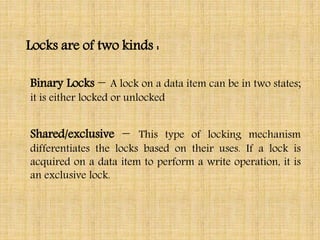
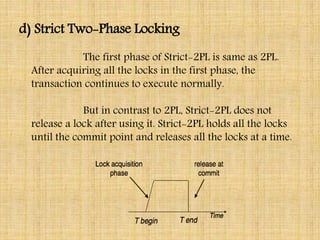
This document discusses transaction management and concurrency control. It summarizes two main categories of concurrency control protocols: lock-based protocols and timestamp-based protocols. For lock-based protocols, it describes four types: simplistic locking, pre-claiming, two-phase locking (2PL), and strict 2PL. For timestamp-based protocols, it explains how each transaction is assigned a timestamp and how read/write rules ensure serializability based on timestamp ordering.