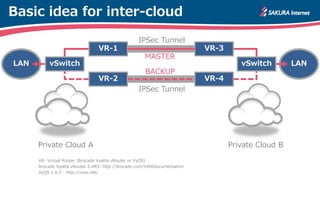
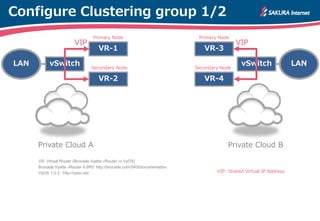
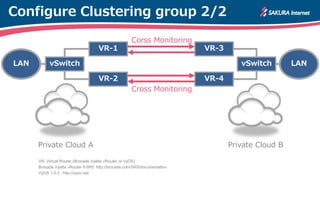
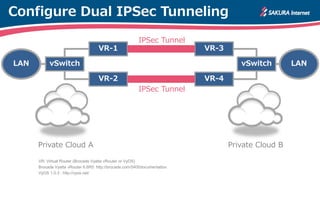
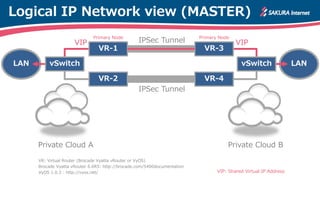
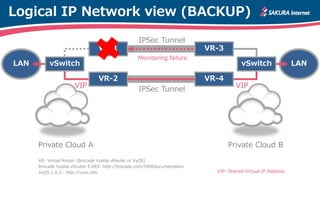
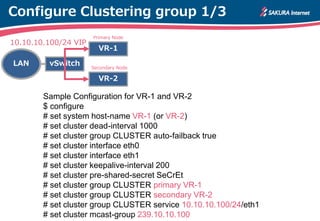
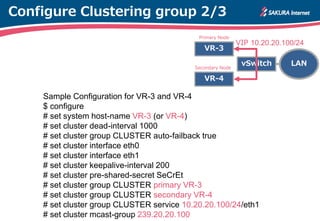
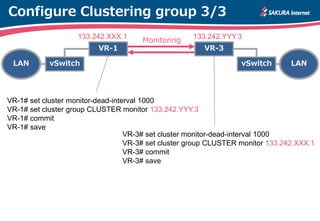
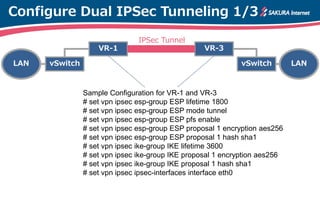
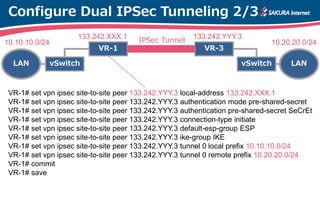
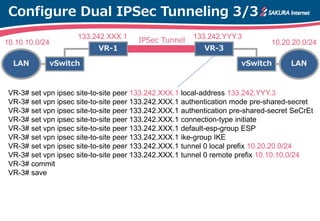
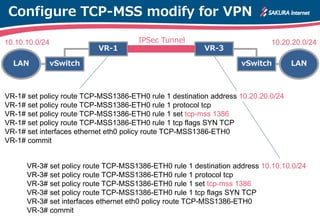
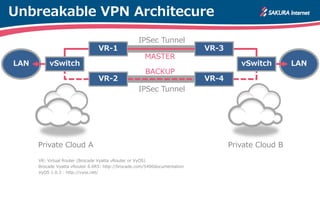
The document is a technical guide by Naoto Matsumoto from Sakura Internet Research Center detailing the configuration of IPsec tunneling and clustering for virtual routers (VR) using Brocade Vyatta and VyOS systems. It includes sample configurations and monitoring setups for dual IPsec tunnels between two private clouds, as well as tips for achieving an unbreakable VPN. The document references specific software versions and provides links for further technical documentation.