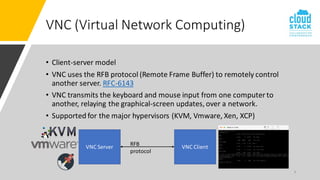
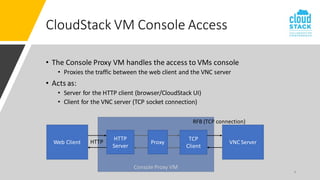
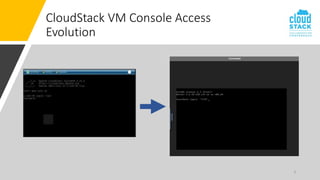
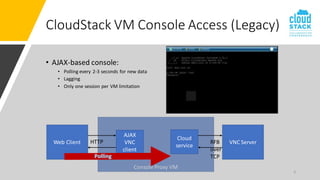
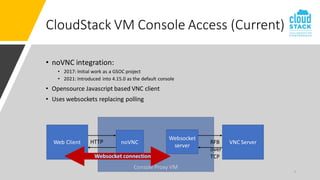
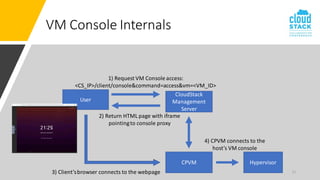
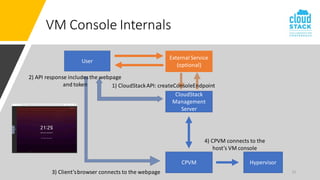
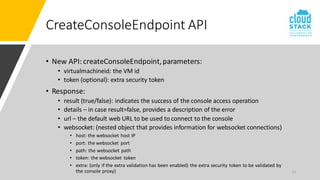
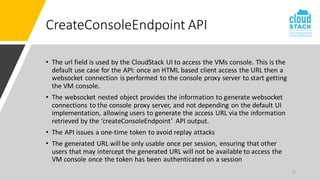
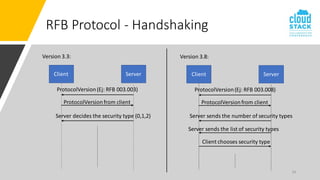
The document outlines enhancements for CloudStack 4.18, including a new API for VM console access, optional security validation for console proxy access, and websocket traffic port encryption. It discusses improvements to the virtual network computing (VNC) framework and the implementation of TLS security for KVM VM console connections. Key features include supporting rfb protocols from version 3.3 to 3.8 and introducing vencrypt and x509vnc security types.