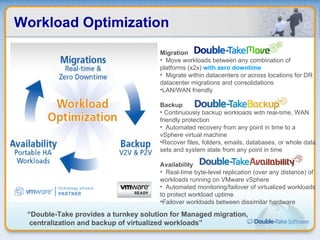
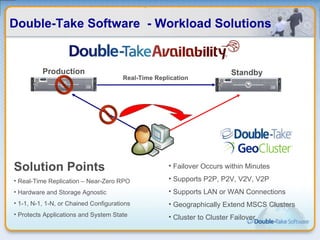
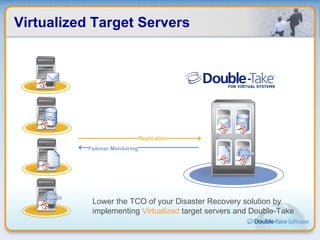
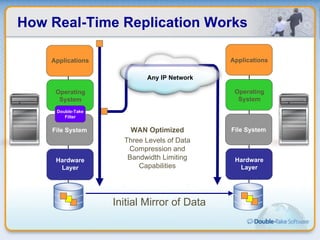
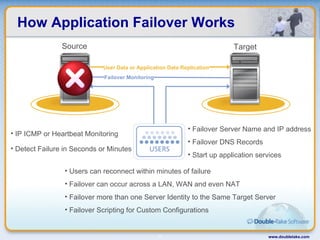
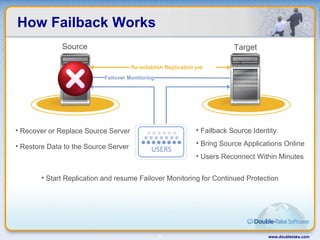
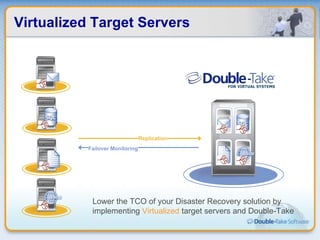
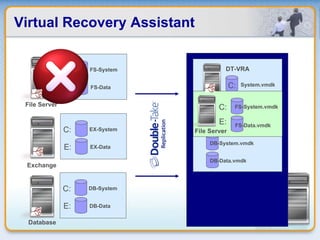
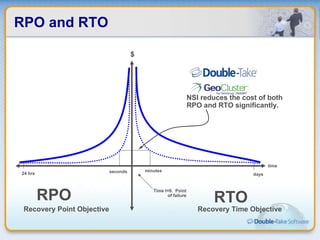
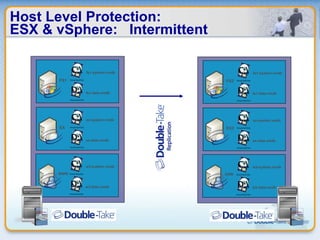
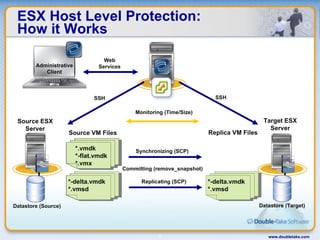
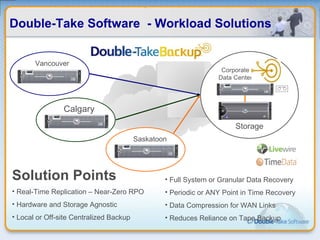
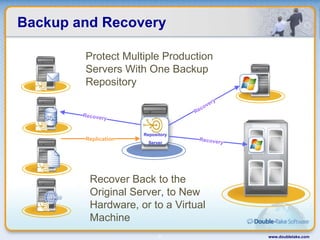
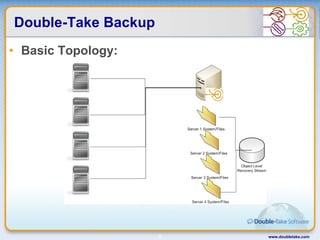
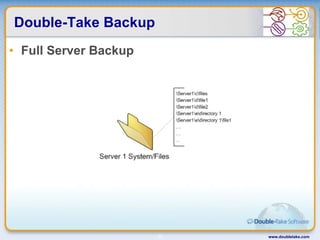
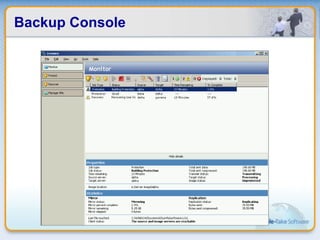
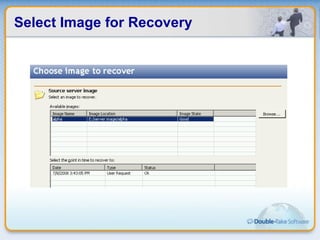
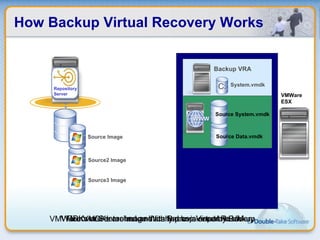
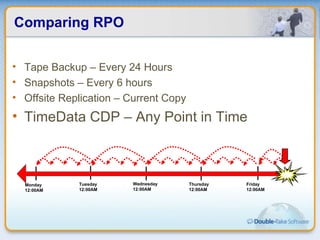
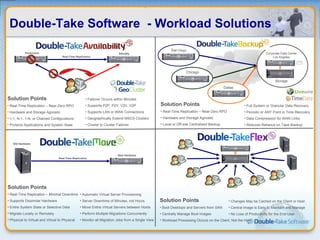
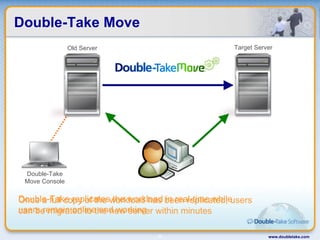
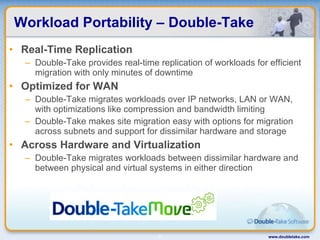
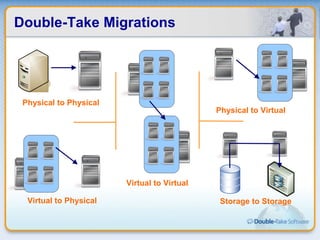
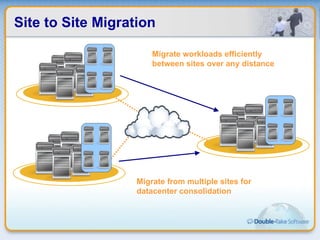
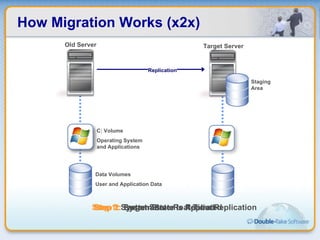
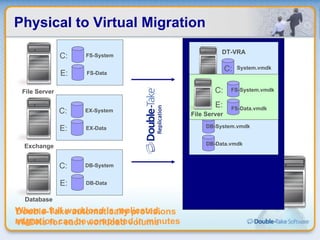
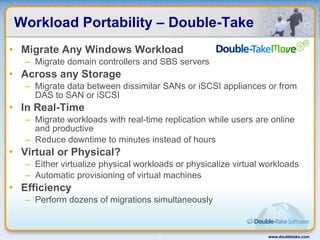
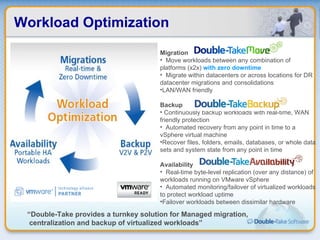
Double-Take Software provides workload optimization solutions such as disaster recovery, high availability, server migration, and backup/management. It focuses on virtualized workload protection and has over 19,000 customers including over half of the Fortune 500. Double-Take's solutions provide real-time replication, hardware agnostic protection, automated failover and recovery in minutes, and WAN-optimized migration and backup.
![Workload Optimization Karl Oman, Sr. Solutions Architect Double-Take Software (Canada) [email_address] www.doubletake.com](https://image.slidesharecdn.com/vmwareusersgroup-canada-koedit-22feb2010-revx1-101020145934-phpapp02/75/Double-Take-Software-1-2048.jpg)