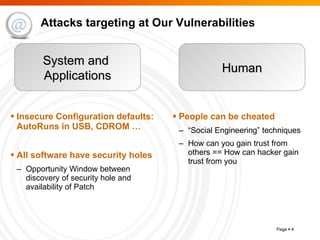
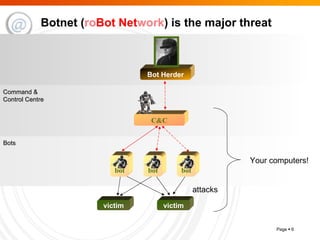
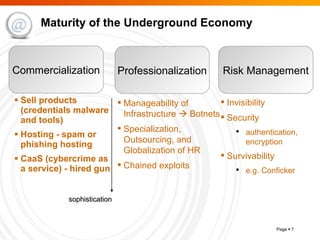
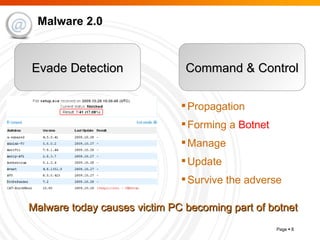
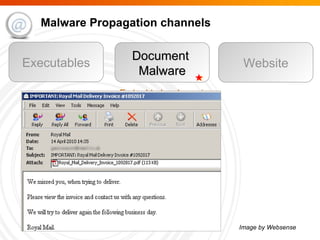
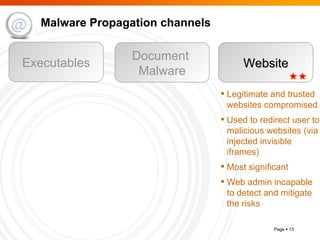
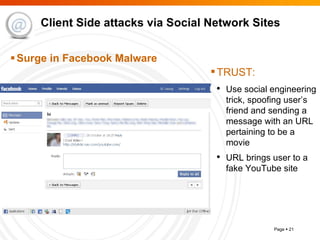
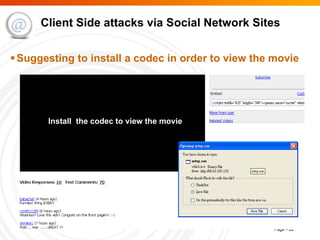
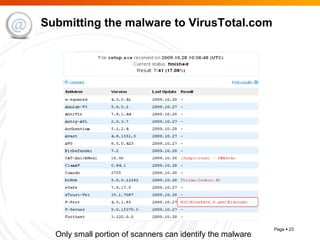
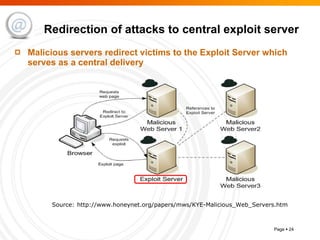
The document summarizes trends in internet attacks and security threats. It discusses how vulnerabilities are exploited through techniques like social engineering, insecure configurations, and software vulnerabilities. It also describes common malware propagation methods, targeted attacks on individuals and organizations, and recommendations for mitigation strategies including education, awareness, and proactive incident handling.