Internet(2)
•
2 likes•983 views
The Internet began in the late 1960s as a network developed by the US Department of Defense to allow communication even if parts were damaged. In the 1980s, the NSFNET allowed researchers to share data. Now many networks are connected, forming the global Internet. Computers communicate using TCP/IP protocols. While the Internet provides advantages like email and information access, it also poses disadvantages like security and privacy risks from hacking, viruses, and cookies that can damage data. Organizations like ISOC and IETF work to support and coordinate Internet development and standards.
Report
Share
Report
Share
Recommended
The Internet

The document discusses the key aspects of the Internet including its history, governance, infrastructure, services, social impacts, and security. It provides details on how the Internet originated from early computer networks, who governs and oversees its development, the physical hardware and transmission systems that allow for connectivity, popular online services, both positive and negative social effects, and security threats and solutions.
Software. intranet. e crime

The document discusses computer software, including that software is a series of instructions that allows hardware to operate. It notes John von Neumann developed practical uses of software in 1944, opening the door for further development. Software types include system software like operating systems and application programs, as well as communication, entertainment, utility and education software. Networking links computing devices through hardware and software supporting data communication. Types of networks include LANs, WANs, MANs, SANs, CANs, PANs and DANs. Intranets share information internally limiting access to employees. Benefits include integrating systems and increasing productivity. Firewalls block unwanted internet traffic based on content. Categories include personal, departmental and enterprise firewalls
Internet surfing and security

This document provides an overview of the internet, its history, advantages, disadvantages, and requirements. It discusses how the internet began as ARPANET, a network developed by the US Department of Defense. It describes how the internet allows people to access information from any device anywhere and share emails and files. However, it notes that not all online information is accurate and personal information could be misused. The document also outlines the components needed like a computer, modem, and ISP to connect to the internet along with definitions of search engines, web browsers, and viruses. It emphasizes installing antivirus software and updating it to protect computers from viruses.
E commerce

Unit -1
E-Commerce, Internet, Intranet, advantages and Limitations of Internet, Extranet, Plugins, TCP/IP, Hardware and Software Requirements.
Discuss various ethical issue which may faced by utilizing information techno...

Network Topologies
Topology is a network's virtual shape or structure. This shape does not necessarily correspond to the actual physical layout of the devices on the network. For example, the computers on a home LAN may be arranged in a circle in a family room, but it would be highly unlikely to find a ring topology there.
In computer networking, topology refers to the layout of connected devices. This article introduces the standard topologies of networking.
Network topologies are categorized into the following basic types:
• bus
• ring
• star
• tree
• mesh
More complex networks can be built as hybrids of two or more of the above basic topologies.
Bus Topology
Bus networks (not to be confused with the system bus of a computer) use a common backbone to connect all devices. A single cable, the backbone functions as a shared communication medium that devices attach or tap into with an interface connector. A device wanting to communicate with another device on the network sends a broadcast message onto the wire that all other devices see, but only the intended recipient actually accepts and processes the message.
Bus topologies are relatively easy to install and don't require much cabling compared to the alternatives. Bus networks work best with a limited number of devices. If more than a few dozen computers are added to a network bus, performance problems will likely result. In addition, if the backbone cable fails, the entire network effectively becomes unusable.
Bus Topology Diagram:
Ring Topology
In a ring network, every device has exactly two neighbors for communication purposes. All messages travel through a ring in the same direction (either "clockwise" or "counterclockwise"). A failure in any cable or device breaks the loop and can take down the entire network. To implement a ring network, one typically uses FDDI, SONET, or Token Ring technology. Ring topologies are found in some office buildings or school campuses.
Definition: Token Ring is a data link technology for local area networks (LANs). It operates at layer 2 of the OSI model.
Ring Topology Diagram:
Star Topology
Many home networks use the star topology. A star network features a central connection point called a "hub" that may be a hub, switch or router. Devices typically connect to the hub with Unshielded Twisted Pair (UTP) Ethernet. Compared to the bus topology, a star network generally requires more cable, but a failure in any star network cable will only take down one computer's network access and not the entire LAN. (If the hub fails, however, the entire network also fails.)
Star Topology Diagram:
Chapter 3 Computer Crimes

The document discusses computer and internet crime, including definitions of crime and different types of attacks such as viruses, worms, Trojan horses, denial-of-service attacks, and logic bombs. It also describes different types of perpetrators like hackers, crackers, insiders, industrial spies, cybercriminals, and cyberterrorists. Finally, it outlines some legal issues around fraud and recommendations for reducing internet vulnerabilities through risk assessment, security policies, education, and installing firewalls.
Computer Crimes

This document discusses various legal issues related to computing. It begins by defining different types of cybercrimes such as hacking, cracking, cyber piracy, cyber trespass, and cyber vandalism. It notes that many cybercrimes go unreported due to embarrassment or fears over security practices. The document also discusses the difference between hackers, crackers, white hat and black hat hackers. It considers issues like counter hacking and whether ethical hacking should be allowed. Finally, it examines the need for separate cybercrime laws and defines cyber-exacerbated and cyber-assisted crimes.
Cyber ethics

This document provides an overview of cyber ethics topics including:
- An introduction to cyber ethics and its history dating back to the 1940s.
- The importance of teaching cyber ethics to protect personal information, promote fair competition, and encourage responsible internet use.
- Common cyber ethics issues like copyright infringement, cyberbullying, hacking, and understanding appropriate online behavior.
- Examples of cyber ethics rules and the do's and don'ts of responsible internet use.
- Frequently asked questions about why cyber ethics is important and what the need is for teaching proper cyber ethics.
Recommended
The Internet

The document discusses the key aspects of the Internet including its history, governance, infrastructure, services, social impacts, and security. It provides details on how the Internet originated from early computer networks, who governs and oversees its development, the physical hardware and transmission systems that allow for connectivity, popular online services, both positive and negative social effects, and security threats and solutions.
Software. intranet. e crime

The document discusses computer software, including that software is a series of instructions that allows hardware to operate. It notes John von Neumann developed practical uses of software in 1944, opening the door for further development. Software types include system software like operating systems and application programs, as well as communication, entertainment, utility and education software. Networking links computing devices through hardware and software supporting data communication. Types of networks include LANs, WANs, MANs, SANs, CANs, PANs and DANs. Intranets share information internally limiting access to employees. Benefits include integrating systems and increasing productivity. Firewalls block unwanted internet traffic based on content. Categories include personal, departmental and enterprise firewalls
Internet surfing and security

This document provides an overview of the internet, its history, advantages, disadvantages, and requirements. It discusses how the internet began as ARPANET, a network developed by the US Department of Defense. It describes how the internet allows people to access information from any device anywhere and share emails and files. However, it notes that not all online information is accurate and personal information could be misused. The document also outlines the components needed like a computer, modem, and ISP to connect to the internet along with definitions of search engines, web browsers, and viruses. It emphasizes installing antivirus software and updating it to protect computers from viruses.
E commerce

Unit -1
E-Commerce, Internet, Intranet, advantages and Limitations of Internet, Extranet, Plugins, TCP/IP, Hardware and Software Requirements.
Discuss various ethical issue which may faced by utilizing information techno...

Network Topologies
Topology is a network's virtual shape or structure. This shape does not necessarily correspond to the actual physical layout of the devices on the network. For example, the computers on a home LAN may be arranged in a circle in a family room, but it would be highly unlikely to find a ring topology there.
In computer networking, topology refers to the layout of connected devices. This article introduces the standard topologies of networking.
Network topologies are categorized into the following basic types:
• bus
• ring
• star
• tree
• mesh
More complex networks can be built as hybrids of two or more of the above basic topologies.
Bus Topology
Bus networks (not to be confused with the system bus of a computer) use a common backbone to connect all devices. A single cable, the backbone functions as a shared communication medium that devices attach or tap into with an interface connector. A device wanting to communicate with another device on the network sends a broadcast message onto the wire that all other devices see, but only the intended recipient actually accepts and processes the message.
Bus topologies are relatively easy to install and don't require much cabling compared to the alternatives. Bus networks work best with a limited number of devices. If more than a few dozen computers are added to a network bus, performance problems will likely result. In addition, if the backbone cable fails, the entire network effectively becomes unusable.
Bus Topology Diagram:
Ring Topology
In a ring network, every device has exactly two neighbors for communication purposes. All messages travel through a ring in the same direction (either "clockwise" or "counterclockwise"). A failure in any cable or device breaks the loop and can take down the entire network. To implement a ring network, one typically uses FDDI, SONET, or Token Ring technology. Ring topologies are found in some office buildings or school campuses.
Definition: Token Ring is a data link technology for local area networks (LANs). It operates at layer 2 of the OSI model.
Ring Topology Diagram:
Star Topology
Many home networks use the star topology. A star network features a central connection point called a "hub" that may be a hub, switch or router. Devices typically connect to the hub with Unshielded Twisted Pair (UTP) Ethernet. Compared to the bus topology, a star network generally requires more cable, but a failure in any star network cable will only take down one computer's network access and not the entire LAN. (If the hub fails, however, the entire network also fails.)
Star Topology Diagram:
Chapter 3 Computer Crimes

The document discusses computer and internet crime, including definitions of crime and different types of attacks such as viruses, worms, Trojan horses, denial-of-service attacks, and logic bombs. It also describes different types of perpetrators like hackers, crackers, insiders, industrial spies, cybercriminals, and cyberterrorists. Finally, it outlines some legal issues around fraud and recommendations for reducing internet vulnerabilities through risk assessment, security policies, education, and installing firewalls.
Computer Crimes

This document discusses various legal issues related to computing. It begins by defining different types of cybercrimes such as hacking, cracking, cyber piracy, cyber trespass, and cyber vandalism. It notes that many cybercrimes go unreported due to embarrassment or fears over security practices. The document also discusses the difference between hackers, crackers, white hat and black hat hackers. It considers issues like counter hacking and whether ethical hacking should be allowed. Finally, it examines the need for separate cybercrime laws and defines cyber-exacerbated and cyber-assisted crimes.
Cyber ethics

This document provides an overview of cyber ethics topics including:
- An introduction to cyber ethics and its history dating back to the 1940s.
- The importance of teaching cyber ethics to protect personal information, promote fair competition, and encourage responsible internet use.
- Common cyber ethics issues like copyright infringement, cyberbullying, hacking, and understanding appropriate online behavior.
- Examples of cyber ethics rules and the do's and don'ts of responsible internet use.
- Frequently asked questions about why cyber ethics is important and what the need is for teaching proper cyber ethics.
Deepak malviya mp 03 subject 703

The document discusses the history and definitions of the Internet, intranet, and extranet. The Internet began in the 1960s as the ARPANET network established by the US defense industry. It later expanded and became publicly available, now offering information access and communication globally. An intranet is a private network that securely shares information within an organization. An extranet allows selective internal information from an organization to be accessed by external partners and remote employees outside the corporate firewall but still maintains some security. The key differences between these networks are their size, accessibility, security features, and intended users.
COmPuter

This document provides information about computer ethics and computer viruses. It discusses 10 commandments of computer ethics such as not using computers to harm others or steal. It then gives a history of computer viruses dating back to 1971 and discusses various types of viruses like boot sector viruses and worms. The document also outlines signs of computer infection and tools that can be used for virus removal.
Computer ethics

The document discusses various topics related to computer ethics. It begins by defining computer ethics as enforcing ethical implementation and use of computing resources through avoiding copyright infringement and unauthorized distribution of digital content. It then lists 10 commandments of computer ethics established by the Computer Ethics Institute in 1992. Some concepts that can lead to unethical computer use discussed include data stealing, cybercrime, hacking, and embezzlement. Cybercrime refers to criminal acts involving computers or networks. Common types of cybercrime are hacking, stealing software/data, and identity theft. Data theft is also common using devices like USB drives to copy large amounts of data. Hacking involves exploiting security weaknesses for unauthorized access, while social engineering and malware attacks are other risks.
Computer

The document discusses various topics related to technology and computer security including:
1. It defines technology abuse as the misuse of technology and lists examples of computer crimes like hacking.
2. Hackers are skilled computer users who break into other people's computers to steal information and data without permission, which is illegal.
3. The document discusses the need for computer security and lists measures like backing up data, access codes, and passwords to restrict unauthorized access.
Etical and professional issues of computer

Group 08 is comprised of 4 students: M. Abdullah, Dua Zahra, Sidra Saher, and Narmeen Bushra. Their topic is on legal, ethical, and professional issues related to computers. The document defines key terms like computer ethics, codes of ethics, intellectual property, privacy, and computer crimes. It also differentiates between ethics and laws. Intellectual property includes patents, trademarks, designs, and copyright. Privacy can be increased by using firewalls and clearing browser histories. Authentication verifies a user's identity through methods like user IDs, passwords, smart cards, and biometrics. The document discusses controversial online content like pornography and slander, as well as types of internet filtering and computer crimes
Chapter 4 Computer Science :: Computer Ethics and Security

This document discusses computer ethics and security risks. It begins by defining computer ethics as moral guidelines governing computer use. It then lists seven frequently discussed areas of computer ethics: unauthorized computer use, software piracy, information accuracy, intellectual property rights, codes of conduct, information privacy, and green computing. The document goes on to define computer security risks and common types like hackers, crackers, and cybercriminals. It also outlines methods to safeguard against risks such as viruses, unauthorized access, and theft through antivirus software, firewalls, and access controls.
Introduction to computer

This document provides an introduction to computers, including definitions and explanations of key concepts. It discusses how computers are important in many industries and aspects of modern life. The document also describes the four phases of the information processing cycle: input, processing, storage, and output. It explains the stages of the data processing cycle in more detail and lists some of the key strengths of computers, such as speed, accuracy, automatic operation, storage capacity, and diligence. Both positive and negative impacts of computers on areas like health, social behavior, learning, and personal and professional life are outlined.
Mikial Singh Nijjar | Where Is Information Technology Headed?

Information technology is changing nearly every aspect of modern life. It refers to any technology that helps produce, manipulate, store, communicate, or disseminate information. The document discusses how IT is affecting education, health, finance, government, jobs, and personal life. It also outlines the basic components of computers, including hardware, software, data storage, input/output, and how data is turned into useful information. The future of IT is focused on greater portability, personalization, collaboration, cloud computing and artificial intelligence as computers and communications continue to converge.
Computer Security and Safety, Ethics & Privacy

This document discusses computer security risks and techniques to protect against unauthorized access and use. It defines computer security risks and describes various types of cybercrime perpetrators. Various types of Internet and network attacks like viruses, worms, Trojan horses, and rootkits are explained. Symptoms of an infected computer and safeguards against hardware theft, vandalism, and malicious infections are presented. Users can take precautions like using antivirus software, firewalls, and strong passwords to safeguard against attacks.
Introduction to cybercrime

This document provides an introduction to cybercrime, including definitions of key terms, classifications of cybercrimes, and descriptions of common cybercrime activities. It defines cybercrime as illegal activities that target computer systems and data. Cybercrimes are categorized as those against individuals, property, organizations, and society. Examples include phishing, spamming, hacking, software piracy, and cyberterrorism. Cybercriminals are also classified as those seeking recognition, financial gain, or insider revenge.
Smart-phone-with-Chains-PowerPoint-Widescreen (1)

The document discusses cyber crimes and cyber safety. It defines cyber crimes as illegal activities conducted online where computers are tools or targets. Common cyber crimes include identity theft, hacking, and viruses. The document then defines cyber safety as practices to protect personal information and computers from attacks. It provides the top four cyber safety actions of running antivirus software, preventing identity theft, using personal firewalls, and protecting passwords. The document concludes by discussing IT Act provisions related to legal validity of emails, e-commerce, digital signatures, and statutory remedies for computer intrusions.
Ahmed computer

The document discusses different types of computer networks including personal area networks (PAN), local area networks (LAN), and wide area networks (WAN). It explains that routers are used to connect devices within a home network and spread the internet connection. Some advantages of a home network are allowing multiple users to share internet access and data. However, disadvantages include high costs if many devices are connected and security risks if the network is not properly secured.
C3 and digital citizenship

This document discusses cyber safety, cyber ethics, and cyber security. It defines each term and provides examples. Cyber safety involves responsible online behaviors to stay safe. Cyber ethics is about positive and ethical online conduct. Cyber security protects information and computer systems from online threats. The document recommends strategies like using antivirus software and not sharing personal information. It provides additional resources from organizations that educate on internet safety.
Computer ethics and crime

This document discusses computer ethics and crimes. It notes that computers are now used extensively for many purposes but can be misused by those with bad intentions to harm information. It discusses the importance of computer ethics and intellectual property rights to protect owners' work. It describes different types of computer crimes like software piracy, hacking, and cracking that violate these ethics and laws. The document advocates for strong computer security controls and ethical computer usage.
Chapter 4 2016

This document discusses computer ethics and security. It covers netiquette rules for email, chat rooms and online communications. Areas of computer ethics discussed include information accuracy, green computing, codes of conduct, information privacy, and intellectual property. Computer security risks are also examined, such as malicious code, unauthorized access, hardware/software theft, information theft, and system failure. Ways to mitigate these risks include encryption, access controls, firewalls, anti-virus software, and uninterruptible power supplies.
Computer ethics

This document discusses various topics relating to computer ethics and privacy. It addresses issues like plagiarism, encryption, privacy in the workplace, protecting privacy online, computer crimes and viruses, cyberstalking, and information warfare. It emphasizes the importance of respecting oneself, others, and academic integrity when using computers and the internet.
Computer Ethics

The document discusses several ethical challenges related to information technology, including issues around software piracy, intellectual property, privacy, computer abuse, appropriate internet use, and establishing codes of ethics for IT professionals. It provides examples of both ethical and unethical behaviors related to computing and asks questions about who is responsible for dealing with ethical issues.
Chap 1

The document discusses key aspects of information systems including hardware, software, data, people, and procedures. It then covers various measures to secure data such as software access restrictions, backup and recovery, and virus protection. Finally, it discusses the evolution of the internet from early networks in the 1960s-1970s to the introduction of the world wide web in the 1990s.
Empowerment Technologies Lecture 3 (Philippines SHS)

Feel free to share to every aspiring ICT SHS teacher that is starting out. Just please do not take the copyright credit. The content is taken from Rex and Abiva Empowerment Technologies books.
cyber crime

Cyber crime refers to any illegal activities conducted through computers and online networks. There are various types of cyber criminals, including children, dissatisfied employees, and professional hackers. Common types of cyber crimes include hacking, email bombing, data interference, cyber stalking, and denial of service attacks. Cyber crime is rising rapidly in countries like India and Pakistan. To protect against cyber crimes, users should use antivirus software, firewalls, strong passwords, and back up their data regularly.
Information Technology (IT)

IT refers to the application of computers to store, retrieve, transmit, and manipulate data. There are three levels of IT: data, information, and knowledge. Computers help quality functions like data collection, analysis, statistical analysis, process control, and automated testing and inspection. Issues with IT include internet privacy, gender differences in use, socioeconomic divides, resource equity, and teacher bias. Emerging technologies include more advanced wireless networks, artificial intelligence, e-paper, wallet PCs, and e-books.
World Wide Web and Internet

The Internet is a global system of interconnected computer networks that connects billions of devices worldwide. It is a network of networks comprised of private, public, academic and government networks linked together using various networking technologies. The Internet enables new forms of human interaction like social networking and allows people worldwide to access a vast amount of information and resources through services like the World Wide Web and email.
More Related Content
What's hot
Deepak malviya mp 03 subject 703

The document discusses the history and definitions of the Internet, intranet, and extranet. The Internet began in the 1960s as the ARPANET network established by the US defense industry. It later expanded and became publicly available, now offering information access and communication globally. An intranet is a private network that securely shares information within an organization. An extranet allows selective internal information from an organization to be accessed by external partners and remote employees outside the corporate firewall but still maintains some security. The key differences between these networks are their size, accessibility, security features, and intended users.
COmPuter

This document provides information about computer ethics and computer viruses. It discusses 10 commandments of computer ethics such as not using computers to harm others or steal. It then gives a history of computer viruses dating back to 1971 and discusses various types of viruses like boot sector viruses and worms. The document also outlines signs of computer infection and tools that can be used for virus removal.
Computer ethics

The document discusses various topics related to computer ethics. It begins by defining computer ethics as enforcing ethical implementation and use of computing resources through avoiding copyright infringement and unauthorized distribution of digital content. It then lists 10 commandments of computer ethics established by the Computer Ethics Institute in 1992. Some concepts that can lead to unethical computer use discussed include data stealing, cybercrime, hacking, and embezzlement. Cybercrime refers to criminal acts involving computers or networks. Common types of cybercrime are hacking, stealing software/data, and identity theft. Data theft is also common using devices like USB drives to copy large amounts of data. Hacking involves exploiting security weaknesses for unauthorized access, while social engineering and malware attacks are other risks.
Computer

The document discusses various topics related to technology and computer security including:
1. It defines technology abuse as the misuse of technology and lists examples of computer crimes like hacking.
2. Hackers are skilled computer users who break into other people's computers to steal information and data without permission, which is illegal.
3. The document discusses the need for computer security and lists measures like backing up data, access codes, and passwords to restrict unauthorized access.
Etical and professional issues of computer

Group 08 is comprised of 4 students: M. Abdullah, Dua Zahra, Sidra Saher, and Narmeen Bushra. Their topic is on legal, ethical, and professional issues related to computers. The document defines key terms like computer ethics, codes of ethics, intellectual property, privacy, and computer crimes. It also differentiates between ethics and laws. Intellectual property includes patents, trademarks, designs, and copyright. Privacy can be increased by using firewalls and clearing browser histories. Authentication verifies a user's identity through methods like user IDs, passwords, smart cards, and biometrics. The document discusses controversial online content like pornography and slander, as well as types of internet filtering and computer crimes
Chapter 4 Computer Science :: Computer Ethics and Security

This document discusses computer ethics and security risks. It begins by defining computer ethics as moral guidelines governing computer use. It then lists seven frequently discussed areas of computer ethics: unauthorized computer use, software piracy, information accuracy, intellectual property rights, codes of conduct, information privacy, and green computing. The document goes on to define computer security risks and common types like hackers, crackers, and cybercriminals. It also outlines methods to safeguard against risks such as viruses, unauthorized access, and theft through antivirus software, firewalls, and access controls.
Introduction to computer

This document provides an introduction to computers, including definitions and explanations of key concepts. It discusses how computers are important in many industries and aspects of modern life. The document also describes the four phases of the information processing cycle: input, processing, storage, and output. It explains the stages of the data processing cycle in more detail and lists some of the key strengths of computers, such as speed, accuracy, automatic operation, storage capacity, and diligence. Both positive and negative impacts of computers on areas like health, social behavior, learning, and personal and professional life are outlined.
Mikial Singh Nijjar | Where Is Information Technology Headed?

Information technology is changing nearly every aspect of modern life. It refers to any technology that helps produce, manipulate, store, communicate, or disseminate information. The document discusses how IT is affecting education, health, finance, government, jobs, and personal life. It also outlines the basic components of computers, including hardware, software, data storage, input/output, and how data is turned into useful information. The future of IT is focused on greater portability, personalization, collaboration, cloud computing and artificial intelligence as computers and communications continue to converge.
Computer Security and Safety, Ethics & Privacy

This document discusses computer security risks and techniques to protect against unauthorized access and use. It defines computer security risks and describes various types of cybercrime perpetrators. Various types of Internet and network attacks like viruses, worms, Trojan horses, and rootkits are explained. Symptoms of an infected computer and safeguards against hardware theft, vandalism, and malicious infections are presented. Users can take precautions like using antivirus software, firewalls, and strong passwords to safeguard against attacks.
Introduction to cybercrime

This document provides an introduction to cybercrime, including definitions of key terms, classifications of cybercrimes, and descriptions of common cybercrime activities. It defines cybercrime as illegal activities that target computer systems and data. Cybercrimes are categorized as those against individuals, property, organizations, and society. Examples include phishing, spamming, hacking, software piracy, and cyberterrorism. Cybercriminals are also classified as those seeking recognition, financial gain, or insider revenge.
Smart-phone-with-Chains-PowerPoint-Widescreen (1)

The document discusses cyber crimes and cyber safety. It defines cyber crimes as illegal activities conducted online where computers are tools or targets. Common cyber crimes include identity theft, hacking, and viruses. The document then defines cyber safety as practices to protect personal information and computers from attacks. It provides the top four cyber safety actions of running antivirus software, preventing identity theft, using personal firewalls, and protecting passwords. The document concludes by discussing IT Act provisions related to legal validity of emails, e-commerce, digital signatures, and statutory remedies for computer intrusions.
Ahmed computer

The document discusses different types of computer networks including personal area networks (PAN), local area networks (LAN), and wide area networks (WAN). It explains that routers are used to connect devices within a home network and spread the internet connection. Some advantages of a home network are allowing multiple users to share internet access and data. However, disadvantages include high costs if many devices are connected and security risks if the network is not properly secured.
C3 and digital citizenship

This document discusses cyber safety, cyber ethics, and cyber security. It defines each term and provides examples. Cyber safety involves responsible online behaviors to stay safe. Cyber ethics is about positive and ethical online conduct. Cyber security protects information and computer systems from online threats. The document recommends strategies like using antivirus software and not sharing personal information. It provides additional resources from organizations that educate on internet safety.
Computer ethics and crime

This document discusses computer ethics and crimes. It notes that computers are now used extensively for many purposes but can be misused by those with bad intentions to harm information. It discusses the importance of computer ethics and intellectual property rights to protect owners' work. It describes different types of computer crimes like software piracy, hacking, and cracking that violate these ethics and laws. The document advocates for strong computer security controls and ethical computer usage.
Chapter 4 2016

This document discusses computer ethics and security. It covers netiquette rules for email, chat rooms and online communications. Areas of computer ethics discussed include information accuracy, green computing, codes of conduct, information privacy, and intellectual property. Computer security risks are also examined, such as malicious code, unauthorized access, hardware/software theft, information theft, and system failure. Ways to mitigate these risks include encryption, access controls, firewalls, anti-virus software, and uninterruptible power supplies.
Computer ethics

This document discusses various topics relating to computer ethics and privacy. It addresses issues like plagiarism, encryption, privacy in the workplace, protecting privacy online, computer crimes and viruses, cyberstalking, and information warfare. It emphasizes the importance of respecting oneself, others, and academic integrity when using computers and the internet.
Computer Ethics

The document discusses several ethical challenges related to information technology, including issues around software piracy, intellectual property, privacy, computer abuse, appropriate internet use, and establishing codes of ethics for IT professionals. It provides examples of both ethical and unethical behaviors related to computing and asks questions about who is responsible for dealing with ethical issues.
Chap 1

The document discusses key aspects of information systems including hardware, software, data, people, and procedures. It then covers various measures to secure data such as software access restrictions, backup and recovery, and virus protection. Finally, it discusses the evolution of the internet from early networks in the 1960s-1970s to the introduction of the world wide web in the 1990s.
Empowerment Technologies Lecture 3 (Philippines SHS)

Feel free to share to every aspiring ICT SHS teacher that is starting out. Just please do not take the copyright credit. The content is taken from Rex and Abiva Empowerment Technologies books.
cyber crime

Cyber crime refers to any illegal activities conducted through computers and online networks. There are various types of cyber criminals, including children, dissatisfied employees, and professional hackers. Common types of cyber crimes include hacking, email bombing, data interference, cyber stalking, and denial of service attacks. Cyber crime is rising rapidly in countries like India and Pakistan. To protect against cyber crimes, users should use antivirus software, firewalls, strong passwords, and back up their data regularly.
What's hot (20)
Chapter 4 Computer Science :: Computer Ethics and Security

Chapter 4 Computer Science :: Computer Ethics and Security
Mikial Singh Nijjar | Where Is Information Technology Headed?

Mikial Singh Nijjar | Where Is Information Technology Headed?
Empowerment Technologies Lecture 3 (Philippines SHS)

Empowerment Technologies Lecture 3 (Philippines SHS)
Similar to Internet(2)
Information Technology (IT)

IT refers to the application of computers to store, retrieve, transmit, and manipulate data. There are three levels of IT: data, information, and knowledge. Computers help quality functions like data collection, analysis, statistical analysis, process control, and automated testing and inspection. Issues with IT include internet privacy, gender differences in use, socioeconomic divides, resource equity, and teacher bias. Emerging technologies include more advanced wireless networks, artificial intelligence, e-paper, wallet PCs, and e-books.
World Wide Web and Internet

The Internet is a global system of interconnected computer networks that connects billions of devices worldwide. It is a network of networks comprised of private, public, academic and government networks linked together using various networking technologies. The Internet enables new forms of human interaction like social networking and allows people worldwide to access a vast amount of information and resources through services like the World Wide Web and email.
Introduction To Internet

The document summarizes the origins and administration of the Internet. It begins by explaining how the US Defense Department established the ARPAnet in the 1960s to share research between universities and the military. This early network helped develop communication protocols like TCP/IP and later broke into both the MILnet for military use and ARPAnet for research and education. The Internet Society was founded in 1992 to support the technical evolution of the Internet. The document then lists some key advantages and resources available on the Internet like information, communication, business opportunities, and entertainment. It concludes by noting that no single entity owns the Internet and that various committees work to maintain its integrity.
Hamza

This document discusses internet security. It begins by defining the internet and its types such as dial up, DSL, cable, wireless, satellite, and cellular. It then defines internet security and its objective to establish rules and measures against attacks over the internet. The document outlines the history of internet security from 1960 to 2000. It discusses common internet security threats like viruses, trojan horses, worms, hacking, phishing, and spyware. Finally, it recommends techniques to improve security such as using strong passwords, antivirus software, firewalls, authenticating data, unlinking accounts, and blocking cookies.
Chirag sharma

The document provides an introduction to the Internet, including:
(1) It describes how the Internet has revolutionized communication and business by allowing people to work and do business globally.
(2) It explains the origins of the Internet from research networks in the 1960s and the development of TCP/IP that allowed computers to connect.
(3) It outlines some common applications and uses of the Internet including email, chatting, online marketing and business transactions.
Future of the Internet

Presentation discusses these Internet future developments:
1. Social computing will expand to business
2. Internet access will be ubiquitous
3. The Web will become faster
4. The Web will become smarter
5. Security will improve
6. IT products will morph into services
Essays On The Internet

The document provides a history of the development of the Internet. It discusses how the ARPANET was developed in the 1960s by the US Department of Defense as the world's first operational information sharing network. It then describes how electronic mail became popular for communication and how this led to the development of instant messaging software for real-time conversations. Finally, it discusses the introduction of blogs in the mid-1990s as personal online diaries and how they have become a popular format for sharing views and media on various topics.
beware of Thing Bot

The document discusses the security risks posed by the growing Internet of Things (IoT). As more everyday devices become connected to the internet, they could be vulnerable to attacks that turn them into "thingbots" that are part of botnets controlled by hackers. This could allow hackers to launch large-scale distributed denial of service (DDoS) attacks or spy on users by accessing unsecured cameras and other smart home devices. Researchers have already discovered botnets made up of thousands of compromised IoT devices like routers, smart TVs and refrigerators. To address this, the document recommends steps like using secure chips and honeypots to detect malicious activity from IoT devices and help secure the growing IoT ecosystem.
Internet Essay

The document discusses the history and development of the Internet. It began as a project called ARPANET in the 1950s by the U.S. Department of Defense to link computers and allow for information sharing. Through the 1970s, protocols like TCP/IP were developed and networks expanded. The World Wide Web was created in 1989 by Tim Berners-Lee, allowing for easy information sharing through hyperlinks on Internet-connected computers. The Internet has since revolutionized communication, business, education and more.
Module-III-Unit-II-Trend-and-Issues-in-Information-Technology.pptx

The document discusses the history and purpose of the Association for Computing Machinery (ACM). It states that ACM was founded in 1947 at Columbia University to advance the field of computing through information sharing and promoting high professional standards. ACM publishes research and works to advance computing education. It aims to serve both professional and public interests in computing.
Unit 1 Introducation

Introduction to Cyberspace and its Architecture, Evolution and Basic Concepts of Internet, Cyberspace, Internet Ownership and Management, Data Security and Management, Data Encryption and Digital Signature, Convergence. Internet Telephony
and VPN, Social Issues in the Regulation of Cyberspace, The Regulability of Cyberspace, UNCITRAL Model Law on Electronics Commerce 1996
Chapter 1

This document provides an overview of how the web works. It begins with the basic concepts and history of the Internet, distinguishing between the Internet and the World Wide Web. It describes key components like web browsers that users employ to access web pages, and web servers that host websites and content. Specific examples of popular browsers like Chrome and Safari are outlined, as well as common web server software like Apache, IIS, and Nginx. The document aims to explain the fundamental workings and interconnected pieces that make up the modern web.
Going Online

The document discusses how to connect to and use the Internet and World Wide Web. It explains that the Internet is a network connecting computers worldwide, while the World Wide Web is a system for accessing information on the Internet through websites. It describes the components needed to connect, including a computer, Internet service provider, modem, and web browser. It also defines key terms like website, URL, search engine, and how the earliest networks like ARPANET evolved into today's Internet.
Going Online

The document discusses how to connect to and use the Internet and World Wide Web. It explains that the Internet is a network connecting computers worldwide, while the World Wide Web is a system for accessing information on the Internet through websites. Websites have unique URLs and domain name extensions like .com, .org, or .edu. To connect, you need a computer, Internet service provider, modem, and web browser software. Search engines help users find information on websites.
Chapter-7-Networks-and-The-Internet.pptx

This document provides an overview of foundational topics in networking, including the evolution of computer networking models from centralized to distributed to collaborative computing. It describes key aspects of networking infrastructure such as the Internet, Internet protocols, Internet access providers, and the transmission of data. It also summarizes the development and functioning of the World Wide Web, URLs, web servers, and top-level domains.
Internet of things (IoT)

This talks comprehensively on Internet of Things (IoT):
What is it?,
Applications of IoT.
Real-time implementation of IoT.
The challenges that lies ahead in making the internet more intelligent.
It elaborates on the current industry trends and how the IoT could be adopted for smarter enability of technology.
E content internet

The document summarizes key information about the internet. It discusses the origins of the internet from the ARPANET network developed by the US Department of Defense in 1969. It allowed multiple users to simultaneously send and receive information over communication paths. Universities were later allowed to join, developing software and giving birth to the modern internet. The document outlines purposes of computer networks like facilitating communication, sharing hardware and files. It lists advantages like serving as a virtual private network for organizations and a communication channel for marketing. Risks discussed include theft of personal information and virus threats.
4.Jan Holler, Vlasios Tsiatsis, Catherine Mulligan, Stefan Avesand, Stamatis ...

This document provides an introduction to the new field of the Internet of Things (IoT). It discusses the evolution from traditional machine-to-machine communications to a world where billions of intelligent physical objects are connected via the Internet. The document is written by experts from Ericsson, SAP and Imperial College London who have extensive experience in IoT technologies, applications, systems architecture and deployments. It aims to provide an overview of this new area and the basic building blocks needed to realize a connected world of intelligent physical objects.
Chapter-2.docx

This document discusses the growing dependency of individuals and organizations on cyberspace and the associated risks. It provides historical context on the evolution of the internet from ARPANET. Key points covered include:
- Individuals and organizations have become increasingly reliant on cyberspace for daily activities, work operations, and digital transformation, leaving them vulnerable to cyber threats.
- Emerging areas of focus for cybersecurity are the internet of things and how hackers can access systems through connected devices, as well as exploiting personal devices with stored data.
- Common cyber risks discussed are viruses, service disruptions, phishing, SQL injection attacks, and password attacks. Stricter laws have been implemented in some countries like the
Internet

The Internet is a global system of interconnected computer networks that connects billions of users worldwide. It is a network of networks comprising millions of private, public, academic, business, and government networks linked together via various networking technologies.
An intranet is a private network within an organization that uses standard network technologies like Ethernet and TCP/IP to facilitate communication and improve data sharing. An intranet typically provides internet access but is protected by a firewall. An extranet extends an intranet by opening the firewall to controlled external partners.
Key benefits of intranets include increased and lower-cost internal communication, accessibility of timely information, and easy publication and distribution of information.
Similar to Internet(2) (20)
Module-III-Unit-II-Trend-and-Issues-in-Information-Technology.pptx

Module-III-Unit-II-Trend-and-Issues-in-Information-Technology.pptx
4.Jan Holler, Vlasios Tsiatsis, Catherine Mulligan, Stefan Avesand, Stamatis ...

4.Jan Holler, Vlasios Tsiatsis, Catherine Mulligan, Stefan Avesand, Stamatis ...
Recently uploaded
"Frontline Battles with DDoS: Best practices and Lessons Learned", Igor Ivaniuk

At this talk we will discuss DDoS protection tools and best practices, discuss network architectures and what AWS has to offer. Also, we will look into one of the largest DDoS attacks on Ukrainian infrastructure that happened in February 2022. We'll see, what techniques helped to keep the web resources available for Ukrainians and how AWS improved DDoS protection for all customers based on Ukraine experience
Apps Break Data

How information systems are built or acquired puts information, which is what they should be about, in a secondary place. Our language adapted accordingly, and we no longer talk about information systems but applications. Applications evolved in a way to break data into diverse fragments, tightly coupled with applications and expensive to integrate. The result is technical debt, which is re-paid by taking even bigger "loans", resulting in an ever-increasing technical debt. Software engineering and procurement practices work in sync with market forces to maintain this trend. This talk demonstrates how natural this situation is. The question is: can something be done to reverse the trend?
The Microsoft 365 Migration Tutorial For Beginner.pptx

This presentation will help you understand the power of Microsoft 365. However, we have mentioned every productivity app included in Office 365. Additionally, we have suggested the migration situation related to Office 365 and how we can help you.
You can also read: https://www.systoolsgroup.com/updates/office-365-tenant-to-tenant-migration-step-by-step-complete-guide/
Principle of conventional tomography-Bibash Shahi ppt..pptx

before the computed tomography, it had been widely used.
5th LF Energy Power Grid Model Meet-up Slides

5th Power Grid Model Meet-up
It is with great pleasure that we extend to you an invitation to the 5th Power Grid Model Meet-up, scheduled for 6th June 2024. This event will adopt a hybrid format, allowing participants to join us either through an online Mircosoft Teams session or in person at TU/e located at Den Dolech 2, Eindhoven, Netherlands. The meet-up will be hosted by Eindhoven University of Technology (TU/e), a research university specializing in engineering science & technology.
Power Grid Model
The global energy transition is placing new and unprecedented demands on Distribution System Operators (DSOs). Alongside upgrades to grid capacity, processes such as digitization, capacity optimization, and congestion management are becoming vital for delivering reliable services.
Power Grid Model is an open source project from Linux Foundation Energy and provides a calculation engine that is increasingly essential for DSOs. It offers a standards-based foundation enabling real-time power systems analysis, simulations of electrical power grids, and sophisticated what-if analysis. In addition, it enables in-depth studies and analysis of the electrical power grid’s behavior and performance. This comprehensive model incorporates essential factors such as power generation capacity, electrical losses, voltage levels, power flows, and system stability.
Power Grid Model is currently being applied in a wide variety of use cases, including grid planning, expansion, reliability, and congestion studies. It can also help in analyzing the impact of renewable energy integration, assessing the effects of disturbances or faults, and developing strategies for grid control and optimization.
What to expect
For the upcoming meetup we are organizing, we have an exciting lineup of activities planned:
-Insightful presentations covering two practical applications of the Power Grid Model.
-An update on the latest advancements in Power Grid -Model technology during the first and second quarters of 2024.
-An interactive brainstorming session to discuss and propose new feature requests.
-An opportunity to connect with fellow Power Grid Model enthusiasts and users.
AppSec PNW: Android and iOS Application Security with MobSF

Mobile Security Framework - MobSF is a free and open source automated mobile application security testing environment designed to help security engineers, researchers, developers, and penetration testers to identify security vulnerabilities, malicious behaviours and privacy concerns in mobile applications using static and dynamic analysis. It supports all the popular mobile application binaries and source code formats built for Android and iOS devices. In addition to automated security assessment, it also offers an interactive testing environment to build and execute scenario based test/fuzz cases against the application.
This talk covers:
Using MobSF for static analysis of mobile applications.
Interactive dynamic security assessment of Android and iOS applications.
Solving Mobile app CTF challenges.
Reverse engineering and runtime analysis of Mobile malware.
How to shift left and integrate MobSF/mobsfscan SAST and DAST in your build pipeline.
Dandelion Hashtable: beyond billion requests per second on a commodity server

This slide deck presents DLHT, a concurrent in-memory hashtable. Despite efforts to optimize hashtables, that go as far as sacrificing core functionality, state-of-the-art designs still incur multiple memory accesses per request and block request processing in three cases. First, most hashtables block while waiting for data to be retrieved from memory. Second, open-addressing designs, which represent the current state-of-the-art, either cannot free index slots on deletes or must block all requests to do so. Third, index resizes block every request until all objects are copied to the new index. Defying folklore wisdom, DLHT forgoes open-addressing and adopts a fully-featured and memory-aware closed-addressing design based on bounded cache-line-chaining. This design offers lock-free index operations and deletes that free slots instantly, (2) completes most requests with a single memory access, (3) utilizes software prefetching to hide memory latencies, and (4) employs a novel non-blocking and parallel resizing. In a commodity server and a memory-resident workload, DLHT surpasses 1.6B requests per second and provides 3.5x (12x) the throughput of the state-of-the-art closed-addressing (open-addressing) resizable hashtable on Gets (Deletes).
Taking AI to the Next Level in Manufacturing.pdf

Read Taking AI to the Next Level in Manufacturing to gain insights on AI adoption in the manufacturing industry, such as:
1. How quickly AI is being implemented in manufacturing.
2. Which barriers stand in the way of AI adoption.
3. How data quality and governance form the backbone of AI.
4. Organizational processes and structures that may inhibit effective AI adoption.
6. Ideas and approaches to help build your organization's AI strategy.
Generating privacy-protected synthetic data using Secludy and Milvus

During this demo, the founders of Secludy will demonstrate how their system utilizes Milvus to store and manipulate embeddings for generating privacy-protected synthetic data. Their approach not only maintains the confidentiality of the original data but also enhances the utility and scalability of LLMs under privacy constraints. Attendees, including machine learning engineers, data scientists, and data managers, will witness first-hand how Secludy's integration with Milvus empowers organizations to harness the power of LLMs securely and efficiently.
Introduction of Cybersecurity with OSS at Code Europe 2024

I develop the Ruby programming language, RubyGems, and Bundler, which are package managers for Ruby. Today, I will introduce how to enhance the security of your application using open-source software (OSS) examples from Ruby and RubyGems.
The first topic is CVE (Common Vulnerabilities and Exposures). I have published CVEs many times. But what exactly is a CVE? I'll provide a basic understanding of CVEs and explain how to detect and handle vulnerabilities in OSS.
Next, let's discuss package managers. Package managers play a critical role in the OSS ecosystem. I'll explain how to manage library dependencies in your application.
I'll share insights into how the Ruby and RubyGems core team works to keep our ecosystem safe. By the end of this talk, you'll have a better understanding of how to safeguard your code.
How to Interpret Trends in the Kalyan Rajdhani Mix Chart.pdf

A Mix Chart displays historical data of numbers in a graphical or tabular form. The Kalyan Rajdhani Mix Chart specifically shows the results of a sequence of numbers over different periods.
What is an RPA CoE? Session 1 – CoE Vision

In the first session, we will review the organization's vision and how this has an impact on the COE Structure.
Topics covered:
• The role of a steering committee
• How do the organization’s priorities determine CoE Structure?
Speaker:
Chris Bolin, Senior Intelligent Automation Architect Anika Systems
GNSS spoofing via SDR (Criptored Talks 2024)

In the realm of cybersecurity, offensive security practices act as a critical shield. By simulating real-world attacks in a controlled environment, these techniques expose vulnerabilities before malicious actors can exploit them. This proactive approach allows manufacturers to identify and fix weaknesses, significantly enhancing system security.
This presentation delves into the development of a system designed to mimic Galileo's Open Service signal using software-defined radio (SDR) technology. We'll begin with a foundational overview of both Global Navigation Satellite Systems (GNSS) and the intricacies of digital signal processing.
The presentation culminates in a live demonstration. We'll showcase the manipulation of Galileo's Open Service pilot signal, simulating an attack on various software and hardware systems. This practical demonstration serves to highlight the potential consequences of unaddressed vulnerabilities, emphasizing the importance of offensive security practices in safeguarding critical infrastructure.
HCL Notes and Domino License Cost Reduction in the World of DLAU

Webinar Recording: https://www.panagenda.com/webinars/hcl-notes-and-domino-license-cost-reduction-in-the-world-of-dlau/
The introduction of DLAU and the CCB & CCX licensing model caused quite a stir in the HCL community. As a Notes and Domino customer, you may have faced challenges with unexpected user counts and license costs. You probably have questions on how this new licensing approach works and how to benefit from it. Most importantly, you likely have budget constraints and want to save money where possible. Don’t worry, we can help with all of this!
We’ll show you how to fix common misconfigurations that cause higher-than-expected user counts, and how to identify accounts which you can deactivate to save money. There are also frequent patterns that can cause unnecessary cost, like using a person document instead of a mail-in for shared mailboxes. We’ll provide examples and solutions for those as well. And naturally we’ll explain the new licensing model.
Join HCL Ambassador Marc Thomas in this webinar with a special guest appearance from Franz Walder. It will give you the tools and know-how to stay on top of what is going on with Domino licensing. You will be able lower your cost through an optimized configuration and keep it low going forward.
These topics will be covered
- Reducing license cost by finding and fixing misconfigurations and superfluous accounts
- How do CCB and CCX licenses really work?
- Understanding the DLAU tool and how to best utilize it
- Tips for common problem areas, like team mailboxes, functional/test users, etc
- Practical examples and best practices to implement right away
Freshworks Rethinks NoSQL for Rapid Scaling & Cost-Efficiency

Freshworks creates AI-boosted business software that helps employees work more efficiently and effectively. Managing data across multiple RDBMS and NoSQL databases was already a challenge at their current scale. To prepare for 10X growth, they knew it was time to rethink their database strategy. Learn how they architected a solution that would simplify scaling while keeping costs under control.
GraphRAG for LifeSciences Hands-On with the Clinical Knowledge Graph

Tomaz Bratanic
Graph ML and GenAI Expert - Neo4j
Artificial Intelligence and Electronic Warfare

Artificial Intelligence and Electronic WarfarePapadakis K.-Cyber-Information Warfare Analyst & Cyber Defense/Security Consultant-Hellenic MoD
AI & Electronic Warfare[OReilly Superstream] Occupy the Space: A grassroots guide to engineering (an...![[OReilly Superstream] Occupy the Space: A grassroots guide to engineering (an...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[OReilly Superstream] Occupy the Space: A grassroots guide to engineering (an...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
The typical problem in product engineering is not bad strategy, so much as “no strategy”. This leads to confusion, lack of motivation, and incoherent action. The next time you look for a strategy and find an empty space, instead of waiting for it to be filled, I will show you how to fill it in yourself. If you’re wrong, it forces a correction. If you’re right, it helps create focus. I’ll share how I’ve approached this in the past, both what works and lessons for what didn’t work so well.
“Temporal Event Neural Networks: A More Efficient Alternative to the Transfor...

“Temporal Event Neural Networks: A More Efficient Alternative to the Transfor...Edge AI and Vision Alliance
For the full video of this presentation, please visit: https://www.edge-ai-vision.com/2024/06/temporal-event-neural-networks-a-more-efficient-alternative-to-the-transformer-a-presentation-from-brainchip/
Chris Jones, Director of Product Management at BrainChip , presents the “Temporal Event Neural Networks: A More Efficient Alternative to the Transformer” tutorial at the May 2024 Embedded Vision Summit.
The expansion of AI services necessitates enhanced computational capabilities on edge devices. Temporal Event Neural Networks (TENNs), developed by BrainChip, represent a novel and highly efficient state-space network. TENNs demonstrate exceptional proficiency in handling multi-dimensional streaming data, facilitating advancements in object detection, action recognition, speech enhancement and language model/sequence generation. Through the utilization of polynomial-based continuous convolutions, TENNs streamline models, expedite training processes and significantly diminish memory requirements, achieving notable reductions of up to 50x in parameters and 5,000x in energy consumption compared to prevailing methodologies like transformers.
Integration with BrainChip’s Akida neuromorphic hardware IP further enhances TENNs’ capabilities, enabling the realization of highly capable, portable and passively cooled edge devices. This presentation delves into the technical innovations underlying TENNs, presents real-world benchmarks, and elucidates how this cutting-edge approach is positioned to revolutionize edge AI across diverse applications.Recently uploaded (20)
"Frontline Battles with DDoS: Best practices and Lessons Learned", Igor Ivaniuk

"Frontline Battles with DDoS: Best practices and Lessons Learned", Igor Ivaniuk
The Microsoft 365 Migration Tutorial For Beginner.pptx

The Microsoft 365 Migration Tutorial For Beginner.pptx
Principle of conventional tomography-Bibash Shahi ppt..pptx

Principle of conventional tomography-Bibash Shahi ppt..pptx
AppSec PNW: Android and iOS Application Security with MobSF

AppSec PNW: Android and iOS Application Security with MobSF
Dandelion Hashtable: beyond billion requests per second on a commodity server

Dandelion Hashtable: beyond billion requests per second on a commodity server
Generating privacy-protected synthetic data using Secludy and Milvus

Generating privacy-protected synthetic data using Secludy and Milvus
Introduction of Cybersecurity with OSS at Code Europe 2024

Introduction of Cybersecurity with OSS at Code Europe 2024
How to Interpret Trends in the Kalyan Rajdhani Mix Chart.pdf

How to Interpret Trends in the Kalyan Rajdhani Mix Chart.pdf
Nordic Marketo Engage User Group_June 13_ 2024.pptx

Nordic Marketo Engage User Group_June 13_ 2024.pptx
HCL Notes and Domino License Cost Reduction in the World of DLAU

HCL Notes and Domino License Cost Reduction in the World of DLAU
Freshworks Rethinks NoSQL for Rapid Scaling & Cost-Efficiency

Freshworks Rethinks NoSQL for Rapid Scaling & Cost-Efficiency
GraphRAG for LifeSciences Hands-On with the Clinical Knowledge Graph

GraphRAG for LifeSciences Hands-On with the Clinical Knowledge Graph
[OReilly Superstream] Occupy the Space: A grassroots guide to engineering (an...![[OReilly Superstream] Occupy the Space: A grassroots guide to engineering (an...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[OReilly Superstream] Occupy the Space: A grassroots guide to engineering (an...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[OReilly Superstream] Occupy the Space: A grassroots guide to engineering (an...
“Temporal Event Neural Networks: A More Efficient Alternative to the Transfor...

“Temporal Event Neural Networks: A More Efficient Alternative to the Transfor...
Internet(2)
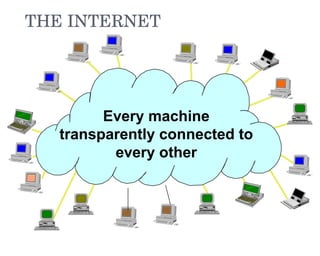
- 1. THE INTERNET Every machine transparently connected to every other
- 7. E-MAIL: Send and receive instant electronic messages
- 14. FORMS OF ATTACK CYBER TERRORISM COOKIES VIRUSES HACKING
- 20. Internet is a cooperative environment and has social as well as technical aspects. It is the responsibility of all the users to ensure trust of the community :-)
- 21. The growth of Internet is not a fluke or a fad, but the consequence of unleashing the power of individual creativity.