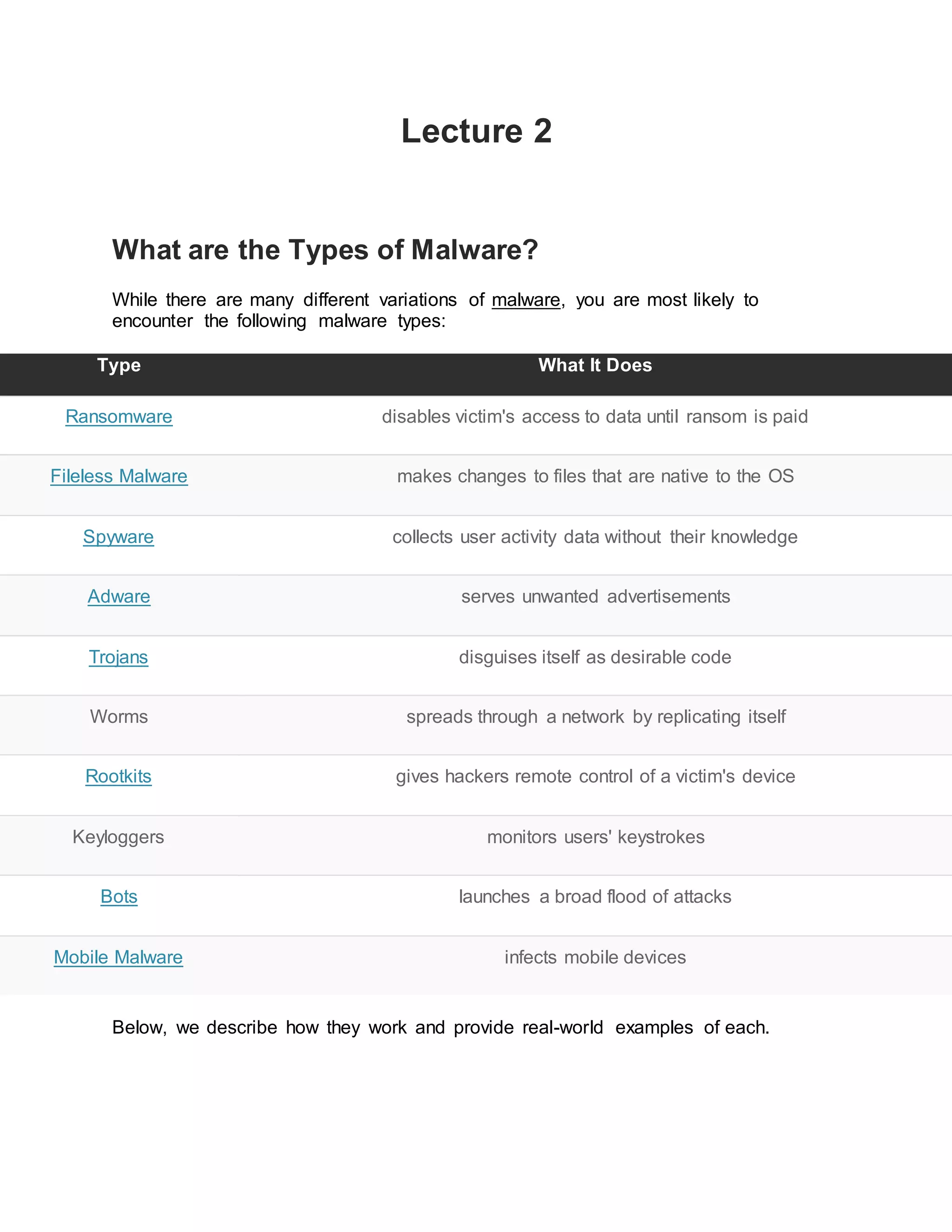
Ransomware, fileless malware, spyware, adware, trojans, worms, rootkits, keyloggers, bots, and mobile malware are the main types of malware. Ransomware disables access to data until ransom is paid, while fileless malware makes changes to operating system files without installing anything. Spyware collects user activity data secretly and adware serves unwanted ads based on user activity tracking. Trojans disguise as desirable software but take control of systems. Worms spread through networks, while rootkits give remote control of devices. Keyloggers monitor keystrokes and bots/botnets launch broad attacks through networks of infected devices. Mobile malware also infects phones and tablets.