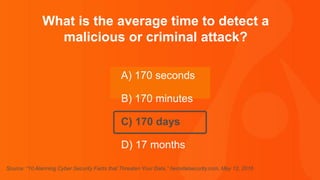
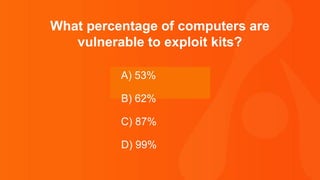
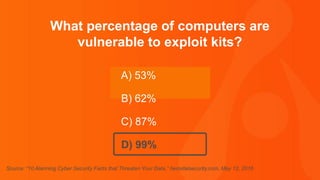
The document contains a series of questions and statements about cybersecurity threats and vulnerabilities. Some key facts presented include:
- 400,000 Facebook accounts are compromised by hackers every day
- The September 2016 Yahoo breach affected 500 million user accounts
- The fastest spreading email worm, MyDoom, caused $480 million in financial damage
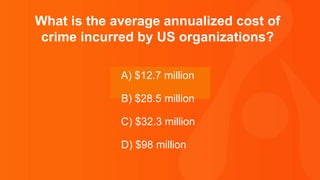
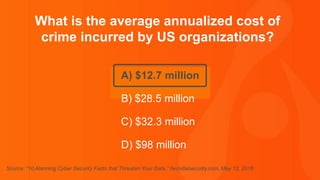
- The average annualized cost of crime incurred by US organizations is $28.5 million
- The Pentagon reports receiving 5-10 million cyber attack attempts per day