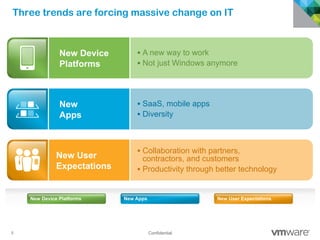
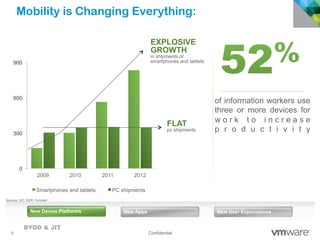
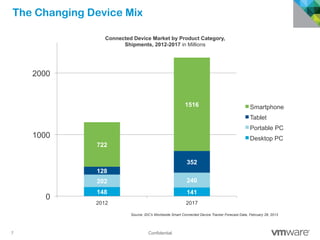
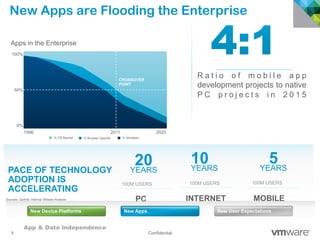
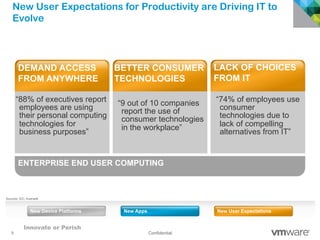
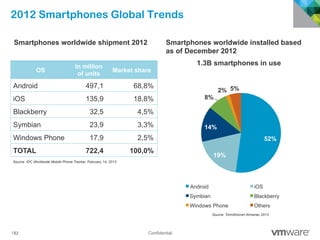
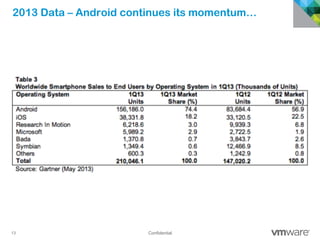
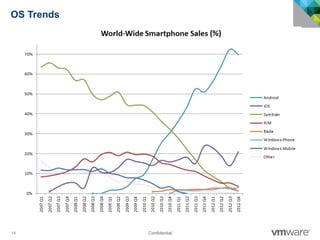
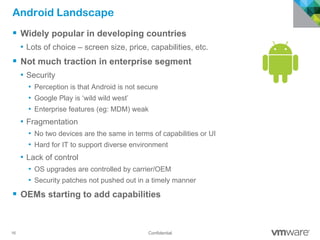
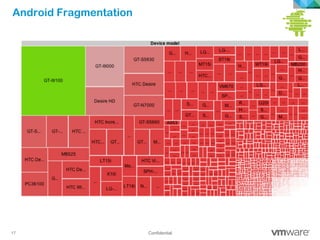
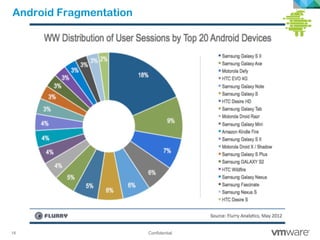
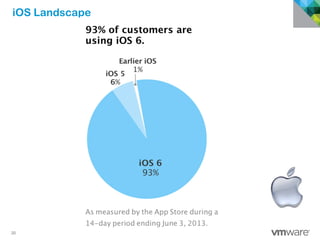
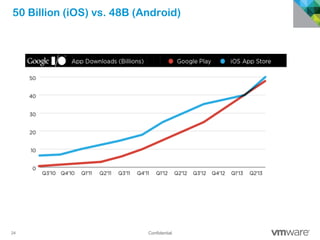
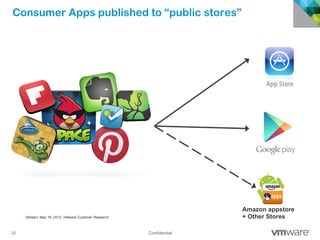
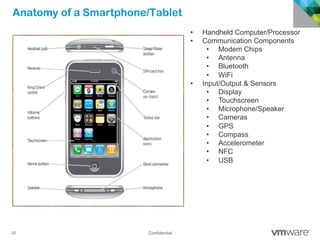
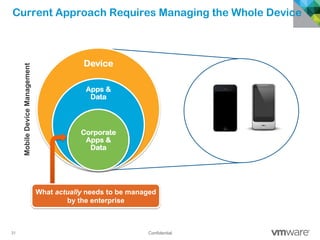
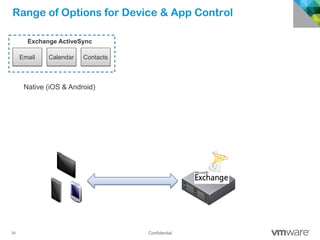
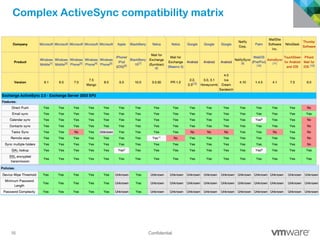
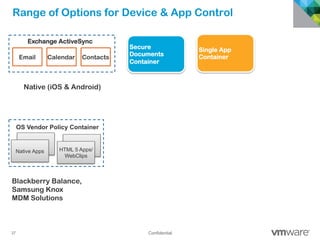
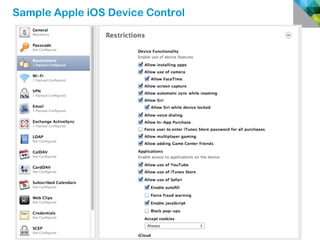
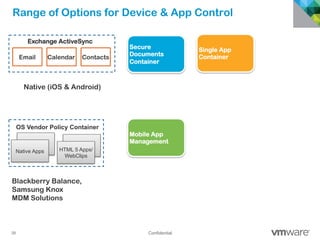
The document discusses how mobile computing is impacting IT and driving massive changes. It notes that new device platforms like smartphones and tablets, new apps, and new user expectations are forcing changes. Specifically, there is now explosive growth in mobile devices, new types of apps, demands for access from anywhere, and expectations of better consumer technologies. This is changing how IT needs to deliver business apps and data to users in a secure yet productive way. It examines trends in mobile operating systems like Android and iOS and challenges like fragmentation. It also explores options for managing devices, apps, data and security in this new environment.