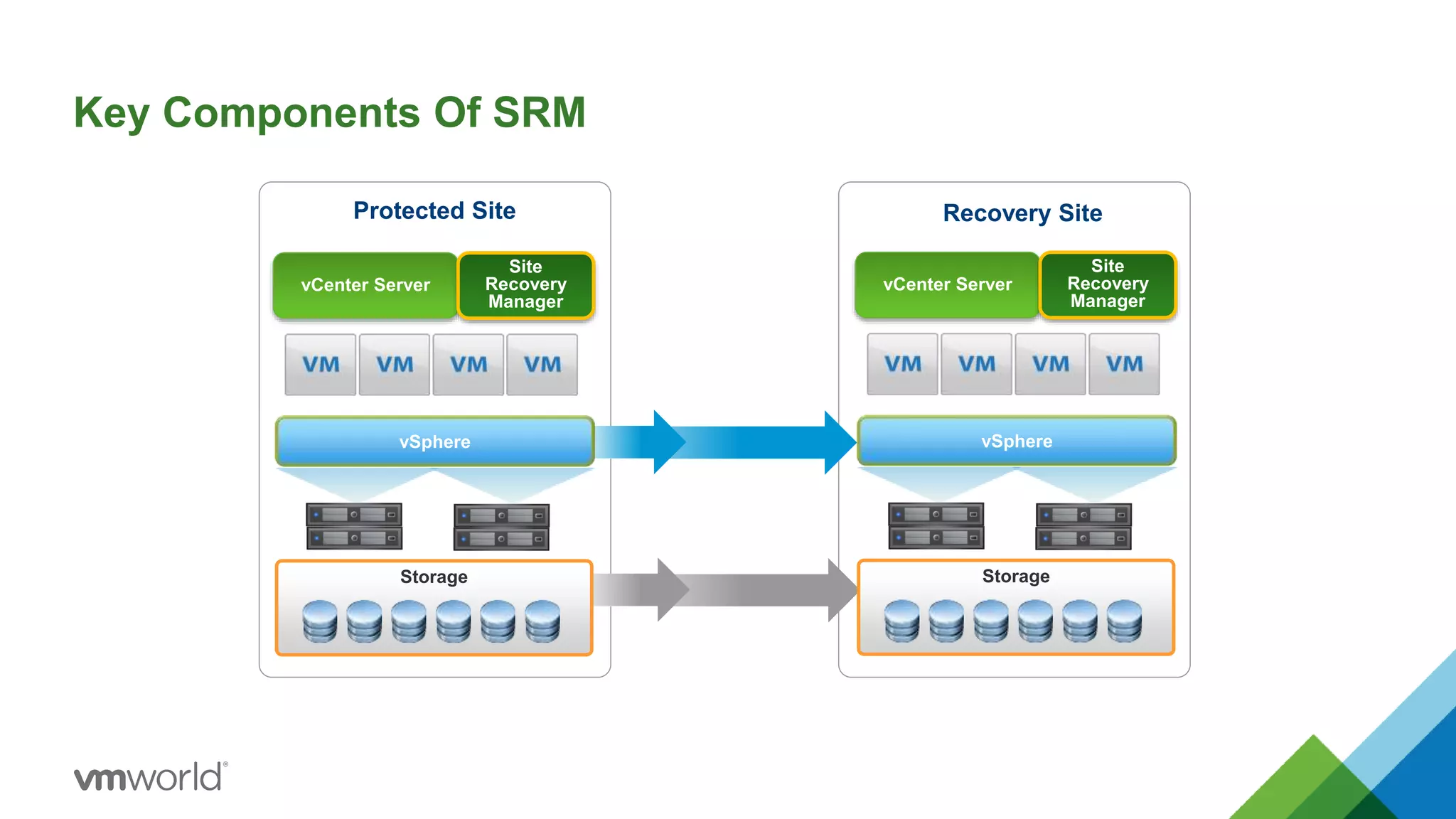
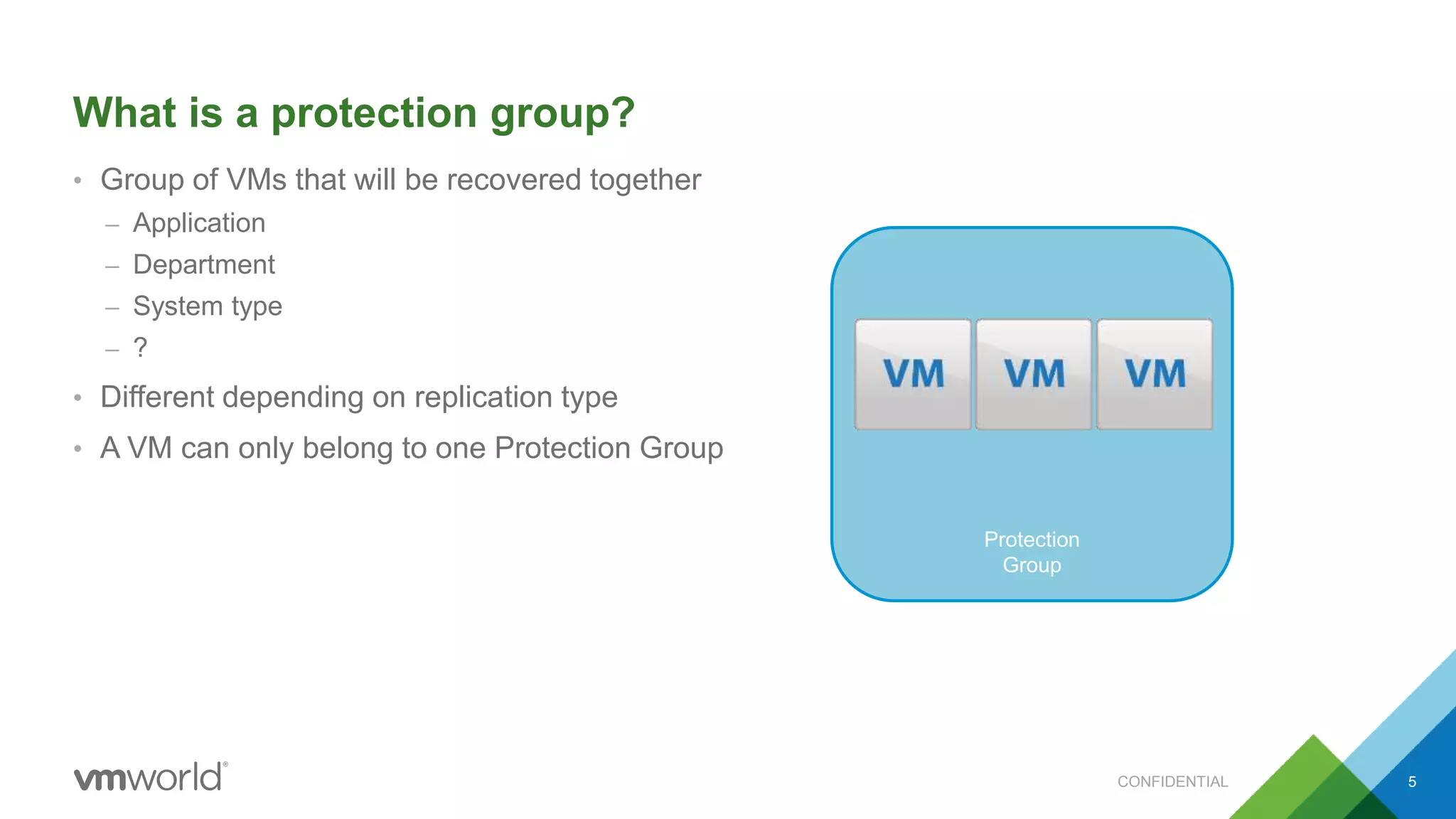
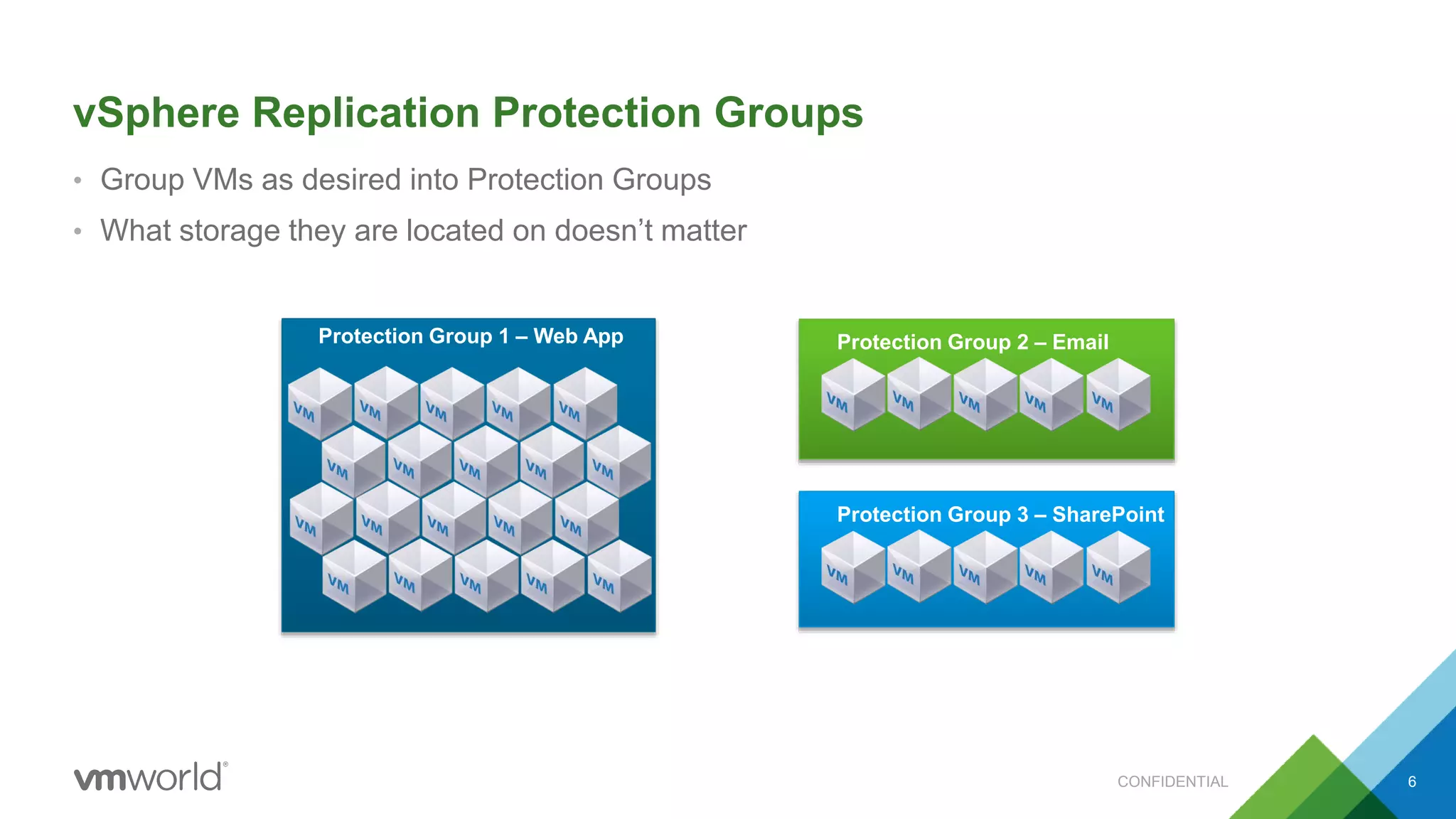
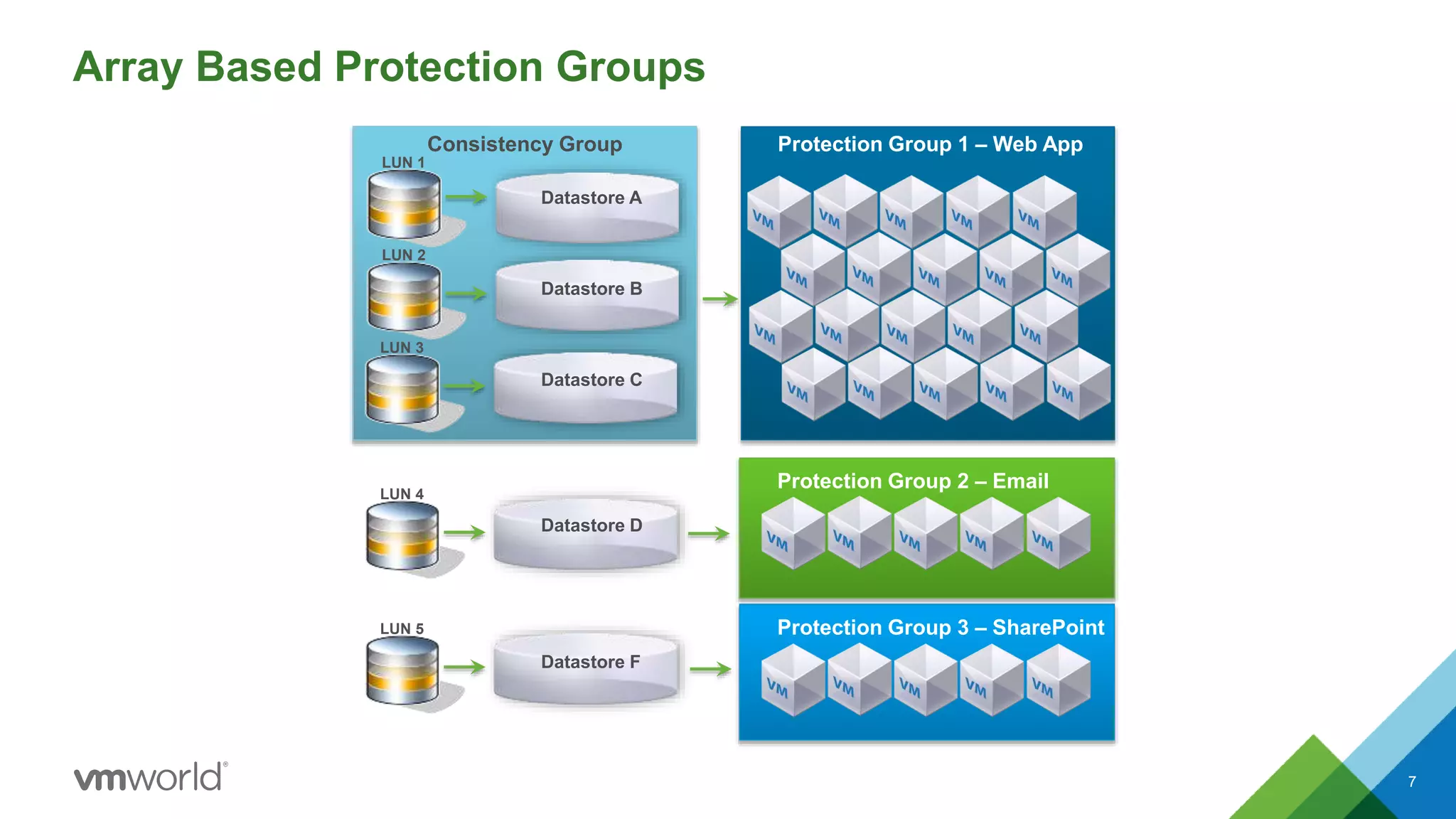
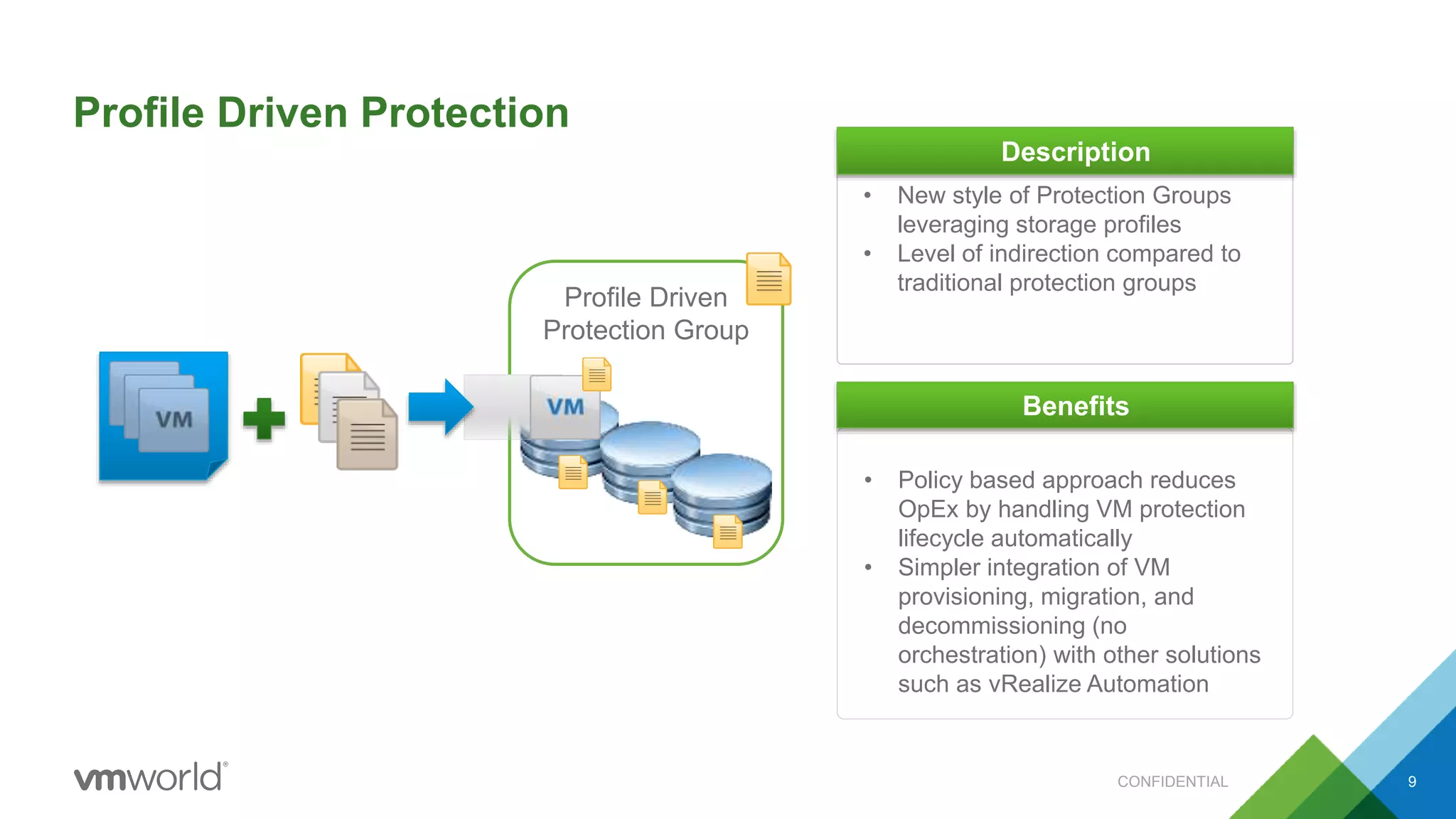
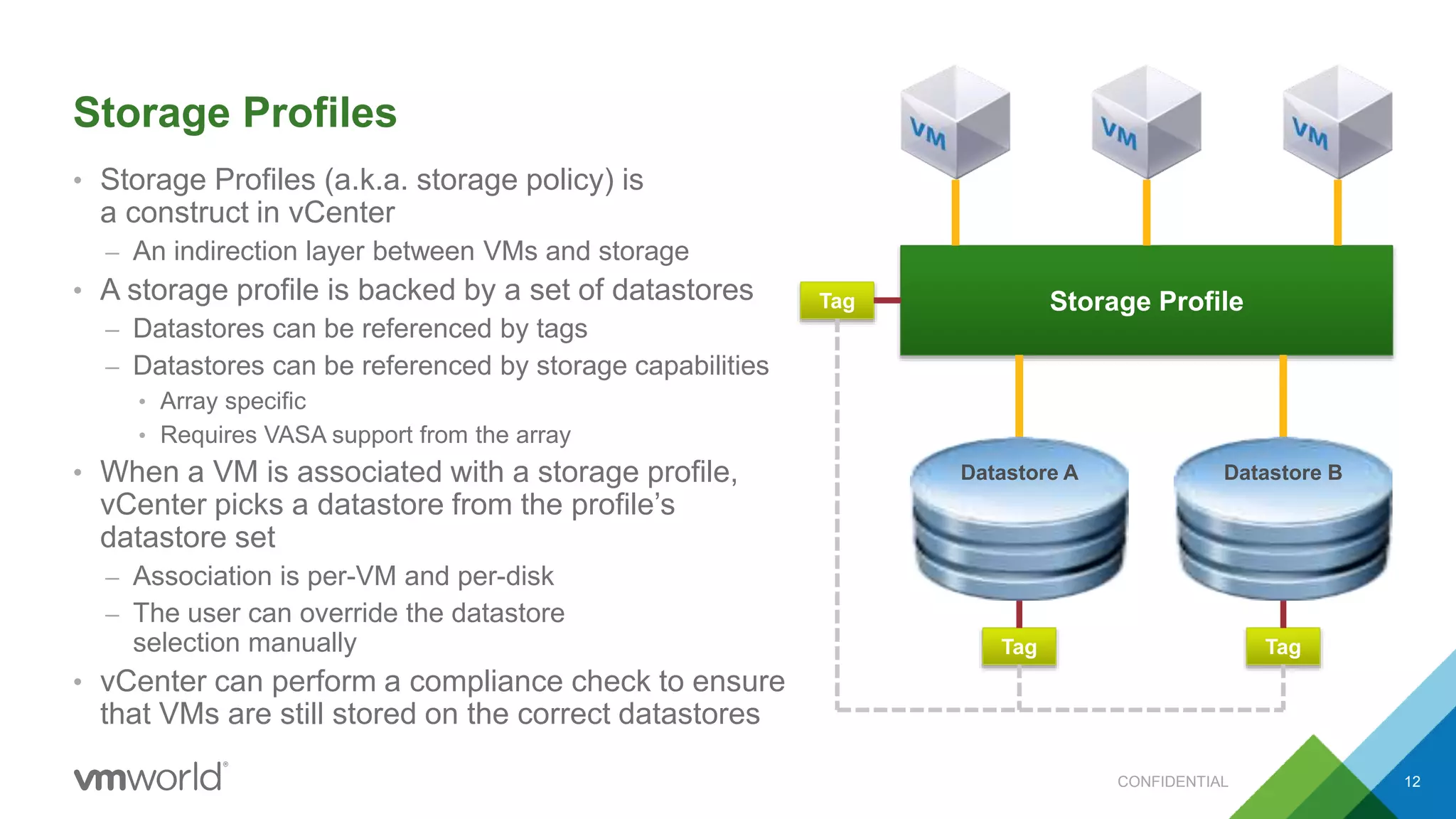
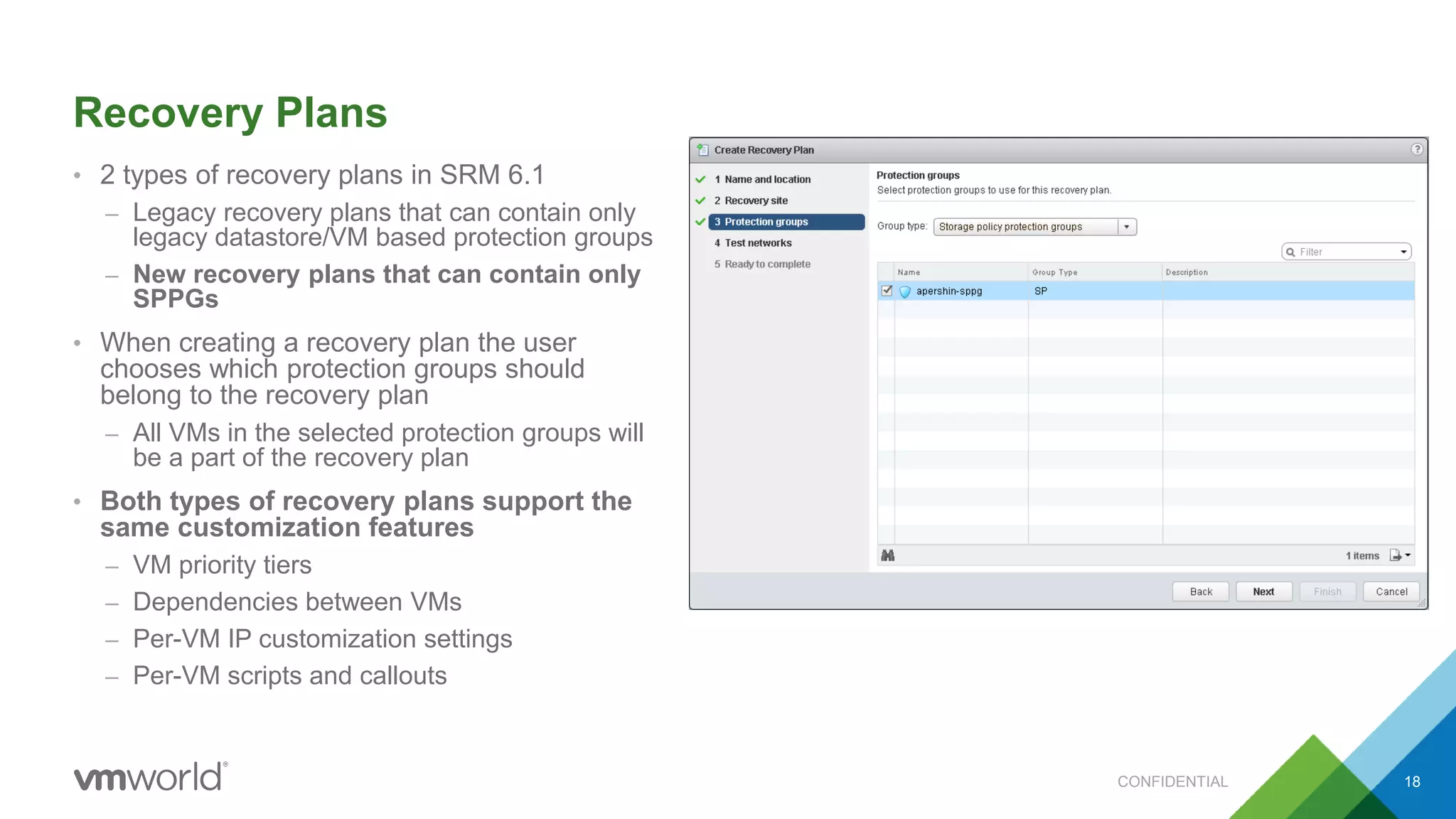
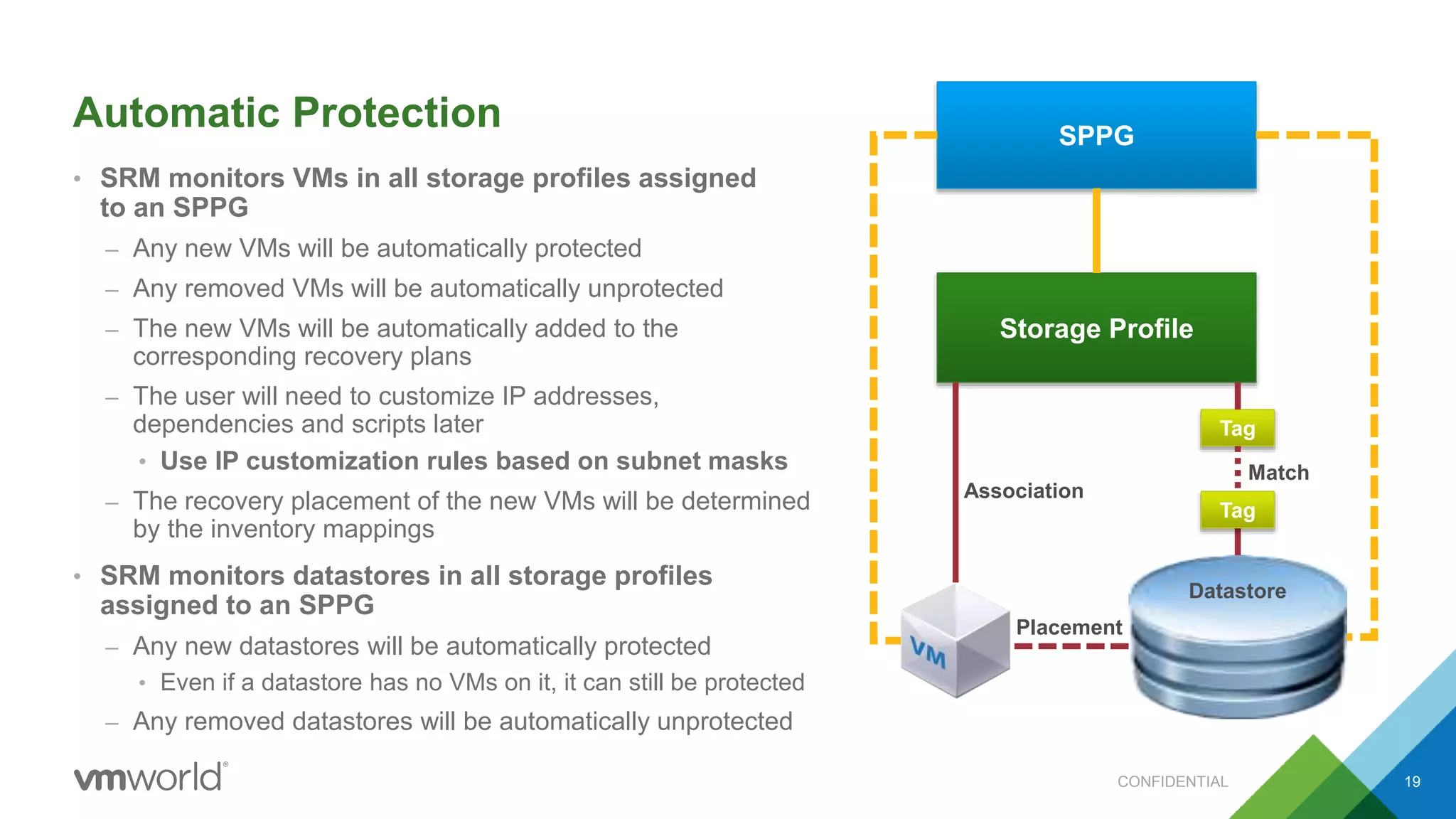
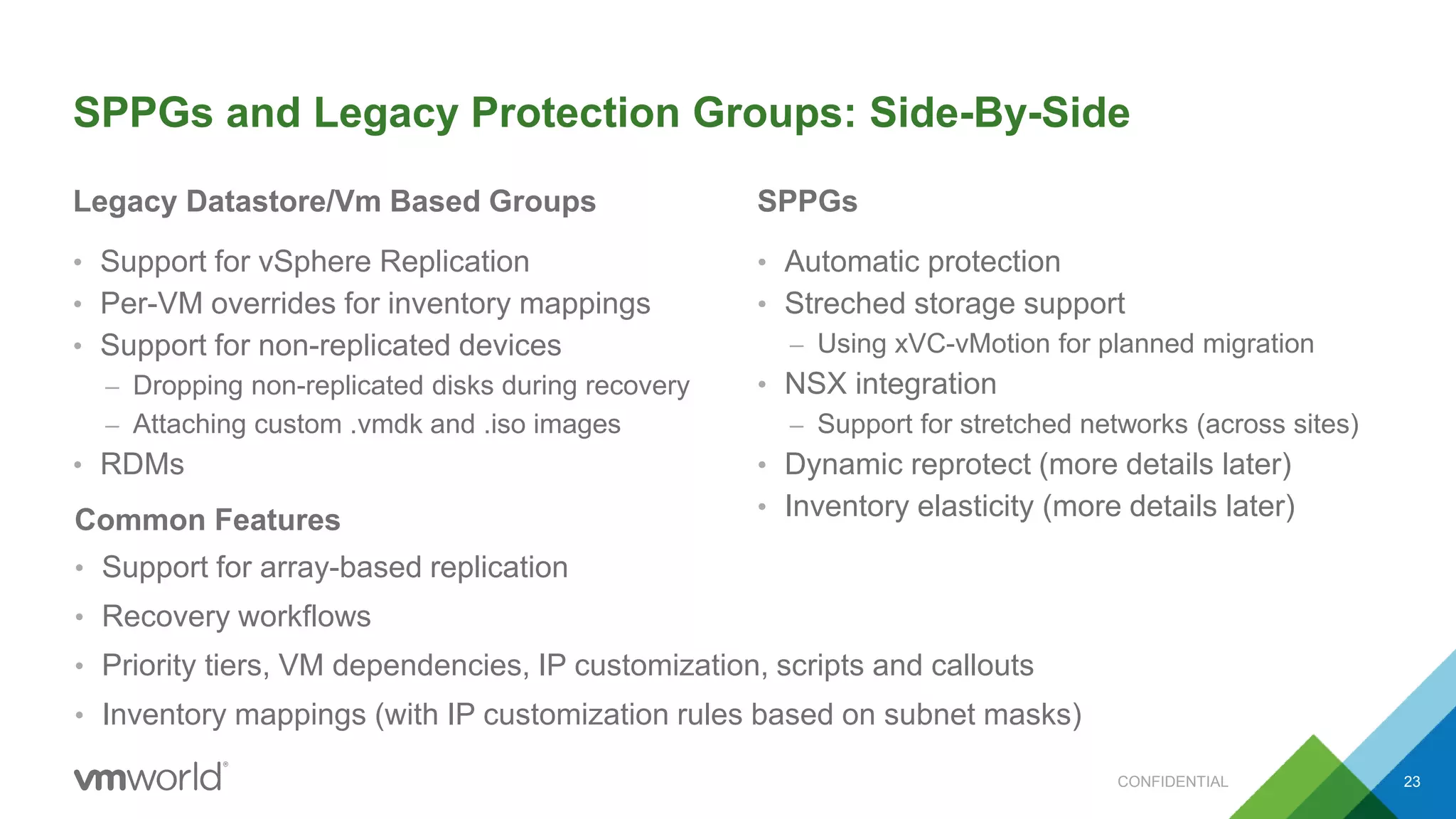
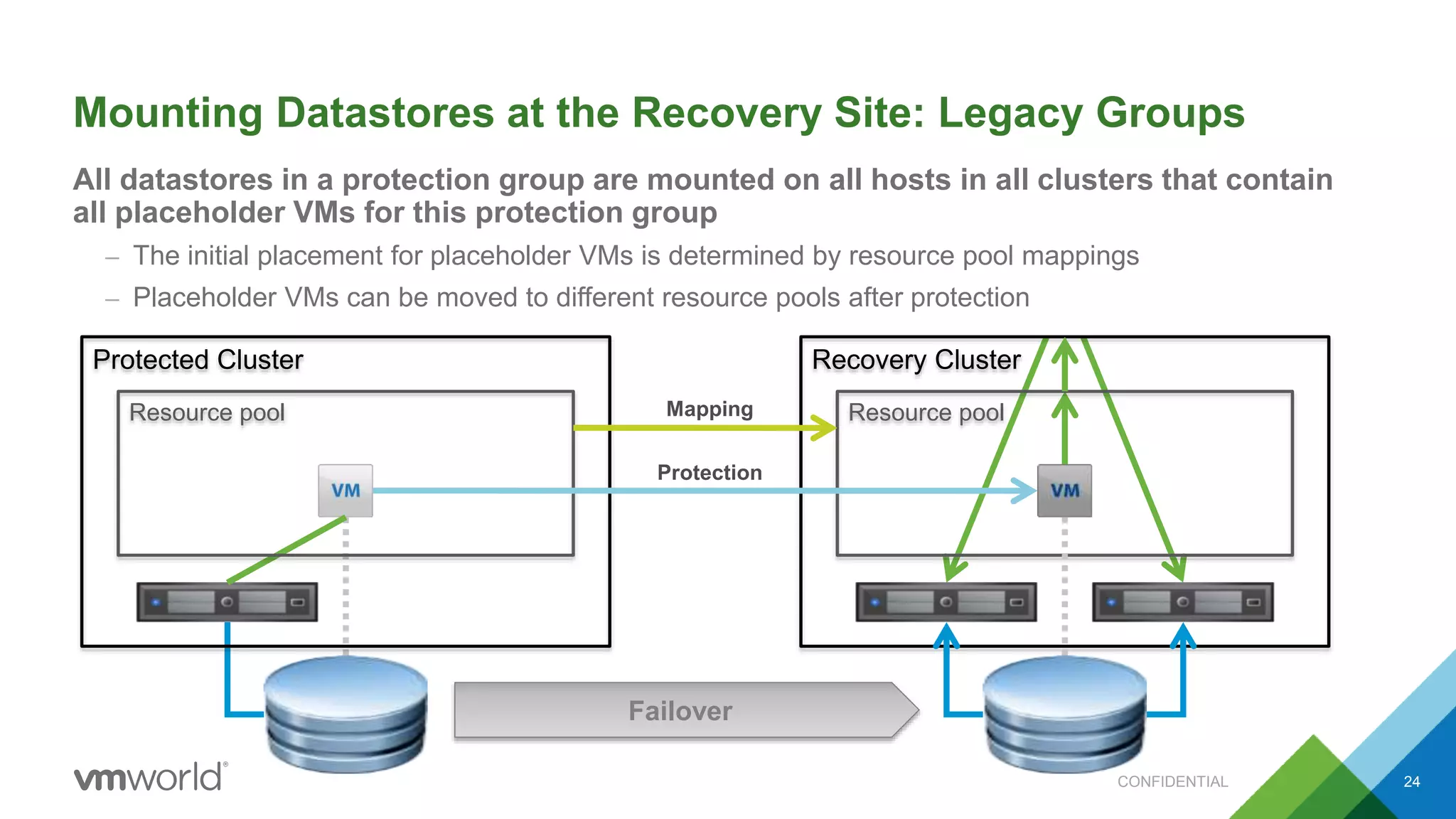
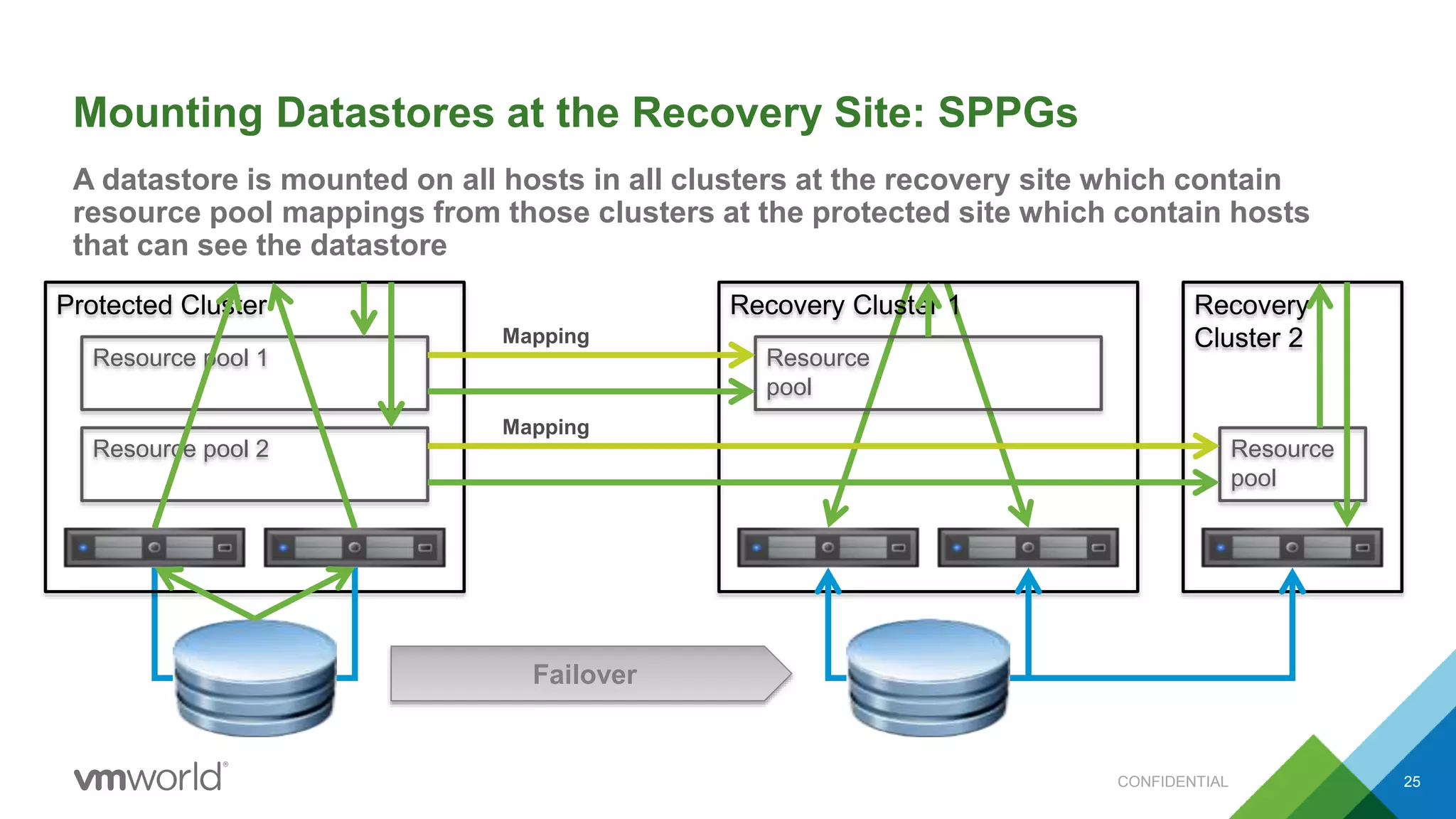
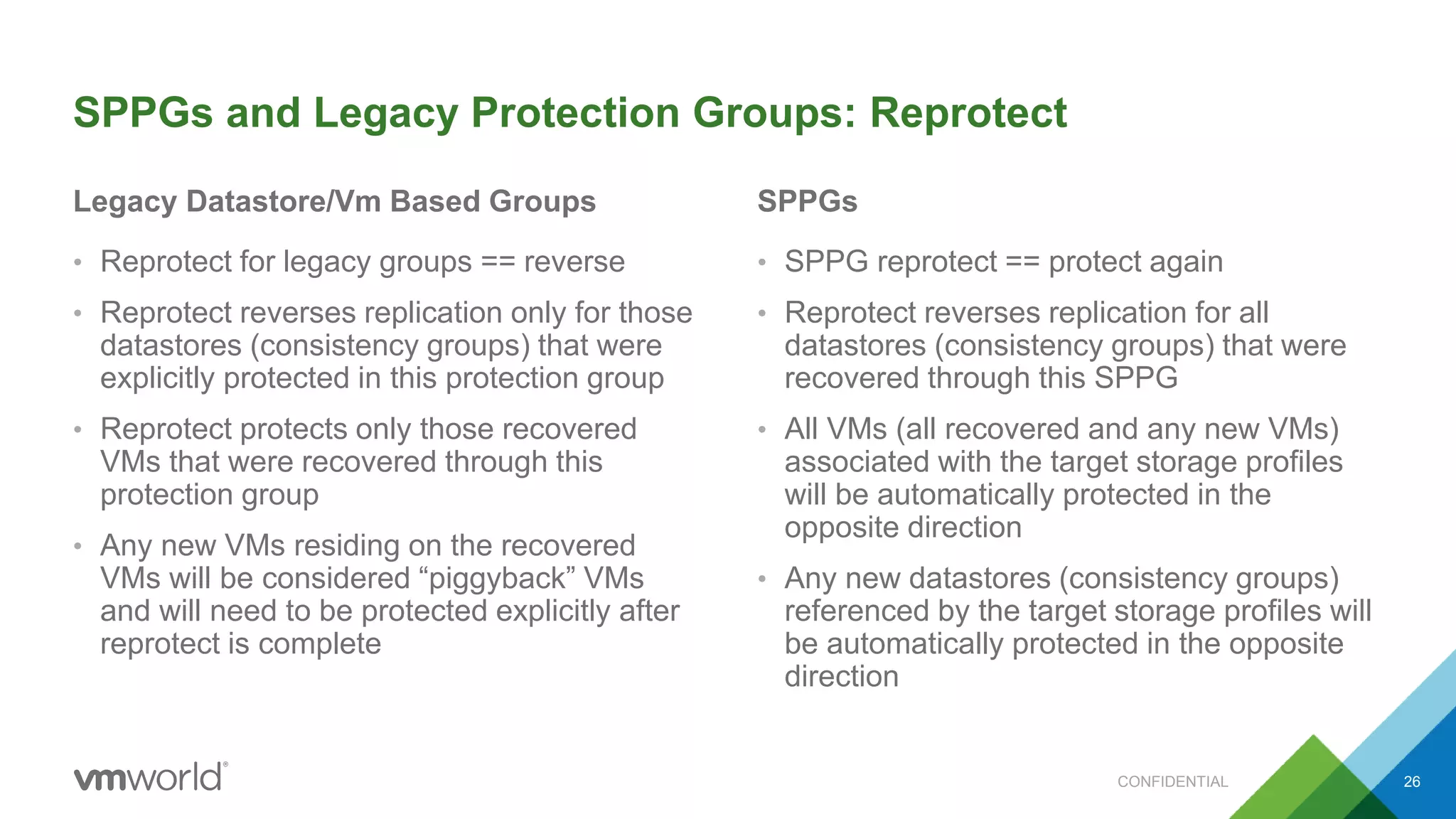
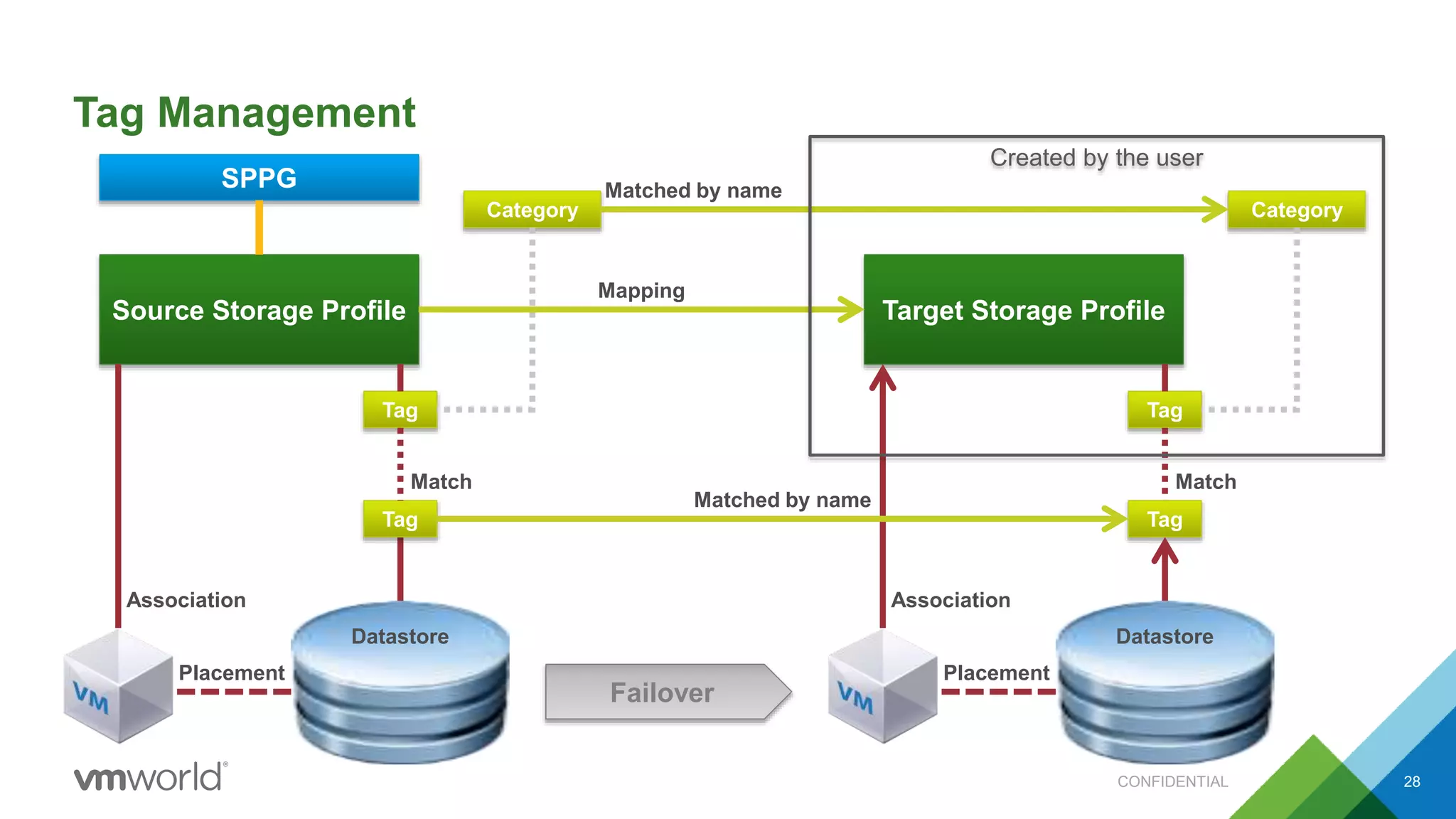
The presentation discusses VMware's Site Recovery Manager (SRM) 6.1, focusing on new features like storage profile-based protection groups (SPPGs) that automate disaster recovery and simplify management. It highlights the integration of stretched storage and NSX, while also addressing the operational benefits and cost reductions associated with these new features. Additionally, it covers the mechanisms for monitoring and automatic protection of virtual machines and datastores.