Japan Vyatta Users Group Introduction
•
1 like•746 views
The Japan Vyatta Users Group was started in 2010 to connect users of the open-source networking operating system Vyatta in Japan. The group holds regular meetings in different cities around Japan to discuss topics like connecting cloud environments and direct server load balancing using Vyatta. It has published a Japanese book on Vyatta and continues to organize semi-annual user meetings.
Report
Share
Report
Share
Download to read offline
Recommended
VyattaCore TIPS2013

VyattaCore TIPS2013
05 Apr, 2013
SAKURA Internet Research Center
Senior Researcher / Naoto MATSUMOTO
Software-Based Networking & Security for the Cloud

As the old appliance model in network infrastructures of datacenters and clouds is being replaced by software and virtual machines, next-generation network security is paving the way for secure migration into the cloud. While one of the key benefits of the cloud is network access from any location, this brings to light critical issues including access restrictions and, more importantly, who controls it. Can providers support VPNs or dedicated connections in the IaaS cloud? This session will cover secure cloud migrations and detail the benefits of the customer-controlled virtual firewall, VPN and IPS in the IaaS cloud.
Unbreakable VPN using Vyatta/VyOS - HOW TO -

Unbreakable VPN using Vyatta/VyOS - HOW TO -
13 May, 2014
SAKURA Internet Research Center
Senior Researcher / Naoto MATSUMOTO
Alder Lake-S CPU Temperature Monitoring

Alder Lake-S CPU Temperature Monitoring
15th Nov, 2021
SAKURA Internet Research Center.
Senior Researcher / Naoto MATSUMOTO
Recommended
VyattaCore TIPS2013

VyattaCore TIPS2013
05 Apr, 2013
SAKURA Internet Research Center
Senior Researcher / Naoto MATSUMOTO
Software-Based Networking & Security for the Cloud

As the old appliance model in network infrastructures of datacenters and clouds is being replaced by software and virtual machines, next-generation network security is paving the way for secure migration into the cloud. While one of the key benefits of the cloud is network access from any location, this brings to light critical issues including access restrictions and, more importantly, who controls it. Can providers support VPNs or dedicated connections in the IaaS cloud? This session will cover secure cloud migrations and detail the benefits of the customer-controlled virtual firewall, VPN and IPS in the IaaS cloud.
Unbreakable VPN using Vyatta/VyOS - HOW TO -

Unbreakable VPN using Vyatta/VyOS - HOW TO -
13 May, 2014
SAKURA Internet Research Center
Senior Researcher / Naoto MATSUMOTO
Alder Lake-S CPU Temperature Monitoring

Alder Lake-S CPU Temperature Monitoring
15th Nov, 2021
SAKURA Internet Research Center.
Senior Researcher / Naoto MATSUMOTO
2023年以降のサーバークラスタリング設計(メモ)

2023年以降のサーバークラスタリング設計(メモ)
2021年02月02日
さくらインターネット株式会社
さくらインターネット研究所
上級研究員 松本直人
LTE-M/NB IoTを試してみる nRF9160/Thingy:91

LTE-M/NB IoTを試してみる nRF9160/Thingy:91
2020年07月22日
さくらインターネット株式会社
さくらインターネット研究所
上級研究員 松本直人
災害時における無線モニタリングによる社会インフラの見える化

災害時における無線モニタリングによる社会インフラの見える化
2020年05月15日
さくらインターネット株式会社
さくらインターネット研究所
上級研究員 松本直人
上級研究員 菊地俊介
BeautifulSoup / selenium Deep dive

BeautifulSoup / Selenium Deep dive
06th May, 2020
SAKURA Internet Research Center.
Senior Researcher / Naoto MATSUMOTO
AMDGPU ROCm Deep dive

AMDGPU ROCm Deep dive
06th May, 2020
SAKURA Internet Research Center.
Senior Researcher / Naoto MATSUMOTO
Network Adapter Deep dive

Network Adapter Deep dive
06th May, 2020
SAKURA Internet Research Center.
Senior Researcher / Naoto MATSUMOTO
RTL2838 DVB-T Deep dive

RTL2838 DVB-T Deep dive
06th May, 2020
SAKURA Internet Research Center.
Senior Researcher / Naoto MATSUMOTO
x86_64 Hardware Deep dive

x86_64 Hardware Deep dive
06th May, 2020
SAKURA Internet Research Center.
Senior Researcher / Naoto MATSUMOTO
ADS-B, AIS, APRS cheatsheet

ADS-B, AIS, APRS cheatsheet
06th May, 2020
SAKURA Internet Research Center.
Senior Researcher / Naoto MATSUMOTO
curl --http3 cheatsheet

curl --http3 cheatsheet
06th May, 2020
SAKURA Internet Research Center.
Senior Researcher / Naoto MATSUMOTO
3/4G USB modem Cheat Sheet

3/4G USB modem Cheat Sheet
06th May, 2020
SAKURA Internet Research Center.
Senior Researcher / Naoto MATSUMOTO
How To Train Your ARM(SBC)

How To Train Your ARM(SBC)
06th May, 2020
SAKURA Internet Research Center.
Senior Researcher / Naoto MATSUMOTO
全国におけるCOVID-19対策の見える化 ~宿泊業の場合~

全国におけるCOVID-19対策の見える化 ~宿泊業の場合~
さくらインターネット株式会社
さくらインターネット研究所
上級研究員 松本直人
2020年03月08日
我が国の電波の使用状況/携帯電話向け割当 (2019年3月1日現在)

我が国の電波の使用状況/携帯電話向け割当 (2019年3月1日現在)
出典: 総務省
https://www.soumu.go.jp/main_content/000572034.pdf
https://www.tele.soumu.go.jp/resource/search/myuse/use/335m.pdf
https://www.tele.soumu.go.jp/resource/search/myuse/use/960m.pdf
https://www.tele.soumu.go.jp/resource/search/myuse/use/10000m.pdf
https://www.tele.soumu.go.jp/j/adm/freq/search/myuse/use/index.htm
私たちに訪れる(かもしれない)未来と計算機によるモノコトの見える化

私たちに訪れる(かもしれない)未来と計算機によるモノコトの見える化
”3~5年後に使われる(かもしれない)技術領域の研究テーマ"2020
さくらインターネット株式会社
さくらインターネット研究所
上級研究員 松本直人
2020年01月05日
仮想化環境におけるバイナリー・ポータビリティの考察 (WebAssemblyの場合)

仮想化環境におけるバイナリー・ポータビリティの考察 (WebAssemblyの場合)
さくらインターネット株式会社
さくらインターネット研究所
上級研究員 松本直人
2019年12月28日
インターネットを用いたニア・リアルタイムでの災害観測の考察

インターネットを用いたニア・リアルタイムでの災害観測の考察
災害コミュニケーションシンポジウム2019
さくらインターネット研究所
上級研究員 松本直人
2019年12月26日
AMD Ryzen Threadripper 3960X によるPCIe 4.0 x16x16x16環境の詳解

AMD Ryzen Threadripper 3960X によるPCIe 4.0 x16x16x16環境の詳解
2019年12月12日
さくらインターネット株式会社
さくらインターネット研究所
上級研究員 / 松本直人
When stars align: studies in data quality, knowledge graphs, and machine lear...

Keynote at DQMLKG workshop at the 21st European Semantic Web Conference 2024
More Related Content
More from Naoto MATSUMOTO
2023年以降のサーバークラスタリング設計(メモ)

2023年以降のサーバークラスタリング設計(メモ)
2021年02月02日
さくらインターネット株式会社
さくらインターネット研究所
上級研究員 松本直人
LTE-M/NB IoTを試してみる nRF9160/Thingy:91

LTE-M/NB IoTを試してみる nRF9160/Thingy:91
2020年07月22日
さくらインターネット株式会社
さくらインターネット研究所
上級研究員 松本直人
災害時における無線モニタリングによる社会インフラの見える化

災害時における無線モニタリングによる社会インフラの見える化
2020年05月15日
さくらインターネット株式会社
さくらインターネット研究所
上級研究員 松本直人
上級研究員 菊地俊介
BeautifulSoup / selenium Deep dive

BeautifulSoup / Selenium Deep dive
06th May, 2020
SAKURA Internet Research Center.
Senior Researcher / Naoto MATSUMOTO
AMDGPU ROCm Deep dive

AMDGPU ROCm Deep dive
06th May, 2020
SAKURA Internet Research Center.
Senior Researcher / Naoto MATSUMOTO
Network Adapter Deep dive

Network Adapter Deep dive
06th May, 2020
SAKURA Internet Research Center.
Senior Researcher / Naoto MATSUMOTO
RTL2838 DVB-T Deep dive

RTL2838 DVB-T Deep dive
06th May, 2020
SAKURA Internet Research Center.
Senior Researcher / Naoto MATSUMOTO
x86_64 Hardware Deep dive

x86_64 Hardware Deep dive
06th May, 2020
SAKURA Internet Research Center.
Senior Researcher / Naoto MATSUMOTO
ADS-B, AIS, APRS cheatsheet

ADS-B, AIS, APRS cheatsheet
06th May, 2020
SAKURA Internet Research Center.
Senior Researcher / Naoto MATSUMOTO
curl --http3 cheatsheet

curl --http3 cheatsheet
06th May, 2020
SAKURA Internet Research Center.
Senior Researcher / Naoto MATSUMOTO
3/4G USB modem Cheat Sheet

3/4G USB modem Cheat Sheet
06th May, 2020
SAKURA Internet Research Center.
Senior Researcher / Naoto MATSUMOTO
How To Train Your ARM(SBC)

How To Train Your ARM(SBC)
06th May, 2020
SAKURA Internet Research Center.
Senior Researcher / Naoto MATSUMOTO
全国におけるCOVID-19対策の見える化 ~宿泊業の場合~

全国におけるCOVID-19対策の見える化 ~宿泊業の場合~
さくらインターネット株式会社
さくらインターネット研究所
上級研究員 松本直人
2020年03月08日
我が国の電波の使用状況/携帯電話向け割当 (2019年3月1日現在)

我が国の電波の使用状況/携帯電話向け割当 (2019年3月1日現在)
出典: 総務省
https://www.soumu.go.jp/main_content/000572034.pdf
https://www.tele.soumu.go.jp/resource/search/myuse/use/335m.pdf
https://www.tele.soumu.go.jp/resource/search/myuse/use/960m.pdf
https://www.tele.soumu.go.jp/resource/search/myuse/use/10000m.pdf
https://www.tele.soumu.go.jp/j/adm/freq/search/myuse/use/index.htm
私たちに訪れる(かもしれない)未来と計算機によるモノコトの見える化

私たちに訪れる(かもしれない)未来と計算機によるモノコトの見える化
”3~5年後に使われる(かもしれない)技術領域の研究テーマ"2020
さくらインターネット株式会社
さくらインターネット研究所
上級研究員 松本直人
2020年01月05日
仮想化環境におけるバイナリー・ポータビリティの考察 (WebAssemblyの場合)

仮想化環境におけるバイナリー・ポータビリティの考察 (WebAssemblyの場合)
さくらインターネット株式会社
さくらインターネット研究所
上級研究員 松本直人
2019年12月28日
インターネットを用いたニア・リアルタイムでの災害観測の考察

インターネットを用いたニア・リアルタイムでの災害観測の考察
災害コミュニケーションシンポジウム2019
さくらインターネット研究所
上級研究員 松本直人
2019年12月26日
AMD Ryzen Threadripper 3960X によるPCIe 4.0 x16x16x16環境の詳解

AMD Ryzen Threadripper 3960X によるPCIe 4.0 x16x16x16環境の詳解
2019年12月12日
さくらインターネット株式会社
さくらインターネット研究所
上級研究員 / 松本直人
More from Naoto MATSUMOTO (20)
AMD Ryzen Threadripper 3960X によるPCIe 4.0 x16x16x16環境の詳解

AMD Ryzen Threadripper 3960X によるPCIe 4.0 x16x16x16環境の詳解
Recently uploaded
When stars align: studies in data quality, knowledge graphs, and machine lear...

Keynote at DQMLKG workshop at the 21st European Semantic Web Conference 2024
By Design, not by Accident - Agile Venture Bolzano 2024

As presented at the Agile Venture Bolzano, 4.06.2024
Epistemic Interaction - tuning interfaces to provide information for AI support

Paper presented at SYNERGY workshop at AVI 2024, Genoa, Italy. 3rd June 2024
https://alandix.com/academic/papers/synergy2024-epistemic/
As machine learning integrates deeper into human-computer interactions, the concept of epistemic interaction emerges, aiming to refine these interactions to enhance system adaptability. This approach encourages minor, intentional adjustments in user behaviour to enrich the data available for system learning. This paper introduces epistemic interaction within the context of human-system communication, illustrating how deliberate interaction design can improve system understanding and adaptation. Through concrete examples, we demonstrate the potential of epistemic interaction to significantly advance human-computer interaction by leveraging intuitive human communication strategies to inform system design and functionality, offering a novel pathway for enriching user-system engagements.
Transcript: Selling digital books in 2024: Insights from industry leaders - T...

The publishing industry has been selling digital audiobooks and ebooks for over a decade and has found its groove. What’s changed? What has stayed the same? Where do we go from here? Join a group of leading sales peers from across the industry for a conversation about the lessons learned since the popularization of digital books, best practices, digital book supply chain management, and more.
Link to video recording: https://bnctechforum.ca/sessions/selling-digital-books-in-2024-insights-from-industry-leaders/
Presented by BookNet Canada on May 28, 2024, with support from the Department of Canadian Heritage.
Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head...

Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head of Product, Amazon Games
Builder.ai Founder Sachin Dev Duggal's Strategic Approach to Create an Innova...

In today's fast-changing business world, Companies that adapt and embrace new ideas often need help to keep up with the competition. However, fostering a culture of innovation takes much work. It takes vision, leadership and willingness to take risks in the right proportion. Sachin Dev Duggal, co-founder of Builder.ai, has perfected the art of this balance, creating a company culture where creativity and growth are nurtured at each stage.
Generative AI Deep Dive: Advancing from Proof of Concept to Production

Join Maher Hanafi, VP of Engineering at Betterworks, in this new session where he'll share a practical framework to transform Gen AI prototypes into impactful products! He'll delve into the complexities of data collection and management, model selection and optimization, and ensuring security, scalability, and responsible use.
De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovati...

De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovation With Your Product by VP of Product Design, Warner Music Group
Accelerate your Kubernetes clusters with Varnish Caching

A presentation about the usage and availability of Varnish on Kubernetes. This talk explores the capabilities of Varnish caching and shows how to use the Varnish Helm chart to deploy it to Kubernetes.
This presentation was delivered at K8SUG Singapore. See https://feryn.eu/presentations/accelerate-your-kubernetes-clusters-with-varnish-caching-k8sug-singapore-28-2024 for more details.
Assuring Contact Center Experiences for Your Customers With ThousandEyes

Presented by Suzanne Phillips and Alex Marcotte
Encryption in Microsoft 365 - ExpertsLive Netherlands 2024

In this session I delve into the encryption technology used in Microsoft 365 and Microsoft Purview. Including the concepts of Customer Key and Double Key Encryption.
Bits & Pixels using AI for Good.........

A whirlwind tour of tech & AI for socio-environmental impact.
Leading Change strategies and insights for effective change management pdf 1.pdf

Leading Change strategies and insights for effective change management pdf 1.pdf
Elizabeth Buie - Older adults: Are we really designing for our future selves?

Elizabeth Buie - Older adults: Are we really designing for our future selves?
DevOps and Testing slides at DASA Connect

My and Rik Marselis slides at 30.5.2024 DASA Connect conference. We discuss about what is testing, then what is agile testing and finally what is Testing in DevOps. Finally we had lovely workshop with the participants trying to find out different ways to think about quality and testing in different parts of the DevOps infinity loop.
Recently uploaded (20)
When stars align: studies in data quality, knowledge graphs, and machine lear...

When stars align: studies in data quality, knowledge graphs, and machine lear...
Secstrike : Reverse Engineering & Pwnable tools for CTF.pptx

Secstrike : Reverse Engineering & Pwnable tools for CTF.pptx
FIDO Alliance Osaka Seminar: FIDO Security Aspects.pdf

FIDO Alliance Osaka Seminar: FIDO Security Aspects.pdf
By Design, not by Accident - Agile Venture Bolzano 2024

By Design, not by Accident - Agile Venture Bolzano 2024
Epistemic Interaction - tuning interfaces to provide information for AI support

Epistemic Interaction - tuning interfaces to provide information for AI support
Transcript: Selling digital books in 2024: Insights from industry leaders - T...

Transcript: Selling digital books in 2024: Insights from industry leaders - T...
Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head...

Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head...
Builder.ai Founder Sachin Dev Duggal's Strategic Approach to Create an Innova...

Builder.ai Founder Sachin Dev Duggal's Strategic Approach to Create an Innova...
Generative AI Deep Dive: Advancing from Proof of Concept to Production

Generative AI Deep Dive: Advancing from Proof of Concept to Production
De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovati...

De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovati...
Accelerate your Kubernetes clusters with Varnish Caching

Accelerate your Kubernetes clusters with Varnish Caching
Assuring Contact Center Experiences for Your Customers With ThousandEyes

Assuring Contact Center Experiences for Your Customers With ThousandEyes
Encryption in Microsoft 365 - ExpertsLive Netherlands 2024

Encryption in Microsoft 365 - ExpertsLive Netherlands 2024
Leading Change strategies and insights for effective change management pdf 1.pdf

Leading Change strategies and insights for effective change management pdf 1.pdf
Elizabeth Buie - Older adults: Are we really designing for our future selves?

Elizabeth Buie - Older adults: Are we really designing for our future selves?
Free Complete Python - A step towards Data Science

Free Complete Python - A step towards Data Science
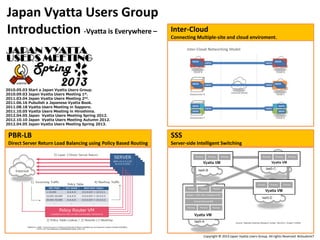
Japan Vyatta Users Group Introduction
- 1. Japan Vyatta Users Group Introduction -Vyatta is Everywhere – Inter-Cloud Connecting Multiple-site and cloud enviroment. 2010.05.03 Start a Japan Vyatta Users Group. 2010.09.03 Japan Vyatta Users Meeting 1st. 2011.03.04 Japan Vyatta Users Meeting 2nd. 2011.06.16 Pubulish a Japanese Vyatta Book. 2011.08.18 Vyatta Users Meeting in Sapporo. 2011.10.05 Vyatta Users Meeting in Hiroshima. 2012.04.05 Japan Vyatta Users Meeting Spring 2012. 2012.10.10 Japan Vyatta Users Meeting Autumn 2012. 2012.04.05 Japan Vyatta Users Meeting Spring 2013. PBR-LB SSS Direct Server Return Load Balancing using Policy Based Routing Server-side Intelligent Switching Copyright © 2013 Japan Vyatta Users Group. All rights Reserved. #cloudmix7
