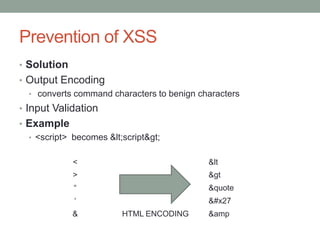
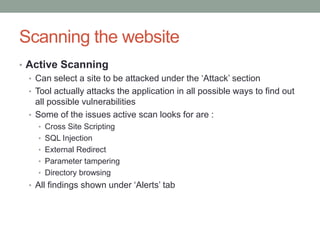
The document is a final report on the OWASP Zed Attack Proxy (ZAP), which is an open-source penetration testing tool designed for identifying vulnerabilities in web applications. It provides an overview of the OWASP, its history, top application security risks, and detailed features of ZAP including scanning methods and preventative measures against common vulnerabilities like XSS and SQL injection. The report concludes that ZAP aims to improve online security by offering a user-friendly, extensible platform for security testing and emphasizes the project's commitment to community-driven development.