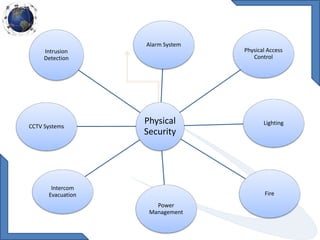
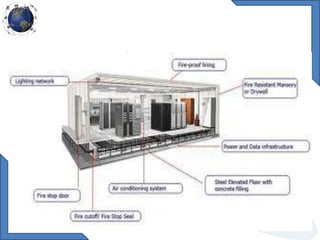
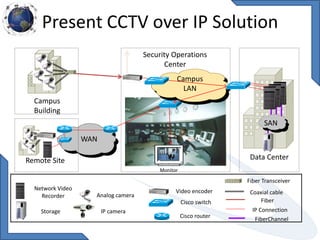
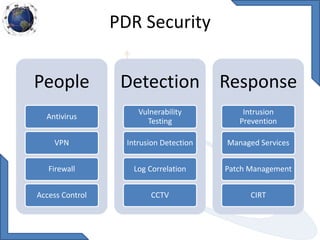
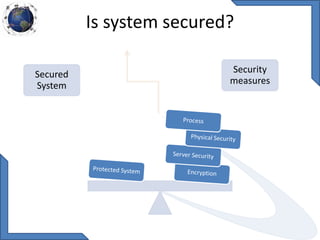
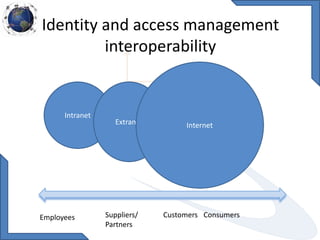
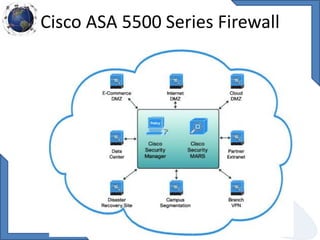
This document discusses requirements for physical and information security systems for data centers. It outlines two major types of protection: physical security, involving safeguarding assets and personnel through controls like access points, alarms and cameras; and information security, protecting data through measures such as firewalls, antivirus software and identity management. The document provides steps for physical security including site placement, utilities redundancy, and access limitations. It also presents examples of Cisco security products that can be used like the ASA firewall and NAC appliance for network admission control.