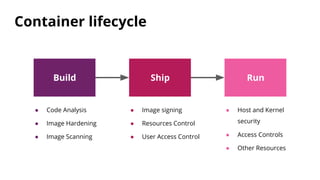
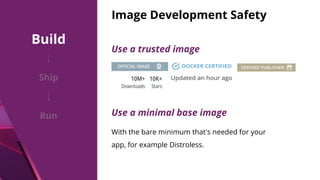
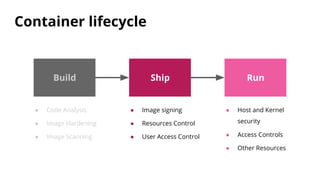
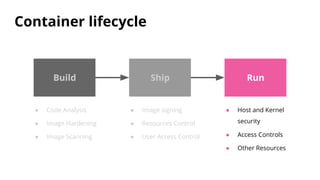
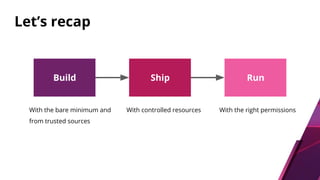
The document discusses security challenges and best practices for Docker containers. It outlines risks at different stages of the container lifecycle from image development to deployment. Key risks include lack of isolation, complex ecosystems, and known vulnerabilities. The document recommends practices like using linting and scanning during development, restricting resources and access controls at deployment, and signing images from trusted sources to improve container security.