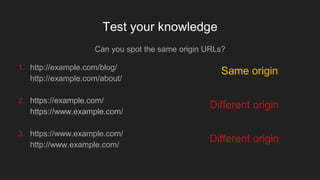
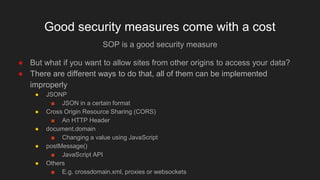
The document discusses various techniques for circumventing the same-origin policy (SOP) in web browsers, which aims to isolate documents retrieved from different origins for security reasons. It provides an overview of SOP and defines what constitutes the same origin. It then examines several methods for enabling cross-origin communication, such as JSONP, CORS headers, modifying the document.domain property in JavaScript, and using the postMessage API, noting security risks with improperly implementing these techniques. Code examples are provided to demonstrate JSONP and postMessage.