Virtual Private Network
•
32 likes•4,714 views
A VPN is a private network that uses a public network like the Internet to connect remote sites and users together in a secure way. VPNs use encryption, authentication, and tunneling to securely connect users and sites. VPNs allow companies to extend connectivity globally to remote users and sites in a more cost effective way than traditional private networks, while also providing benefits like data confidentiality, integrity, and simplified network topology. However, VPNs can potentially introduce security risks if not properly configured and monitored.
Report
Share
Report
Share
Recommended
Virtual Private Network

Presented by
Or Sereiparinha
Phan Chhunlong
Student from Panhasastra University of Cambodia (PUC)
VPN (virtual private network) 

A VPN (Virtual Private Network) extends a private network across a public network, such as the
Internet.
A VPN is a network that uses a public telecommunication infrastructure, such as the Internet, to provide
remote offices or individual users with secure access to their organization's network. A VPN ensures
privacy through security procedures and tunneling protocols such as the Layer Two Tunneling Protocol
(L2TP). Data is encrypted at the sending end and decrypted at the receiving end.
Recommended
Virtual Private Network

Presented by
Or Sereiparinha
Phan Chhunlong
Student from Panhasastra University of Cambodia (PUC)
VPN (virtual private network) 

A VPN (Virtual Private Network) extends a private network across a public network, such as the
Internet.
A VPN is a network that uses a public telecommunication infrastructure, such as the Internet, to provide
remote offices or individual users with secure access to their organization's network. A VPN ensures
privacy through security procedures and tunneling protocols such as the Layer Two Tunneling Protocol
(L2TP). Data is encrypted at the sending end and decrypted at the receiving end.
VPN, Its Types,VPN Protocols,Configuration and Benefits

This Presentation About VPN its Types And Configuration and also discuss the Benefits Of VPN.
Virtual Private Network

Virtual Private Network, is defined as a network that uses public network paths but maintains the security and protection of private networks.
Virtual Private Network

A technology that creates a network that is physically public, but virtually private
That is a Secure way of adding an extra level of privacy to your online activity Like web surfing.
Virtual Private Network

A virtual private network gives secure access to LAN resources over a shared network infrastructure such as the internet. It can be conceptualized as creating a tunnel from one location to another, with Encrypted data traveling through the tunnel before being decrypted at its destination.
Virtual Private Network (VPN)

Knowledge Base - Why use a Virtual Private Network (VPN) presented by Devolutions, leader in remote desktop management solutions.
Check out http://remotedesktopmanager.com/
Virtual Private Network(VPN)

Virtual Private Network(VPN).Types of protocol used in VPN and types of VPN
Virtual Private Networks (VPN) ppt

Virtual Private Network is a type of private network that uses public telecommunicaton, such as the Internet, instead of leased lines to communicate
VPN - Virtual Private Network

Overview of VPN protocols.
VPNs (Virtual Private Networks) are often viewed from the perspective of security with the goal of providing authentication and confidentiality.
However, the primary purpose of VPNs is to connect 2 topologically separated private networks over a public network (typically the Internet).
VPNs basically hook a network logically into another network so that both appear as one private local network.
Security is a possible add-on to VPNs. In many cases it makes perfectly sense to secure the VPNs communication over the unsecure public network.
VPN protocols typically employ a tunnel where data packets of the local network are encapsulated in an outer protocol for transmission over the public network.
The most important VPN protocols are IPSec, PPTP and L2TP. In recent years SSL/TLS based VPNs such as OpenVPN have gained widespread adoption.
More Related Content
What's hot
VPN, Its Types,VPN Protocols,Configuration and Benefits

This Presentation About VPN its Types And Configuration and also discuss the Benefits Of VPN.
Virtual Private Network

Virtual Private Network, is defined as a network that uses public network paths but maintains the security and protection of private networks.
Virtual Private Network

A technology that creates a network that is physically public, but virtually private
That is a Secure way of adding an extra level of privacy to your online activity Like web surfing.
Virtual Private Network

A virtual private network gives secure access to LAN resources over a shared network infrastructure such as the internet. It can be conceptualized as creating a tunnel from one location to another, with Encrypted data traveling through the tunnel before being decrypted at its destination.
Virtual Private Network (VPN)

Knowledge Base - Why use a Virtual Private Network (VPN) presented by Devolutions, leader in remote desktop management solutions.
Check out http://remotedesktopmanager.com/
Virtual Private Network(VPN)

Virtual Private Network(VPN).Types of protocol used in VPN and types of VPN
Virtual Private Networks (VPN) ppt

Virtual Private Network is a type of private network that uses public telecommunicaton, such as the Internet, instead of leased lines to communicate
What's hot (20)
VPN, Its Types,VPN Protocols,Configuration and Benefits

VPN, Its Types,VPN Protocols,Configuration and Benefits
Viewers also liked
VPN - Virtual Private Network

Overview of VPN protocols.
VPNs (Virtual Private Networks) are often viewed from the perspective of security with the goal of providing authentication and confidentiality.
However, the primary purpose of VPNs is to connect 2 topologically separated private networks over a public network (typically the Internet).
VPNs basically hook a network logically into another network so that both appear as one private local network.
Security is a possible add-on to VPNs. In many cases it makes perfectly sense to secure the VPNs communication over the unsecure public network.
VPN protocols typically employ a tunnel where data packets of the local network are encapsulated in an outer protocol for transmission over the public network.
The most important VPN protocols are IPSec, PPTP and L2TP. In recent years SSL/TLS based VPNs such as OpenVPN have gained widespread adoption.
Chapter 3: Block Ciphers and the Data Encryption Standard

CRYPTOGRAPHY AND NETWORK SECURITY
PRINCIPLES AND PRACTICE
William Stallings
block ciphers

In cryptography, a block cipher is a deterministic algorithm operating on ... Systems as a means to effectively improve security by combining simple operations such as .... Finally, the cipher should be easily cryptanalyzable, such that it can be ...
Lecture 4 firewalls

Network Security Course (ET1318, ET2437) at Blekinge Institute of Technology, Karlskrona, Sweden
Viewers also liked (16)
Chapter 3: Block Ciphers and the Data Encryption Standard

Chapter 3: Block Ciphers and the Data Encryption Standard
The evolution of mobile technologies 1 g to 4g to lte

The evolution of mobile technologies 1 g to 4g to lte
Similar to Virtual Private Network
Similar to Virtual Private Network (20)
Recently uploaded
From Daily Decisions to Bottom Line: Connecting Product Work to Revenue by VP...

From Daily Decisions to Bottom Line: Connecting Product Work to Revenue by VP of Product, Amplitude
Mission to Decommission: Importance of Decommissioning Products to Increase E...

Mission to Decommission: Importance of Decommissioning Products to Increase Enterprise-Wide Efficiency by VP Data Platform, American Express
Neuro-symbolic is not enough, we need neuro-*semantic*

Neuro-symbolic (NeSy) AI is on the rise. However, simply machine learning on just any symbolic structure is not sufficient to really harvest the gains of NeSy. These will only be gained when the symbolic structures have an actual semantics. I give an operational definition of semantics as “predictable inference”.
All of this illustrated with link prediction over knowledge graphs, but the argument is general.
GraphRAG is All You need? LLM & Knowledge Graph

Guy Korland, CEO and Co-founder of FalkorDB, will review two articles on the integration of language models with knowledge graphs.
1. Unifying Large Language Models and Knowledge Graphs: A Roadmap.
https://arxiv.org/abs/2306.08302
2. Microsoft Research's GraphRAG paper and a review paper on various uses of knowledge graphs:
https://www.microsoft.com/en-us/research/blog/graphrag-unlocking-llm-discovery-on-narrative-private-data/
Smart TV Buyer Insights Survey 2024 by 91mobiles.pdf

91mobiles recently conducted a Smart TV Buyer Insights Survey in which we asked over 3,000 respondents about the TV they own, aspects they look at on a new TV, and their TV buying preferences.
Designing Great Products: The Power of Design and Leadership by Chief Designe...

Designing Great Products: The Power of Design and Leadership by Chief Designer, Beats by Dr Dre
Slack (or Teams) Automation for Bonterra Impact Management (fka Social Soluti...

Sidekick Solutions uses Bonterra Impact Management (fka Social Solutions Apricot) and automation solutions to integrate data for business workflows.
We believe integration and automation are essential to user experience and the promise of efficient work through technology. Automation is the critical ingredient to realizing that full vision. We develop integration products and services for Bonterra Case Management software to support the deployment of automations for a variety of use cases.
This video focuses on the notifications, alerts, and approval requests using Slack for Bonterra Impact Management. The solutions covered in this webinar can also be deployed for Microsoft Teams.
Interested in deploying notification automations for Bonterra Impact Management? Contact us at sales@sidekicksolutionsllc.com to discuss next steps.
Knowledge engineering: from people to machines and back

Keynote at the 21st European Semantic Web Conference
UiPath Test Automation using UiPath Test Suite series, part 4

Welcome to UiPath Test Automation using UiPath Test Suite series part 4. In this session, we will cover Test Manager overview along with SAP heatmap.
The UiPath Test Manager overview with SAP heatmap webinar offers a concise yet comprehensive exploration of the role of a Test Manager within SAP environments, coupled with the utilization of heatmaps for effective testing strategies.
Participants will gain insights into the responsibilities, challenges, and best practices associated with test management in SAP projects. Additionally, the webinar delves into the significance of heatmaps as a visual aid for identifying testing priorities, areas of risk, and resource allocation within SAP landscapes. Through this session, attendees can expect to enhance their understanding of test management principles while learning practical approaches to optimize testing processes in SAP environments using heatmap visualization techniques
What will you get from this session?
1. Insights into SAP testing best practices
2. Heatmap utilization for testing
3. Optimization of testing processes
4. Demo
Topics covered:
Execution from the test manager
Orchestrator execution result
Defect reporting
SAP heatmap example with demo
Speaker:
Deepak Rai, Automation Practice Lead, Boundaryless Group and UiPath MVP
Bits & Pixels using AI for Good.........

A whirlwind tour of tech & AI for socio-environmental impact.
Kubernetes & AI - Beauty and the Beast !?! @KCD Istanbul 2024

As AI technology is pushing into IT I was wondering myself, as an “infrastructure container kubernetes guy”, how get this fancy AI technology get managed from an infrastructure operational view? Is it possible to apply our lovely cloud native principals as well? What benefit’s both technologies could bring to each other?
Let me take this questions and provide you a short journey through existing deployment models and use cases for AI software. On practical examples, we discuss what cloud/on-premise strategy we may need for applying it to our own infrastructure to get it to work from an enterprise perspective. I want to give an overview about infrastructure requirements and technologies, what could be beneficial or limiting your AI use cases in an enterprise environment. An interactive Demo will give you some insides, what approaches I got already working for real.
To Graph or Not to Graph Knowledge Graph Architectures and LLMs

Reflecting on new architectures for knowledge based systems in light of generative ai
Key Trends Shaping the Future of Infrastructure.pdf

Keynote at DIGIT West Expo, Glasgow on 29 May 2024.
Cheryl Hung, ochery.com
Sr Director, Infrastructure Ecosystem, Arm.
The key trends across hardware, cloud and open-source; exploring how these areas are likely to mature and develop over the short and long-term, and then considering how organisations can position themselves to adapt and thrive.
Transcript: Selling digital books in 2024: Insights from industry leaders - T...

The publishing industry has been selling digital audiobooks and ebooks for over a decade and has found its groove. What’s changed? What has stayed the same? Where do we go from here? Join a group of leading sales peers from across the industry for a conversation about the lessons learned since the popularization of digital books, best practices, digital book supply chain management, and more.
Link to video recording: https://bnctechforum.ca/sessions/selling-digital-books-in-2024-insights-from-industry-leaders/
Presented by BookNet Canada on May 28, 2024, with support from the Department of Canadian Heritage.
Generating a custom Ruby SDK for your web service or Rails API using Smithy

Have you ever wanted a Ruby client API to communicate with your web service? Smithy is a protocol-agnostic language for defining services and SDKs. Smithy Ruby is an implementation of Smithy that generates a Ruby SDK using a Smithy model. In this talk, we will explore Smithy and Smithy Ruby to learn how to generate custom feature-rich SDKs that can communicate with any web service, such as a Rails JSON API.
JMeter webinar - integration with InfluxDB and Grafana

Watch this recorded webinar about real-time monitoring of application performance. See how to integrate Apache JMeter, the open-source leader in performance testing, with InfluxDB, the open-source time-series database, and Grafana, the open-source analytics and visualization application.
In this webinar, we will review the benefits of leveraging InfluxDB and Grafana when executing load tests and demonstrate how these tools are used to visualize performance metrics.
Length: 30 minutes
Session Overview
-------------------------------------------
During this webinar, we will cover the following topics while demonstrating the integrations of JMeter, InfluxDB and Grafana:
- What out-of-the-box solutions are available for real-time monitoring JMeter tests?
- What are the benefits of integrating InfluxDB and Grafana into the load testing stack?
- Which features are provided by Grafana?
- Demonstration of InfluxDB and Grafana using a practice web application
To view the webinar recording, go to:
https://www.rttsweb.com/jmeter-integration-webinar
Builder.ai Founder Sachin Dev Duggal's Strategic Approach to Create an Innova...

In today's fast-changing business world, Companies that adapt and embrace new ideas often need help to keep up with the competition. However, fostering a culture of innovation takes much work. It takes vision, leadership and willingness to take risks in the right proportion. Sachin Dev Duggal, co-founder of Builder.ai, has perfected the art of this balance, creating a company culture where creativity and growth are nurtured at each stage.
Recently uploaded (20)
From Daily Decisions to Bottom Line: Connecting Product Work to Revenue by VP...

From Daily Decisions to Bottom Line: Connecting Product Work to Revenue by VP...
Mission to Decommission: Importance of Decommissioning Products to Increase E...

Mission to Decommission: Importance of Decommissioning Products to Increase E...
Neuro-symbolic is not enough, we need neuro-*semantic*

Neuro-symbolic is not enough, we need neuro-*semantic*
Smart TV Buyer Insights Survey 2024 by 91mobiles.pdf

Smart TV Buyer Insights Survey 2024 by 91mobiles.pdf
Designing Great Products: The Power of Design and Leadership by Chief Designe...

Designing Great Products: The Power of Design and Leadership by Chief Designe...
Slack (or Teams) Automation for Bonterra Impact Management (fka Social Soluti...

Slack (or Teams) Automation for Bonterra Impact Management (fka Social Soluti...
Knowledge engineering: from people to machines and back

Knowledge engineering: from people to machines and back
UiPath Test Automation using UiPath Test Suite series, part 4

UiPath Test Automation using UiPath Test Suite series, part 4
Kubernetes & AI - Beauty and the Beast !?! @KCD Istanbul 2024

Kubernetes & AI - Beauty and the Beast !?! @KCD Istanbul 2024
To Graph or Not to Graph Knowledge Graph Architectures and LLMs

To Graph or Not to Graph Knowledge Graph Architectures and LLMs
Key Trends Shaping the Future of Infrastructure.pdf

Key Trends Shaping the Future of Infrastructure.pdf
Transcript: Selling digital books in 2024: Insights from industry leaders - T...

Transcript: Selling digital books in 2024: Insights from industry leaders - T...
Generating a custom Ruby SDK for your web service or Rails API using Smithy

Generating a custom Ruby SDK for your web service or Rails API using Smithy
JMeter webinar - integration with InfluxDB and Grafana

JMeter webinar - integration with InfluxDB and Grafana
Builder.ai Founder Sachin Dev Duggal's Strategic Approach to Create an Innova...

Builder.ai Founder Sachin Dev Duggal's Strategic Approach to Create an Innova...
Virtual Private Network
- 2. Flow of presentation Defining VPN Characteristics Types of VPN VPN Technologies Benefits of VPN Tradeoffs in VPN
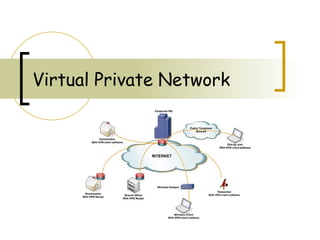
- 3. What is VPN? A VPN is a private network that uses a public network (usually the Internet) to connect remote sites or users together.
- 6. User VPN Remote vpn client Internet Tunnel formation Two way communication Vpn gateway Organization n User−to−LAN connection used by a company that has employees who need to connect to the private network from various remote locations.
- 7. Site VPN Internet Tunnel formation Two way communication Vpn gateway Organization n Remote site Through the use of dedicated equipment and large-scale encryption, a company can connect multiple fixed sites over a public network such as the Internet. Each site needs only a local connection to the same public network
- 8. User and site vpn connection
- 11. Tradeoffs of VPN internet Internal network User computer Vpn channel Trojan horse sends traffic to internal n over VPN Vpn Server Attacker communicates with the trojan horse via the internet TCPP stack VPN s Trojan horse
- 12. Submitted by- Ashish Goel Shippi chandak Sujata Shreya Tanu venus