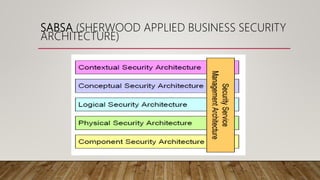
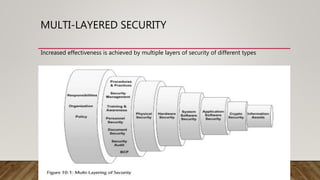
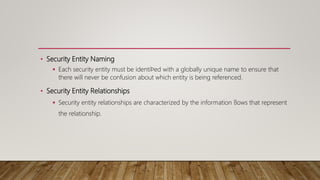
This document provides an overview of conceptual security architecture using the SABSA framework. It describes key concepts like security architecture, enterprise frameworks, control objectives, multi-layered security strategies, security entity models, security domains, and security lifetimes and deadlines. The goal is to conceptualize security at a high level to address business risks and requirements through control objectives and a multi-layered approach using concepts like entities, domains, and relationships of trust.