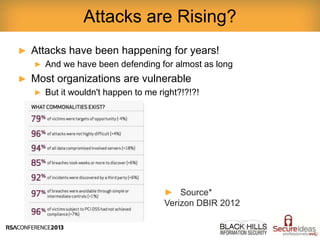
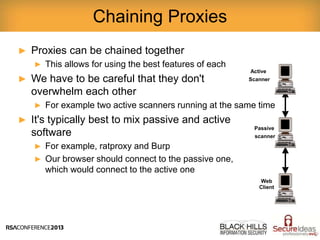
This document provides a summary of a presentation on tactical security operations. It discusses how security incidents are increasing and examines different types of security testing, including network scanning, web application testing, and user awareness testing. The presentation provides examples of security tools that can be used for each type of testing and recommends learning how to properly use these tools. It emphasizes the importance of consistent security testing to measure vulnerabilities over time.