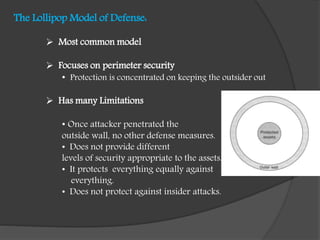
This document discusses risk analysis and defense models for network security. It begins by outlining the components of risk analysis: asset identification and valuation, threat definition, and likelihood and impact analysis. Common threats include computer theft, exposure of confidential information, financial fraud, and denial of service attacks. Threat vectors describe where threats originate and which assets are exposed. The document then examines three defense models: the lollipop model which focuses on perimeter security, the onion model with multiple layered defenses, and identifying zones of trust within a network with varying levels of security for different areas.