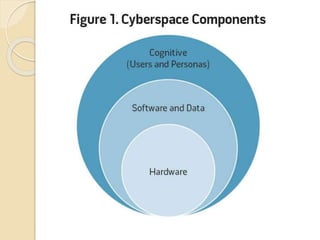
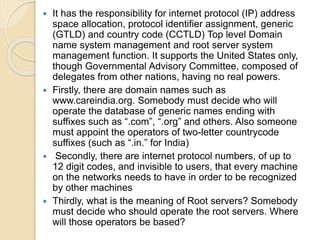
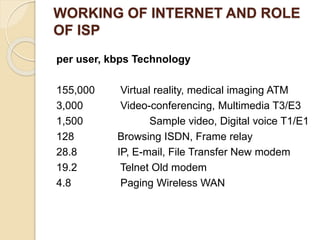
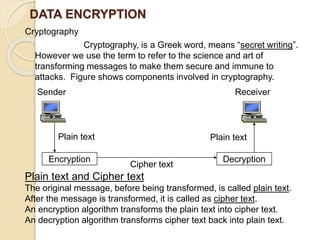
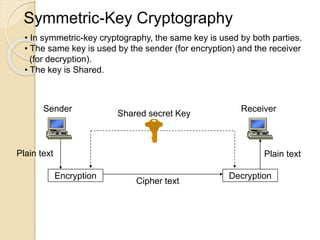
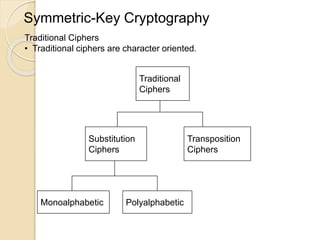
The document provides an overview of cyberspace and cybersecurity, detailing how the internet functions and its historical evolution. It discusses the roles of internet service providers (ISPs), the importance of cybersecurity measures such as data encryption and digital signatures, and the need for a regulatory framework to manage internet ownership. Additionally, it highlights the use of authentication methods and the legal frameworks governing electronic signatures.