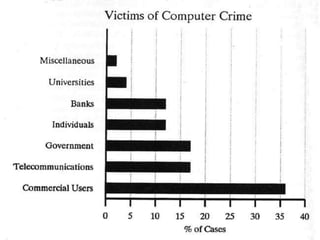
This document discusses cyber crime and provides an overview of the topic. It defines cyber crime as illegal activities committed using computers and networks. The document then covers the history of cyber crime, types of cyber criminals, common types of cyber crimes like hacking and viruses, the rising issue of cyber crime in Pakistan, and concludes with recommendations for protecting computers like using antivirus software and strong passwords.