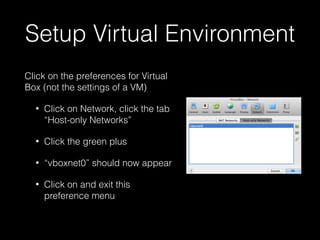
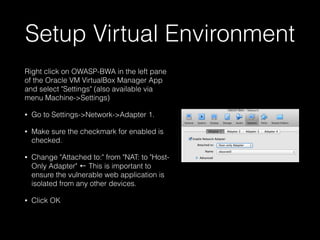
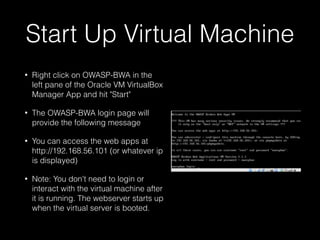
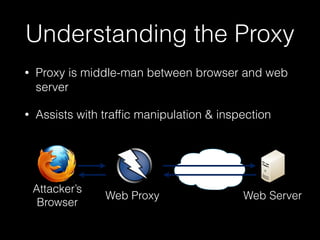
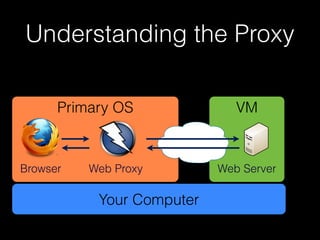
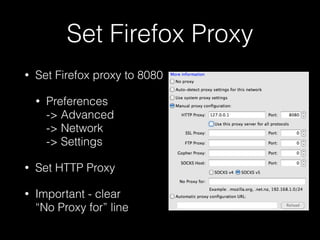
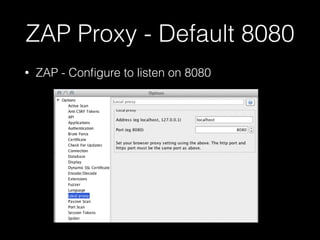
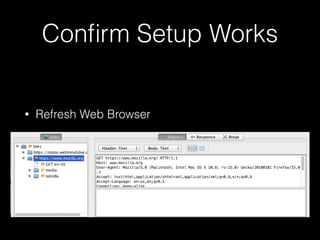
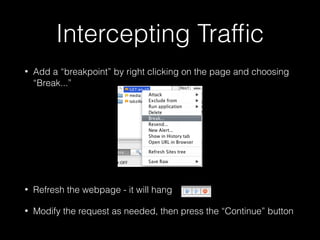
This document provides a step-by-step guide for setting up a virtual security training lab using OWASP's Broken Web App (BWA) and ZAP tools. It includes instructions for configuring a virtual machine, establishing a proxy connection, and testing connectivity to the web applications. Additionally, it highlights how to manipulate and intercept web traffic through the proxy during security testing.