The document presents critical insights into WordPress security by Mehmet Ince, a senior penetration tester. Key points include best practices for application and database security, the importance of disabling certain features, and the dangers of using free themes and shared hosting. It also highlights significant vulnerabilities in WordPress and discusses the Cryptophp backdoor case that affects multiple CMS platforms.














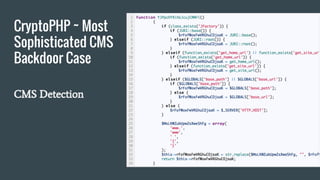
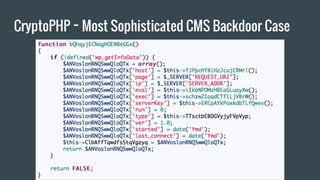
![CryptoPHP ~ Most Sophisticated CMS Backdoor Case
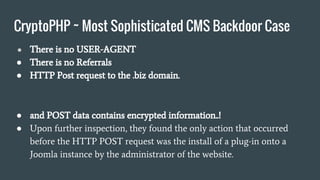
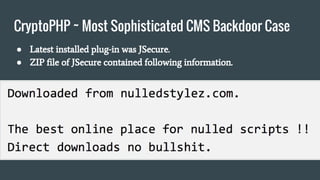
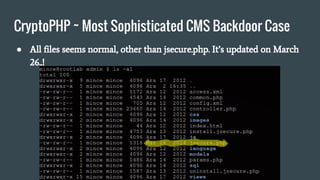
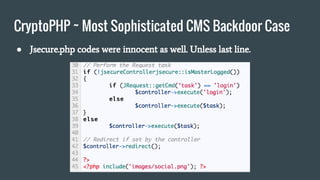
● Identified by Foxit-Security at May 2014.
● A researcher from Foxit-Security found a following HTTP request
generated by their customer server.
[08/May/2014:12:44:10 +0100] "POST http://worldcute.biz/ HTTP/1.1"
… unexpected journey has begun.](https://image.slidesharecdn.com/wordpresssecurity-160522112757/85/Wordpress-security-21-320.jpg)