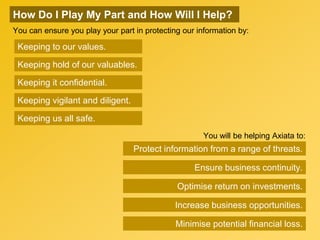
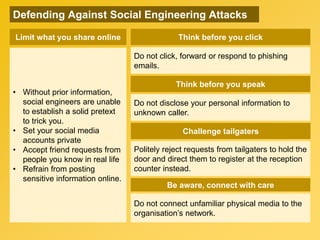
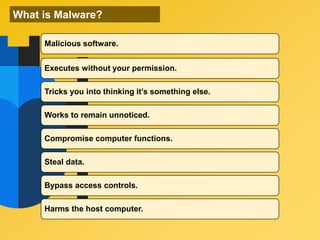
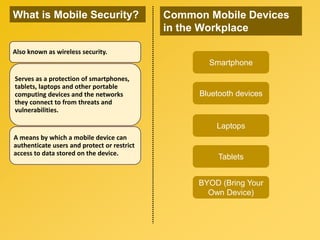
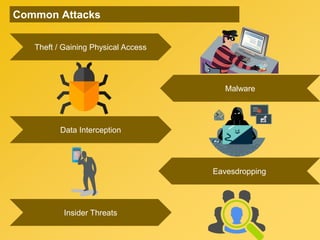
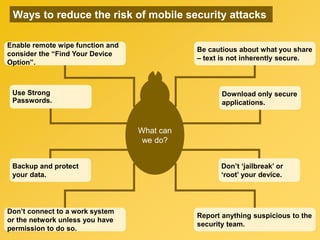
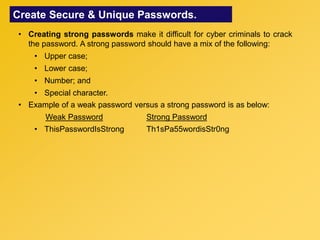
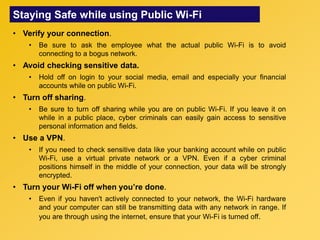
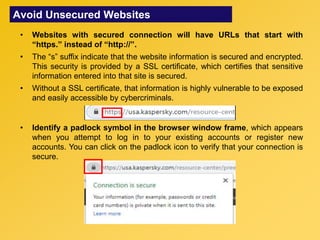
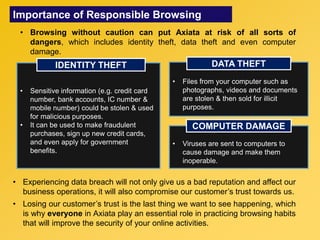
This document provides information about an e-learning cyber security induction course for Axiata employees. The course aims to promote information security awareness around topics like introduction to security, social engineering, malware, mobile security, and responsible browsing. It serves as an induction for new employees and a refresher for existing employees. The course objectives are to understand information security and how to protect it, recognize social engineering techniques, be aware of malware types and prevention methods, understand mobile security risks and defenses, and learn responsible browsing practices. The course content will cover these topics through modules on introduction to security, social engineering, mobile security and social media, responsible browsing, and malware. Upon completing the course, participants will understand these cyber security concepts and