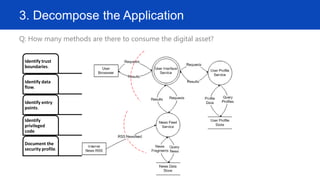
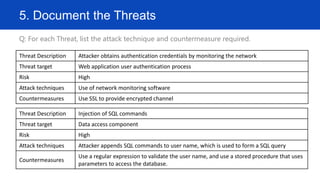
The document outlines a seven-step approach to threat modeling, focusing on identifying assets, creating architectural overviews, decomposing applications, identifying and documenting threats, rating them, and generating work item reports. It utilizes the STRIDE model for threat identification and the DREAD model for threat rating, emphasizing the importance of countermeasures and prioritizing threats for mitigation. The document also includes examples of potential threats and countermeasures, such as SQL injection and credential monitoring.