The document discusses IEEE 802 subgroups and local area network (LAN) technologies such as token bus and token ring. It provides details on:
- IEEE 802 subgroups and their responsibilities for various networking standards
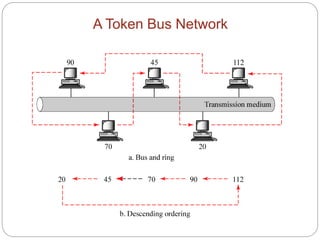
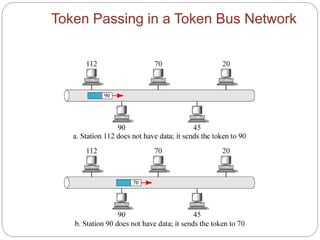
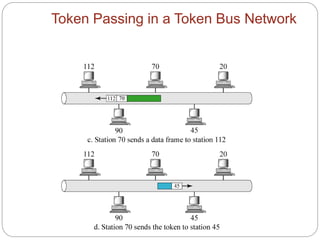
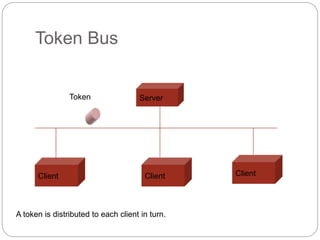
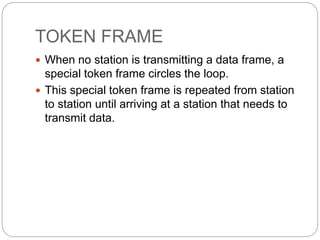
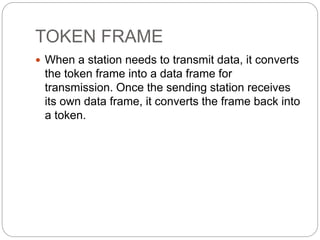
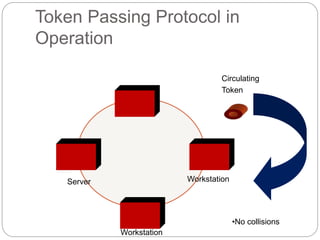
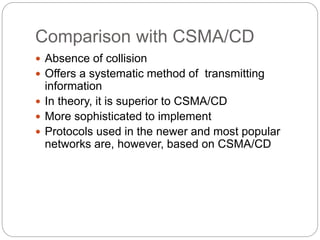
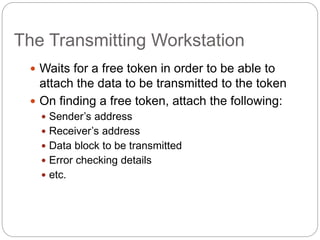
- How token passing works on token bus and token ring networks, with stations passing a token frame that allows the holder to transmit data
- Standards such as IEEE 802.4 for token bus and IEEE 802.5 for token ring
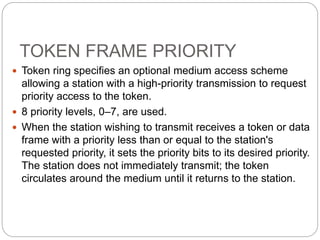
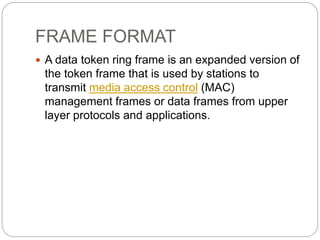
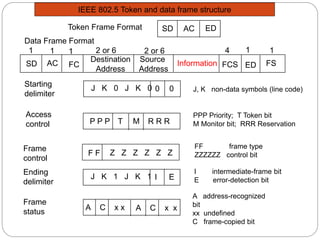
- Key aspects of token ring and token bus networks, including frame formats, priority schemes, and how data is transmitted and errors are handled.