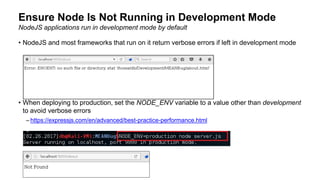
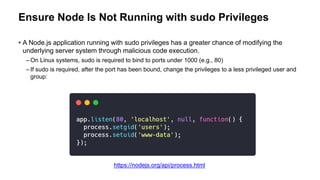
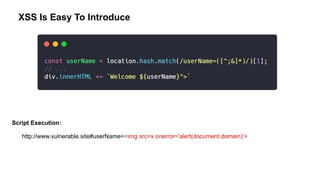
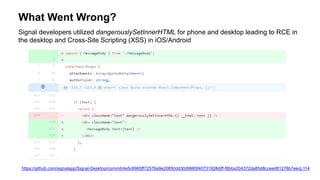
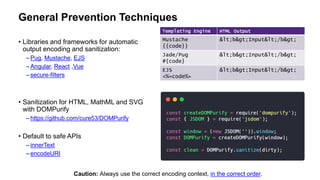
The document provides an overview of the OWASP Top 10 vulnerabilities specifically relevant to JavaScript developers, highlighting critical web application security risks based on data from 2014-2017. It details vulnerabilities such as injection flaws, broken authentication, and cross-site scripting, along with prevention techniques and best practices for secure coding. Resources for further reading and tools for security analysis are also recommended for developers to mitigate risks in their applications.



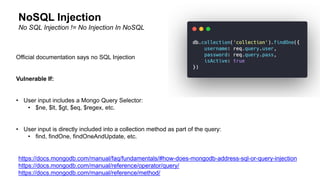
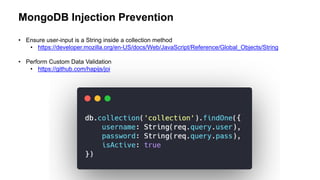
![Query Output:
Vulnerable MongoDB Login Example
Injection:
https://url.to/login?user=admin&pass[$ne]=](https://image.slidesharecdn.com/appsectelavivowasptop1030minutes-190531140010/85/AppSec-Tel-Aviv-OWASP-Top-10-For-JavaScript-Developers-6-320.jpg)


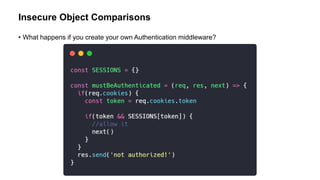
![Comparison Table
Value Return
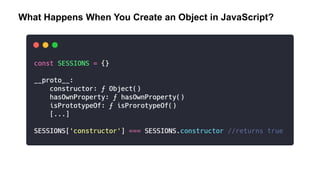
SESSIONS['invalidString'] False
SESSIONS[''] False
SESSIONS['constructor'] True
SESSIONS['hasOwnPropery'] True](https://image.slidesharecdn.com/appsectelavivowasptop1030minutes-190531140010/85/AppSec-Tel-Aviv-OWASP-Top-10-For-JavaScript-Developers-13-320.jpg)