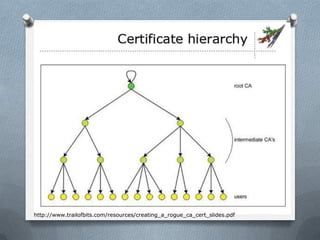
The document discusses various aspects of SSL/TLS security, highlighting the risks of SSL attacks and the importance of authenticity in secure communication. It addresses vulnerabilities such as the BEAST attack, issues with certificate authorities, and the significance of certificate revocation lists. Additionally, it outlines the implications of attacks against the public key infrastructure and mentions specific incidents of CA hacks that compromised numerous certificates.