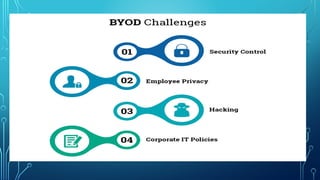
BYOD refers to employees bringing their own devices like smartphones, laptops, and tablets to the workplace. While it can increase productivity and flexibility, it also poses security risks if not properly managed. Key challenges include supporting a variety of devices and operating systems, managing costs, and protecting corporate data and networks. Successful BYOD programs, like Intel's, develop access controls, security tools, and register employee devices to enhance user experience while maintaining security. Companies must address factors like which devices and platforms to allow, inventory management, virtualization, and data protection when deciding whether to implement BYOD.