This document outlines an industrial training report on ethical hacking conducted at Alison Online Training Institute. It begins with an introduction to ethical hacking and the different types of hacking. It then discusses the role of security and penetration testers and different penetration testing methodologies. The document provides an overview of what can and cannot be done legally as an ethical hacker. It also discusses the basics of networking and what it takes to be a successful security tester.




![6
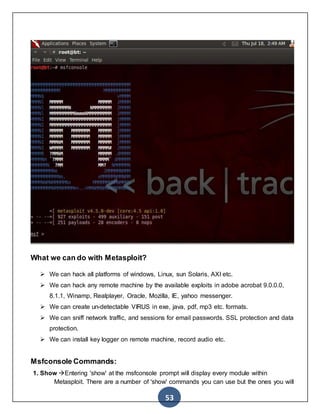
INDUSTRIAL OVERVIEW
Alison is one of the world’s largest free learning platforms for education and skills training. It is
a for-profit social enterprise dedicated to making it possible for anyone, to study anything,
anywhere, at any time, for free online, at any subject level. Through our mission we are a catalyst
for positive social change, creating opportunity, prosperity, and equality for everyone.
Alison was founded in Galway, Ireland, in 2007 and has grown organically to become a major
force in free online education and skills training. Today, with more than 18 million learners in 195
countries, Alison is changing how the world learns and up-skills.
We are committed to equality and access to education and skills training irrespective of gender,
geography, economic status or any other barriers that can so often stunt potential. So we offer
a range of free courses that meet the many diverse needs of our learners. The UN declared in
Article 26 of the 1946 Declaration of Human Rights that “Education shall be free…”. This
statement will always inspire us.
Alison was founded by Alison CEO, Mike Feerick. Mike is a businessman, but one with a
difference. He believes in social impact, and that you can build a financially successful business
focused on meeting a huge global social need, making education and skills training more
accessible for everyone. He invites anyone who believes that too, to support the Alison mission.
Alison is free of charge to you. But it’s still a business – albeit a socially-focused one. We are a
social enterprise making our money through advertising, merchandise, and the sale of
Certificates and Diplomas, should a graduate choose to buy one.
Alison Learning Centers
For many around the world, online learning is inaccessible. Millions are still without internet
access, need assistance with computers, and advice on how to start and maintain their online
education. Alison Learning Centers [ALCs] are an initiative for directly confronting these
challenges.
At an ALC, those without direct access to online learning, or who need or can benefit from
technical or learning support, can find the facilities, community, and support they need. ALCs
enable learners to study on Alison online as part of a group, to avail of off-line tutor assistance,](https://image.slidesharecdn.com/lucknowinstituteoftechnology-210321184515/85/industrial-training-report-on-Ethical-hacking-6-320.jpg)


![9
Alison is currently accredited by CPD UK Continuing professional development.
https://cpduk.co.uk/directory/profile/capernaum-ltd-alison-com
https://alison.com/about/accreditation
Reception
Alison was among the four winners of the 2010 UNESCO King Hamad bin Isa Al Khalifa Prize,
a Prize for innovation in ICT for Education.] In October 2013, Alison won an award at the World
Innovation Summit for Education held in Qatar. Since 2013 Alison courses have become
generally recognized by many employers, particularly in occupations and disciplines where no
external certification by professional bodies post-graduation exist. It is estimated that currently
over 1.5 million people around the world have an Alison course on their CV.
David Bornstein of The New York Times noted that 'practical skills training is usually
expensive. Initially some observers also predicted the ineffectiveness of the MOOC model in
delivering real educational impact, highlighting the lack of personal interaction with educators
and the high drop-out rate of users with no incentive to commit without any material investment
of their own.](https://image.slidesharecdn.com/lucknowinstituteoftechnology-210321184515/85/industrial-training-report-on-Ethical-hacking-9-320.jpg)















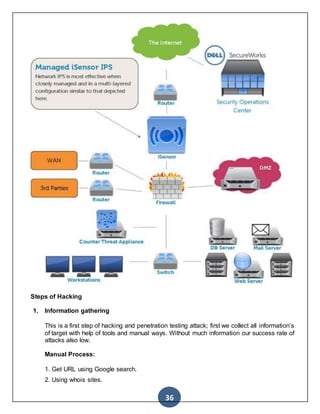
![37
5. www.who.is
6. www.robtex.com
7. www.domaintools.com
3. Get PDF and Document using Google special features:
8. Site:4share.com CISSP
9. Site:pastebin.com inurl:hack
10. Chemistry filetype:doc
11. http://www.googleguide.com/advanced_operators_reference.html
Automated Process:
1. We use following tools for information gathering:
UberHarvest
theharvester.py
Metagoofil
Web Data Extractors (Email-Phone no Extractors)
Maltego
2. People Search:
pipl.com
anywho.com
address.com
Social networking sites (Facebook, LinkedIn, twitter)
Job Sites [ dice.com, monster.com, naukri.com]
3. Phone Number
truecaller.com
kgdetective.com
phunwa.com
4. Trace route Tools
Vtrace [ www.vtrace.pl ]
Trout [ www.foundstone.com ]
tracert , traceroute [ commands ]
5. Email IP Tracking
wspy.org](https://image.slidesharecdn.com/lucknowinstituteoftechnology-210321184515/85/industrial-training-report-on-Ethical-hacking-37-320.jpg)
![38
Emailtrackerpro.com
Readnotify.com
Politemail.com
2. Scanning & Banner Grabbing
After getting information of target user, we need to know OS type, version of application
that are running on open PORTS etc. to successful exploitation
.
Following tools, we need to use:
1. Port & network scanning:
Port and networking scanning is used to know open port and active Pc in network.
Nmap
Angry IP scanner
Hping
2. Banner Grabbing:
Banner grabbing is a process to know exact version of target application to search
loopholes or exploits or zero day.
Telnet
ID serve
3. Vulnerability Scanning
This step is used to find out loopholes in applications using tools, after we use public and
private exploit to enter on target system remotely.
Vulnerability scanner:
Acunetix
Netsparke
Nessus
gfi languard
Whatweb [ Find out web application ][ Backtrack Tool ]
E.g.: ./whatweb bytec0de.com
zoomscan [ scan zoomla website ] [ /pentest/web/zoomscan ]
E.g.: ./joomscan.pl -u http://liclanka.com/
Nikto:
E.g. ./nikto.pl -host liclanka.com
Websecurifi](https://image.slidesharecdn.com/lucknowinstituteoftechnology-210321184515/85/industrial-training-report-on-Ethical-hacking-38-320.jpg)

![40
Dos & DDos Attacks
1. Dos Attack:
A "denial-of-service" attack is characterized by an explicit attempt by attackers to prevent
legitimate users of a service from using that service. Examples include
attempts to "flood" a network, thereby preventing legitimate network traffic
attempts to disrupt connections between two machines, thereby preventing
access to a service
attempts to prevent a particular individual from accessing a service
attempts to disrupt service to a specific system or person
It is an attempt to make a machine or network resource unavailable to its intended users.
Consuming all resources given to person. Like Network bandwidth, all Type of Memory etc.
1. Ping of Death
ping -t -l 6550 google.com [ max buffer size = 65500 ]
Effective system [ Solaris 2.4 , minix , win3.11,95 ]
2. SYN-ATTACK
Hping -i sudo hping3 -i u1 -S -p 80 192.168.1.1
3. UDP/HTTP/TCP Flooding
LOIC
HOIC
4. Smurf Attack](https://image.slidesharecdn.com/lucknowinstituteoftechnology-210321184515/85/industrial-training-report-on-Ethical-hacking-40-320.jpg)
![41
make your own packet and flood on network
pktbuilder
packETH 1.6 (linux & windows)
5. CDP Flooding (Cisco Discovery Protocol)
yersinia [ backtrack ]
Done on Cisco Switches & Routers
6. MAC Flooding
Flooding network switches
ARP Spoofing
Net cut [ Windows ]
ettercap [ Backtrack ]
Deauthentication Technique
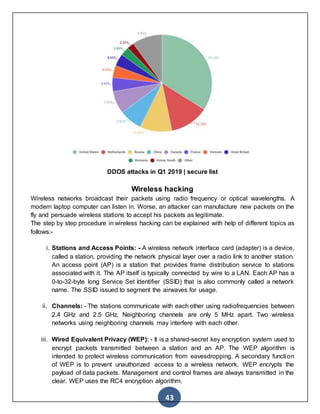
2. Ddos Attack
DDOS, short for Distributed Denial of Service, is a type of DOS attack where multiple
compromised systems -- which are usually infected with a Trojan – are used to target a single
system causing a Denial of Service (DoS) attack. Victims of a DDoS attack consist of both the
end targeted system and all systems maliciously used and controlled by the hacker in the
distributed attack.
According to this report on e-Security Planet, in a DDoS attack, the incoming traffic flooding the
victim originates from many different sources – potentially hundreds of thousands or more. This
effectively makes it impossible to stop the attack simply by blocking a single IP address; plus, it
is very difficult to distinguish legitimate user traffic from attack traffic when spread across so
many points of origin.
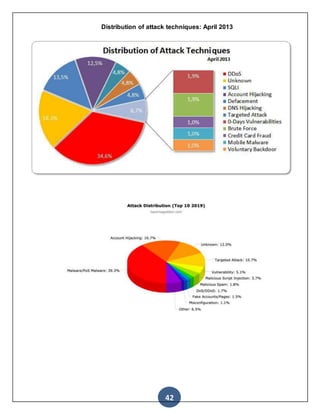
Distribution of attack techniques: January 2013](https://image.slidesharecdn.com/lucknowinstituteoftechnology-210321184515/85/industrial-training-report-on-Ethical-hacking-41-320.jpg)