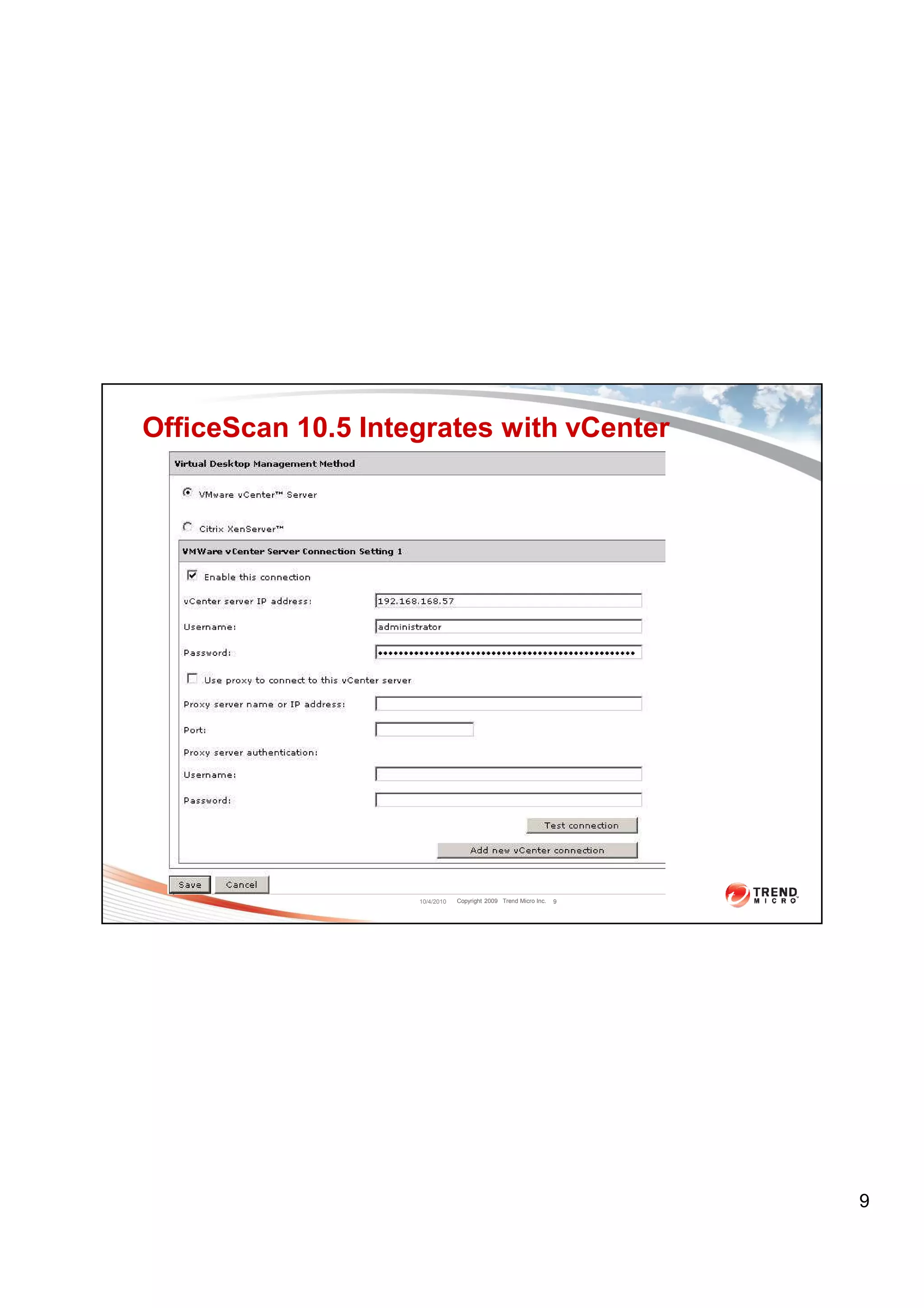
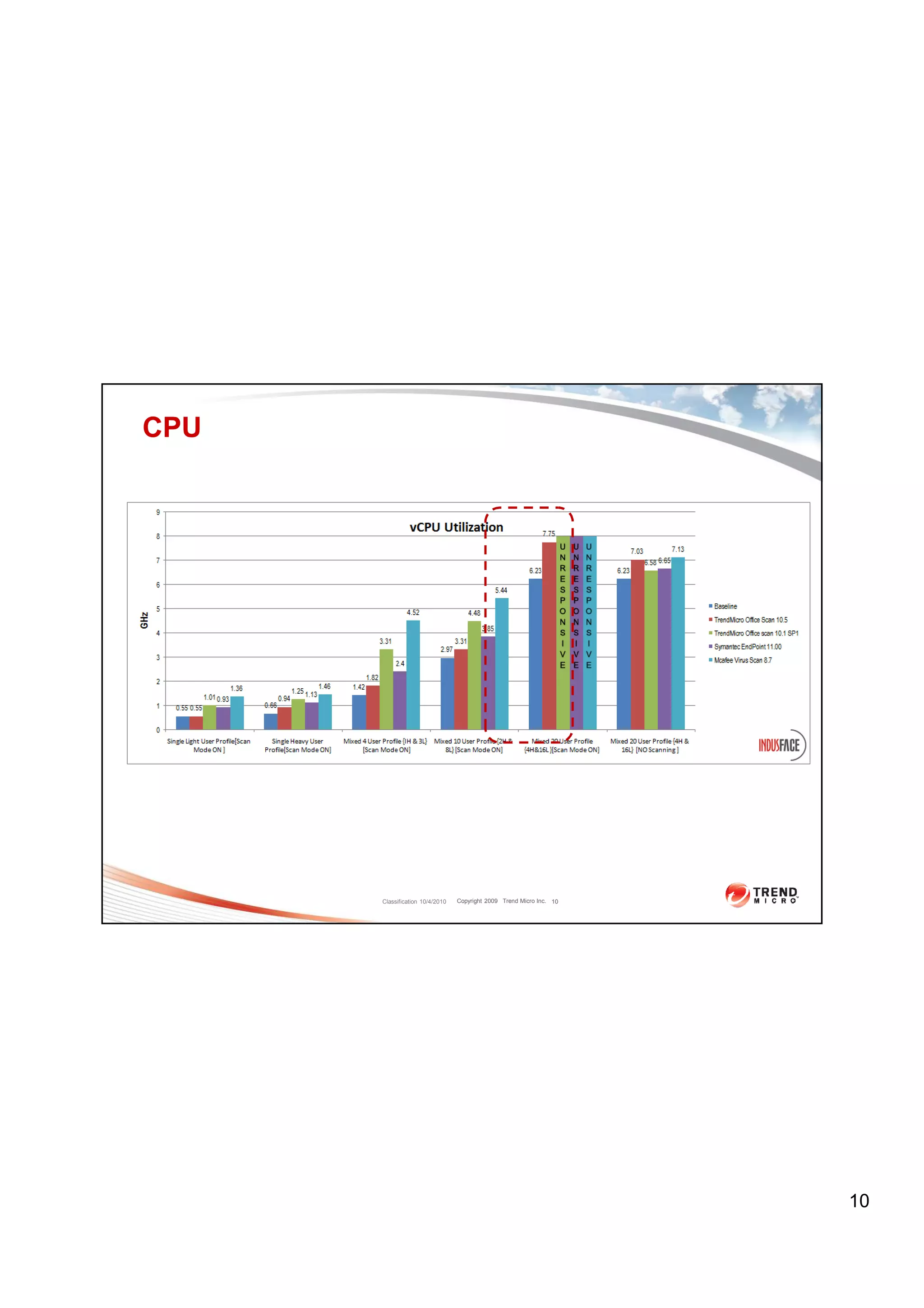
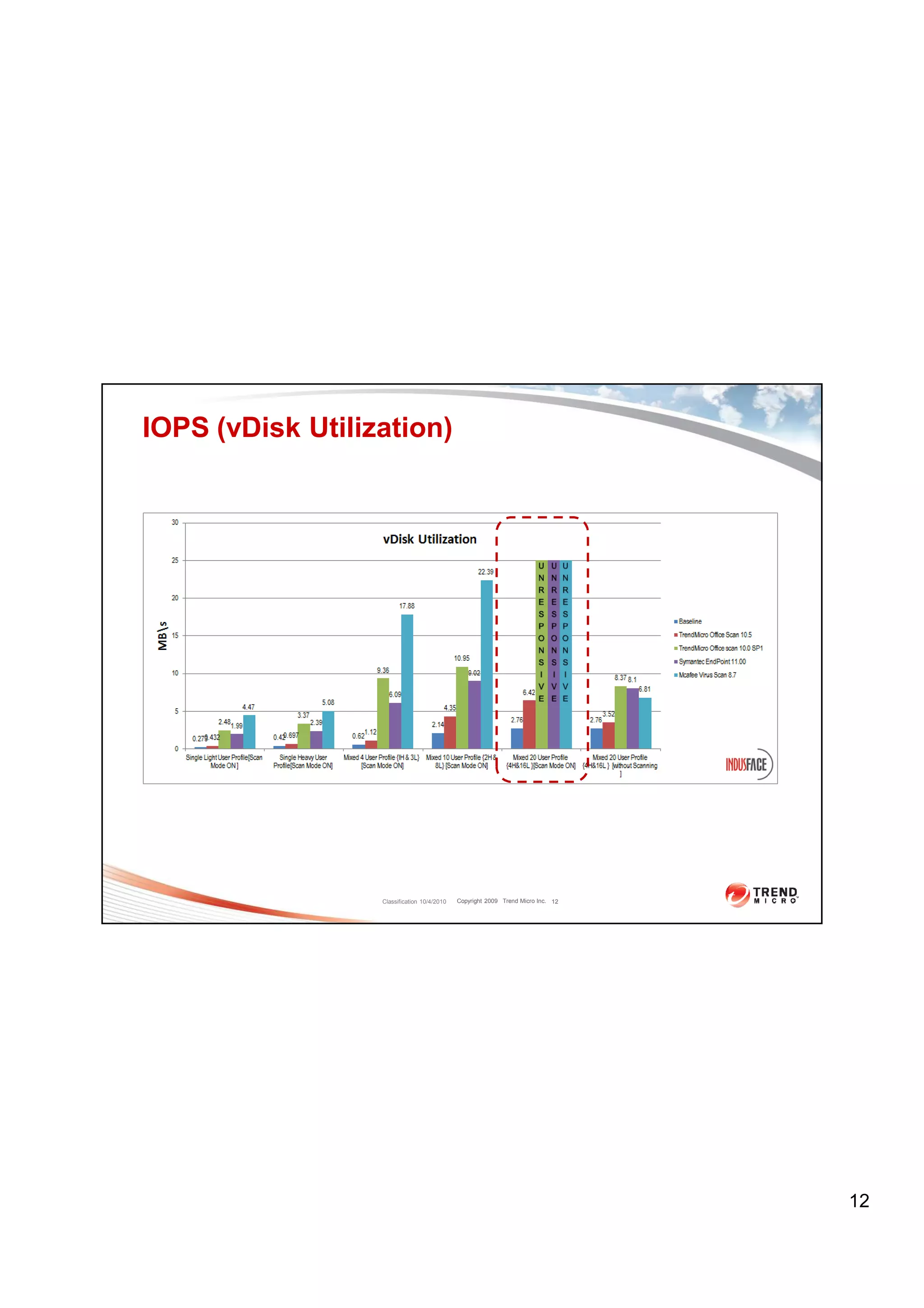
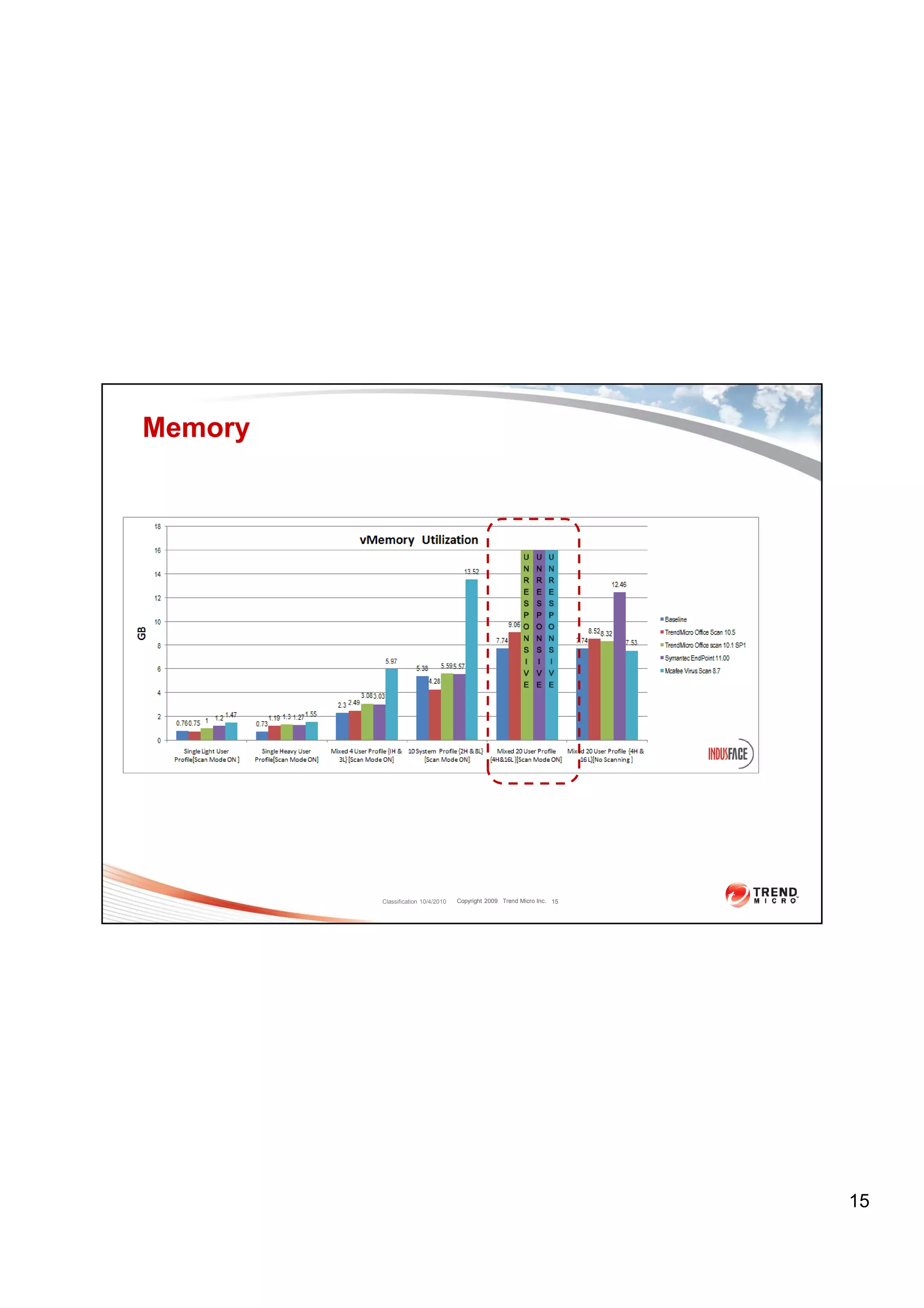
The document discusses virtual desktop infrastructure (VDI) security solutions from Trend Micro, focusing on Trend Micro OfficeScan and Deep Security. It provides performance comparisons of OfficeScan against other antivirus solutions, showing that OfficeScan uses significantly less CPU, IOPS, memory and scan time. It also introduces Deep Security as Trend Micro's agentless security solution that eliminates "AV storms" through hypervisor-based inspection.