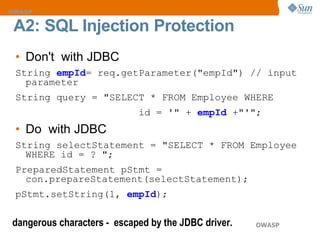
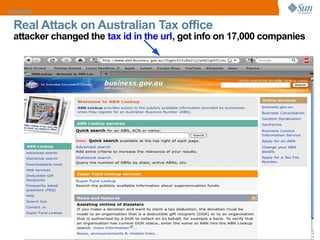
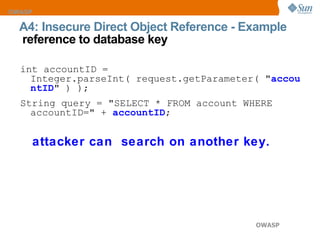
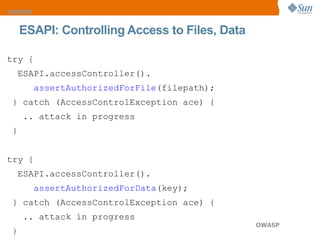
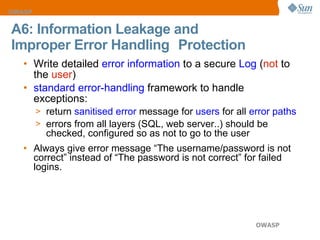
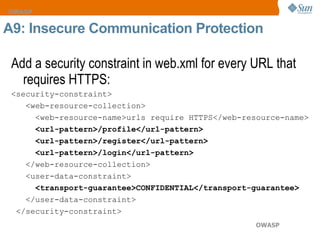
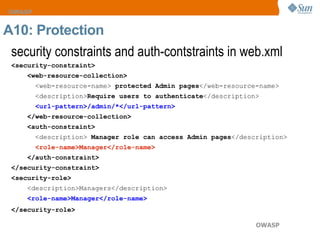
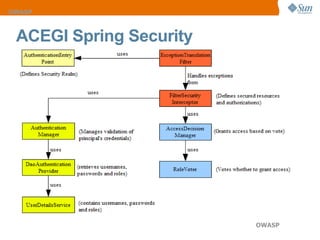
The document discusses the OWASP Top 10 web security vulnerabilities, emphasizing the importance of secure web application development. Key vulnerabilities include Cross-Site Scripting (XSS), SQL Injection, and Insecure Direct Object References, with protective measures outlined for each. The content also highlights best practices for input validation, output encoding, and proper error handling to mitigate security risks.











![Validating Input with Java String regex = "[\\s\\w-,]*"; Pattern pattern = Pattern.compile(regex); validate(stringToValidate, pattern); Validating Input with JSF 2.0 <h:inputText id="creditCard" value="#{booking.creditCardNumber}"/> A1 Cross Site Scripting Protection](https://image.slidesharecdn.com/top10security-12556277819898-phpapp01/85/Top-10-Web-Security-Vulnerabilities-13-320.jpg)