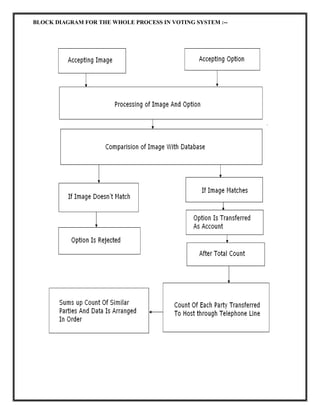
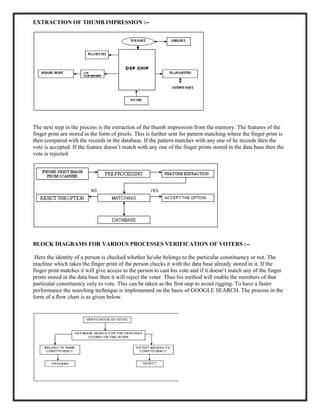
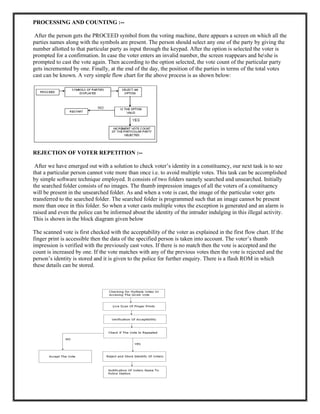
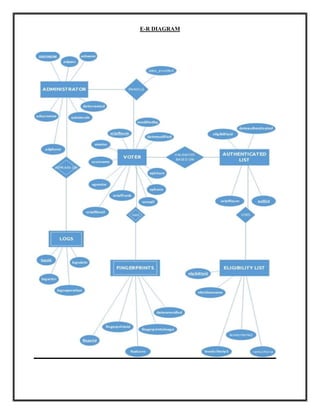
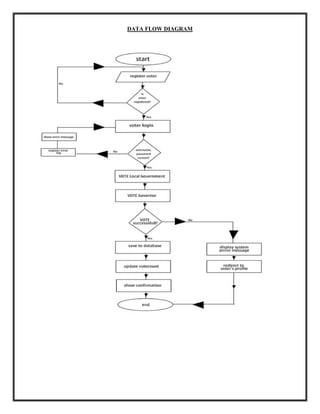
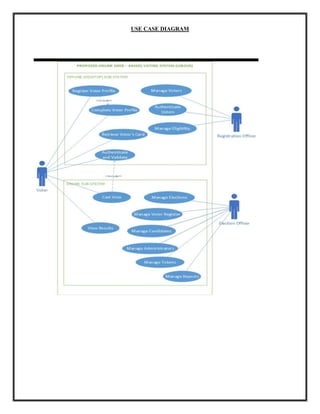
The document summarizes the design of a biometric-based online voting system. It discusses including voter secrecy, authentication, vote verification and accuracy. The design goals are to safely transfer votes from the user's computer to the server and securely store cast votes. The system will use fingerprint biometrics for voter verification and only allow each verified voter to cast one vote. It will also provide manuals for voters before the election and allow vote verification before finalizing.