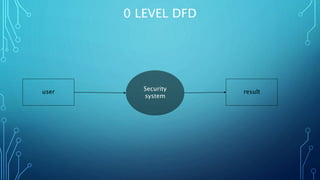
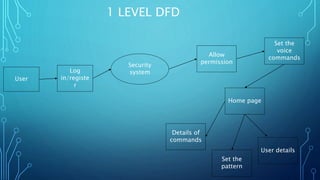
This document presents a voice recognition security system project. The project uses speech recognition to allow a user to control their Android phone through voice commands even if their hands are unavailable. It aims to keep users safe by recognizing their voice and taking actions. Key features include emergency calling, real-time location sharing, camera snapshots, and low data usage. The project is developed using Python, Kivy framework, OpenCV, and speech recognition libraries. It analyzes voice commands using hidden Markov models and accesses the microphone via PyAudio.