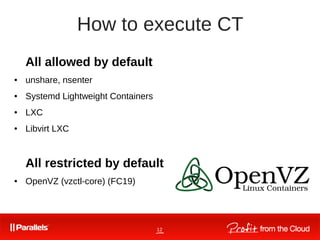
The document discusses virtualization technologies, particularly focusing on Linux containers and OpenVZ. It explains various types of virtualization, the evolution of operating systems, and provides an overview of the Checkpoint/Restore in Userspace (CRIU) functionality. Detailed technical aspects and commands related to container management and process checkpointing are also covered.



![7
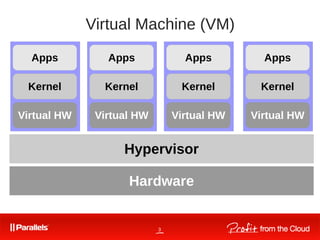
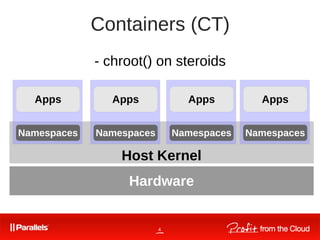
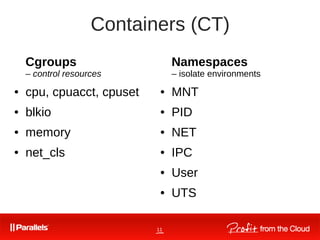
Comparison VM-s vs CT-s
● One real HW, many virtual HW,
many OS-s.
● One real HW, one kernel, many
userspace instances
● Full control on the guest OS ● Native performance: [almost] no
overhead
● High density
● KSM (Kernel SamePage Merging) ● Use resources on demand
● Dynamic resource allocation
● Naturally share pages
● Depends on hardware
(VT-x, VT-d, EPT, etc)
● Not all functionality are virtualized
● Flexibility](https://image.slidesharecdn.com/vagin-linux-containers-150627193009-lva1-app6892/85/2-Vagin-Linux-containers-June-01-2013-6-320.jpg)





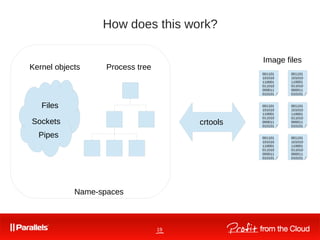
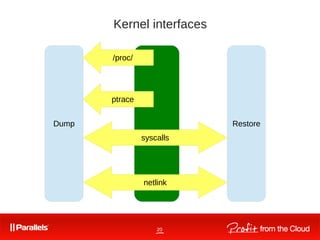
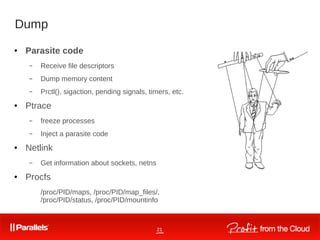
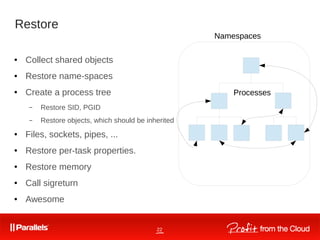
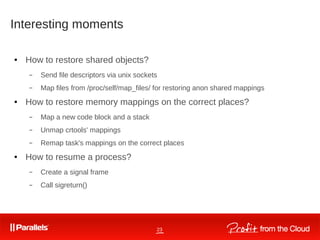





![30
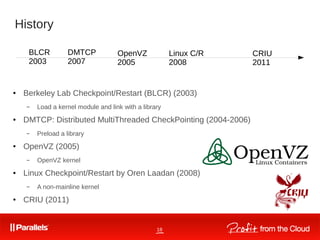
How to use
● ./crtools dump -t pid [<options>]
– checkpoint a process/tree identified by pid
● ./crtools restore -t pid [<options>]
– restore - restore a process/tree identified by pid
● ./crtools show (-D dir)|(-f file) [<options>]
– show dump file(s) contents
● ./crtools check
– checks whether the kernel support is up-to-date
● ./crtools exec -t pid <syscall-string>
– exec - execute a system call by other task](https://image.slidesharecdn.com/vagin-linux-containers-150627193009-lva1-app6892/85/2-Vagin-Linux-containers-June-01-2013-29-320.jpg)

