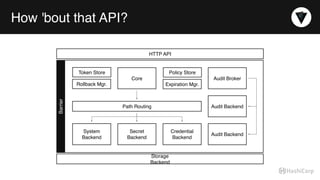
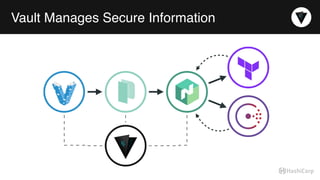
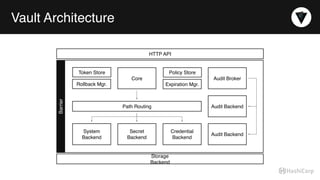
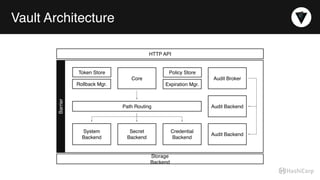
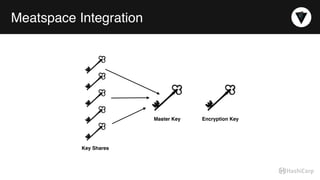
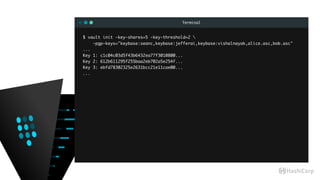
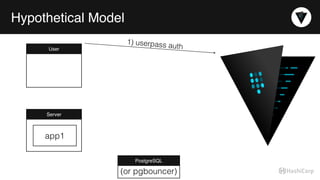
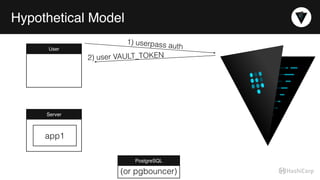
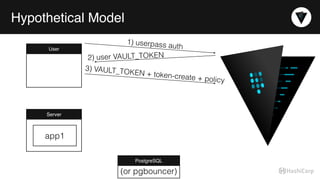
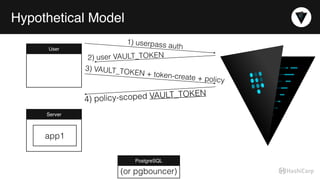
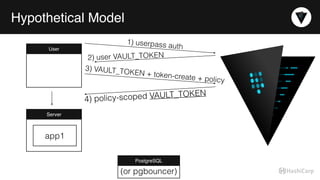
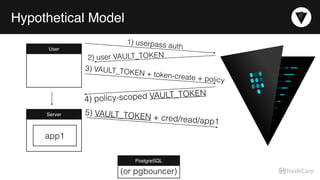
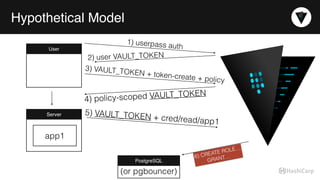
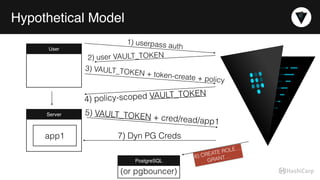
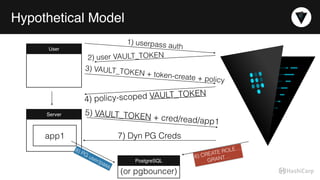
The document discusses the management of dynamic database credentials using HashiCorp's Vault, focusing on security best practices and the architecture behind it. Key elements include centralizing key management, automating security measures, and implementing role-based access controls to mitigate risks associated with leaked secrets. It also highlights the advantages of using Vault for managing database credentials, such as PostgreSQL, through processes that ensure secure interactions and auditing capabilities.


















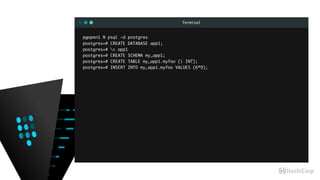
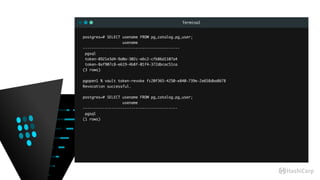
![Terminal
pgopen1 % vault mount postgresql
Successfully mounted 'postgresql' at 'postgresql'!
pgopen1 % vault path-help postgresql/ | head -8
## DESCRIPTION
The PostgreSQL backend dynamically generates database users.
After mounting this backend, configure it using the endpoints within
the "config/" path.
## PATHS
pgopen1 % vault path-help postgresql/ | grep /
the "config/" path.
^config/connection$
^config/lease$
^creds/(?P<name>w[w-.]+w)$
^roles/(?P<name>w[w-.]+w)$
^roles/?$](https://image.slidesharecdn.com/dynamiccredentials-160914172523/85/Dynamic-Database-Credentials-Security-Contingency-Planning-46-320.jpg)
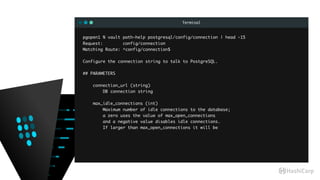
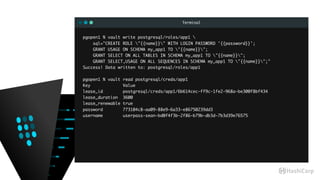
![Terminal
pgopen1 % vault read postgresql/creds/app1
Key Value
lease_id postgresql/creds/app1/6b614cec-ff9c-1fe2-968a-be300f8bf434
lease_duration 3600
lease_renewable true
password 773104c8-aa09-88e9-6a33-e86750239dd3
username userpass-sean-bd0f4f3b-2f86-b79b-db3d-7b3d39e76575
pgopen1 % psql -q -d app1
app1=# x
app1=# dn+
List of schemas
-[ RECORD 1 ]-----+-------------------------------------------------------------
Name | my_app1
Owner | pgsql
Access privileges | pgsql=UC/pgsql +
| "userpass-sean-bd0f4f3b-2f86-b79b-db3d-7b3d39e76575"=U/pgsql
Description |](https://image.slidesharecdn.com/dynamiccredentials-160914172523/85/Dynamic-Database-Credentials-Security-Contingency-Planning-51-320.jpg)
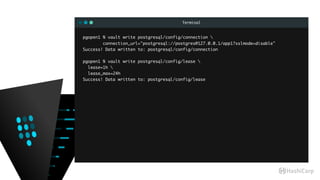
![Terminal
pgopen1 % psql -q -d app1
app1=# x
app1=# dn+
List of schemas
-[ RECORD 1 ]-----+-------------------------------------------------------------
Name | my_app1
Owner | pgsql
Access privileges | pgsql=UC/pgsql +
| "userpass-sean-bd0f4f3b-2f86-b79b-db3d-7b3d39e76575"=U/pgsql
Description |
app1=# dp+
Access privileges
-[ RECORD 1 ]-----+-------------------------------------------------------------
Schema | my_app1
Name | myfoo
Type | table
Access privileges | pgsql=arwdDxt/pgsql +
| "userpass-sean-bd0f4f3b-2f86-b79b-db3d-7b3d39e76575"=r/pgsql
Column privileges |
Policies |](https://image.slidesharecdn.com/dynamiccredentials-160914172523/85/Dynamic-Database-Credentials-Security-Contingency-Planning-52-320.jpg)
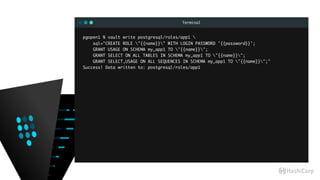
![Terminal
app1=# CREATE ROLE my_app1_web_tier;
app1=# GRANT USAGE ON SCHEMA my_app1 TO my_app1_web_tier;
app1=# GRANT SELECT ON ALL TABLES IN SCHEMA my_app1 TO my_app1_web_tier;
app1=# dp+
Access privileges
-[ RECORD 1 ]-----+-------------------------
Schema | my_app1
Name | myfoo
Type | table
Access privileges | pgsql=arwdDxt/pgsql +
| my_app1_web_tier=r/pgsql
Column privileges |
Policies |](https://image.slidesharecdn.com/dynamiccredentials-160914172523/85/Dynamic-Database-Credentials-Security-Contingency-Planning-53-320.jpg)
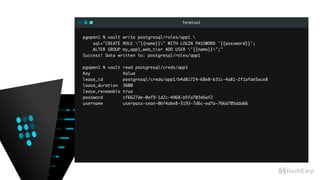
![Terminal
pgopen1 % psql -q -U userpass-sean-0bf4abe8-5193-7d6c-ed7a-766d705dda66 app1
app1=> SET search_path = my_app1;
app1=> dn+
List of schemas
-[ RECORD 1 ]-----+-------------------------------------------------------------
Name | my_app1
Owner | pgsql
Access privileges | pgsql=UC/pgsql +
| "userpass-sean-bd0f4f3b-2f86-b79b-db3d-7b3d39e76575"=U/pgsql+
| my_app1_web_tier=U/pgsql
Description |
app1=> dp+
Access privileges
-[ RECORD 1 ]-----+-------------------------
Schema | my_app1
Name | myfoo
Type | table
Access privileges | pgsql=arwdDxt/pgsql +
| my_app1_web_tier=r/pgsql
Column privileges |
Policies |](https://image.slidesharecdn.com/dynamiccredentials-160914172523/85/Dynamic-Database-Credentials-Security-Contingency-Planning-55-320.jpg)
![Terminal
app1=> SELECT * FROM my_app1.myfoo ;
-[ RECORD 1 ]
i | 1](https://image.slidesharecdn.com/dynamiccredentials-160914172523/85/Dynamic-Database-Credentials-Security-Contingency-Planning-56-320.jpg)
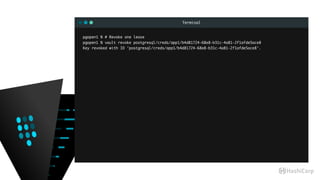
![Terminal
pgopen1 % # Revoke all of postgresql/ ’s leases
pgopen1 % vault revoke -prefix postgresql/creds
app1=# du
List of roles
-[ RECORD 1 ]----------------------------------------------------------
Role name | my_app1_web_tier
Attributes | Cannot login
Member of | {}
-[ RECORD 2 ]----------------------------------------------------------
Role name | pgsql
Attributes | Superuser, Create role, Create DB, Replication, Bypass RLS
Member of | {}](https://image.slidesharecdn.com/dynamiccredentials-160914172523/85/Dynamic-Database-Credentials-Security-Contingency-Planning-58-320.jpg)
![Terminal
pgopen1 % # Create some new creds from a child token
pgopen1 % vault token-create
Key Value
token fc20f365-4250-e840-739e-2e658dba8678
token_accessor 046f5be2-a98d-4608-4398-4c232b3afca2
token_duration 0
token_renewable true
token_policies [root]
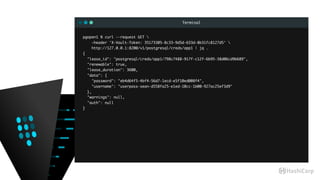
$ env VAULT_TOKEN=fc20f365-4250-e840-739e-2e658dba8678 vault read postgresql/creds/app1
Key Value
lease_id postgresql/creds/app1/d6e01c35-ff11-365f-5bce-d78dbe9fd995
lease_duration 2592000
lease_renewable true
password 2828a500-f813-b785-5d49-0da565de2938
username token-8921e3d4-9a0a-302c-e6c2-cfb86d1107a4
$ env VAULT_TOKEN=fc20f365-4250-e840-739e-2e658dba8678 vault read postgresql/creds/app1
Key Value
lease_id postgresql/creds/app1/7532550e-e5cb-501d-a8e5-3578a71a40c3
lease_duration 2592000
lease_renewable true
password 2a9f3169-c49d-f83f-e0d7-b261c4aadcc9
username token-8ef907c8-e619-4b8f-01f4-372dbcac51ca](https://image.slidesharecdn.com/dynamiccredentials-160914172523/85/Dynamic-Database-Credentials-Security-Contingency-Planning-59-320.jpg)