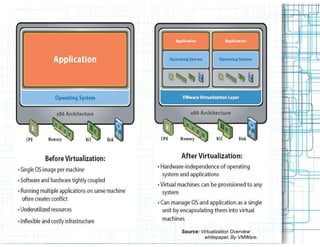
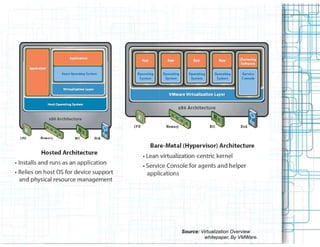
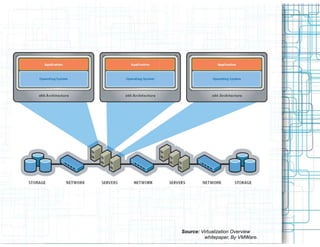
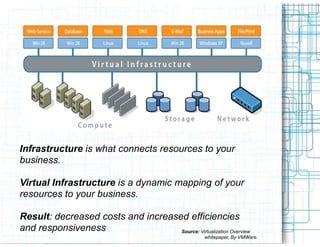
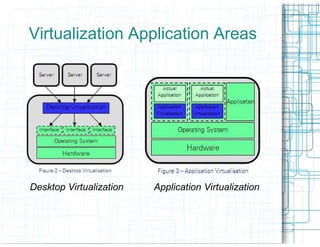
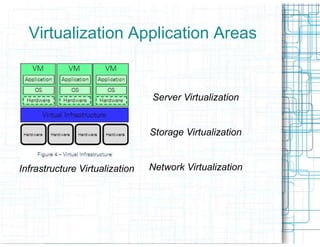
Virtualization allows multiple operating systems to run on a single physical system by sharing hardware resources. It provides isolation between virtual machines using a virtual machine monitor. Virtualization provides benefits like server consolidation, running legacy applications, sandboxing, and business continuity. However, it also presents risks if not properly secured, such as increased attack channels, insecure communications between virtual machines, and virtual machine sprawl consuming excess resources. Security measures are needed at the hypervisor, host, virtual machine, and network layers to harden the virtualization environment against threats.