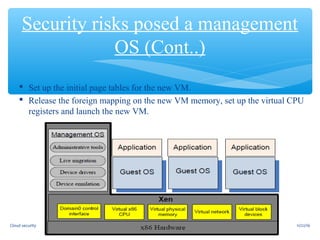
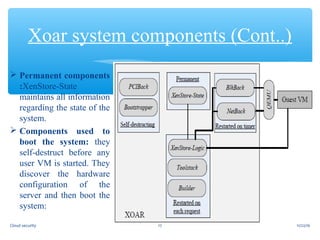
This document discusses cloud security risks and provides an overview of cloud security. It outlines various security risks in cloud computing including insider and outsider attacks, privacy and trust issues, and vulnerabilities in operating systems, virtualization, and shared images. It also describes the Xoar system for improving security by reducing the trusted computing base and limiting privileges and interfaces of system components. Finally, it discusses the need for a trusted virtual machine monitor to prevent the cloud provider from accessing the system.