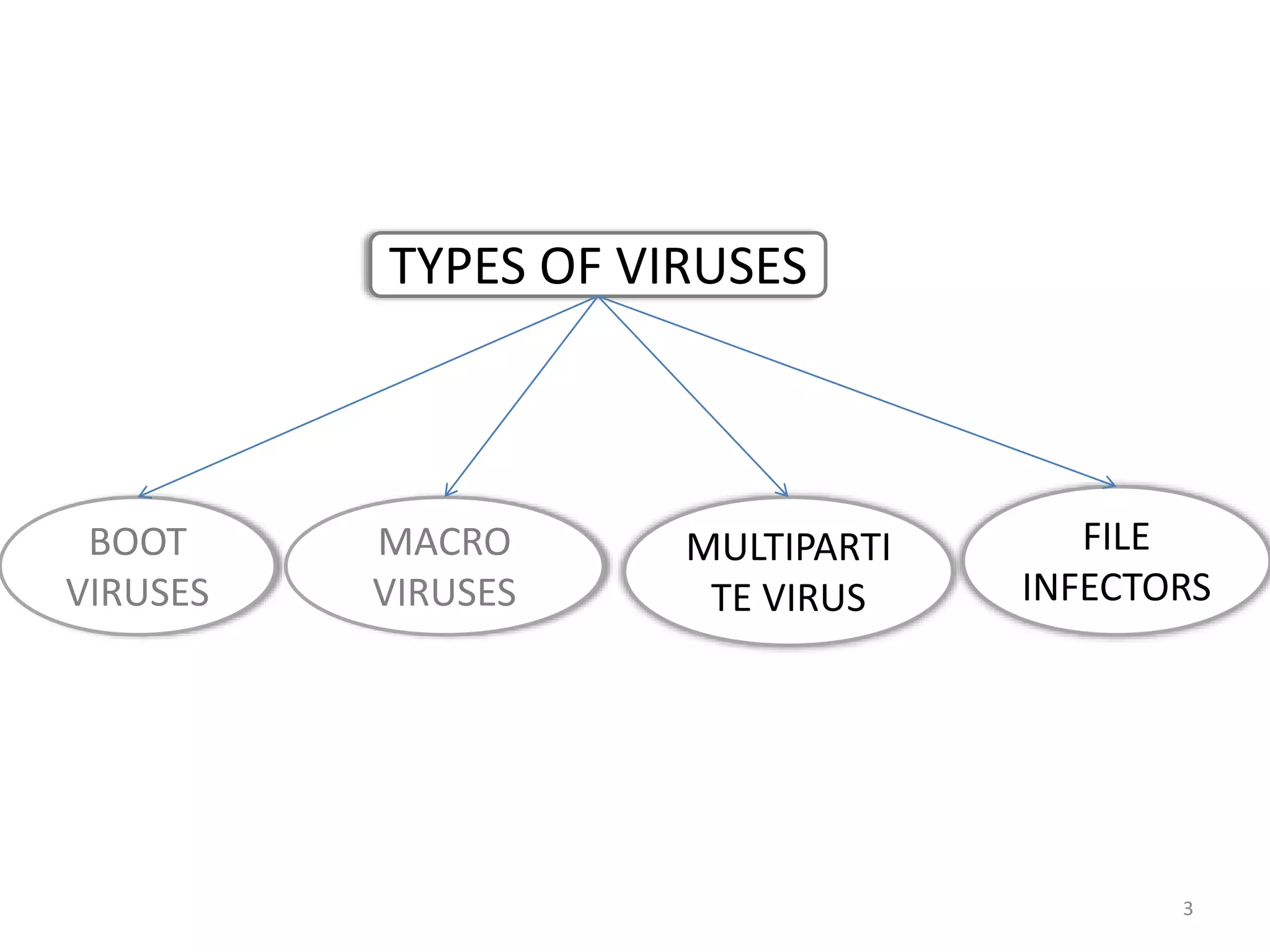
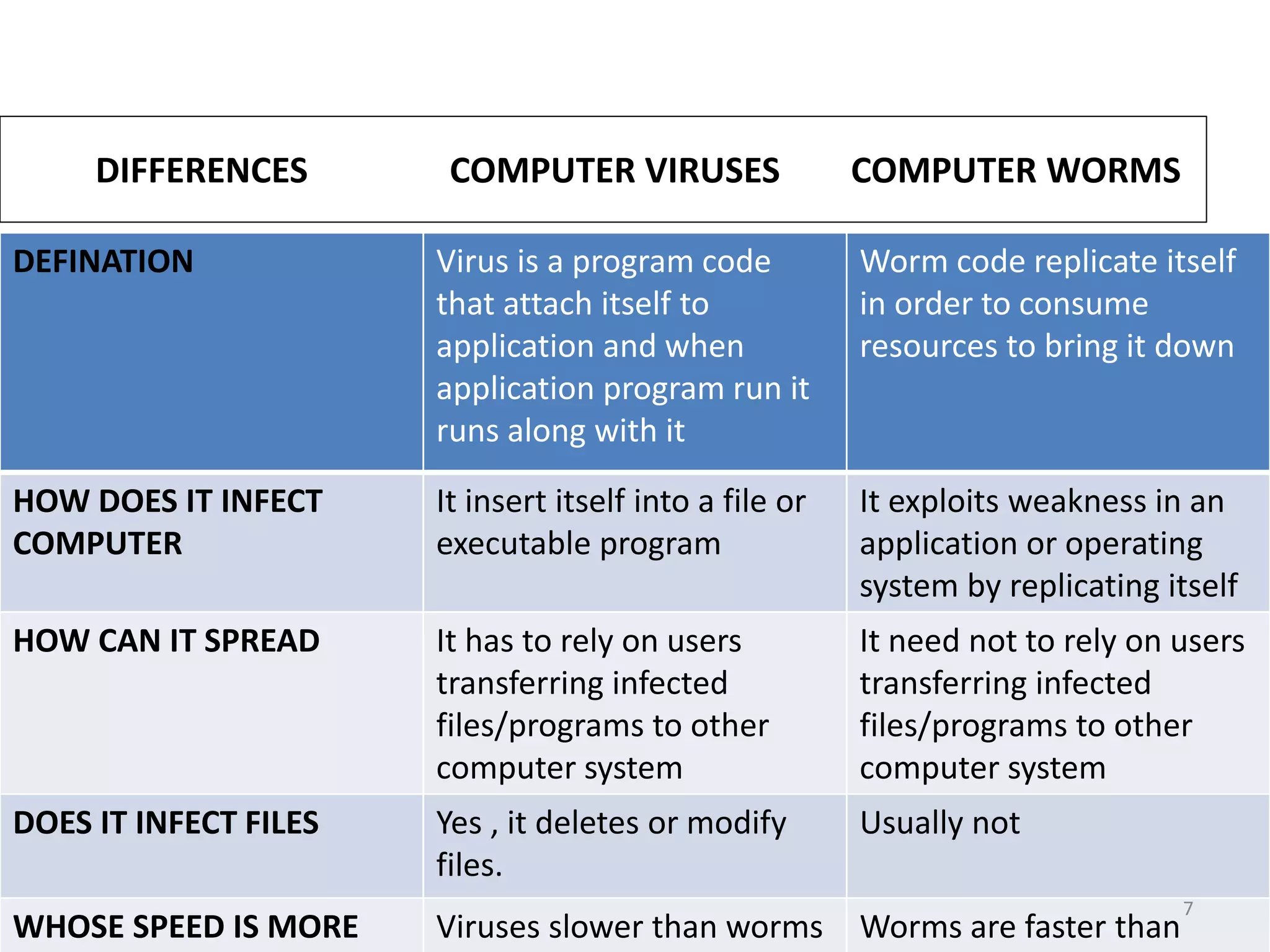
Viruses and worms are types of malware, but they differ in how they spread. Viruses require human action by infecting other files or programs when executed, while worms can spread automatically between computers without human involvement by exploiting system vulnerabilities. Worms spread faster than viruses and do not typically infect files, though both can damage systems by deleting or modifying files. Protecting against malware involves keeping systems updated, using antivirus software, avoiding untrusted sources, and regularly backing up data.