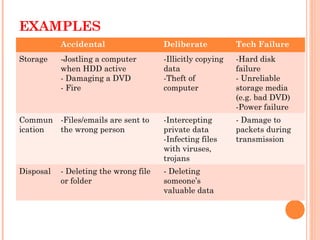
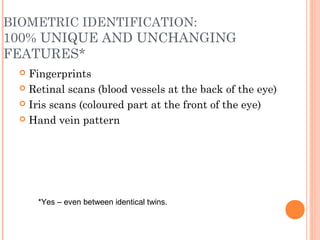
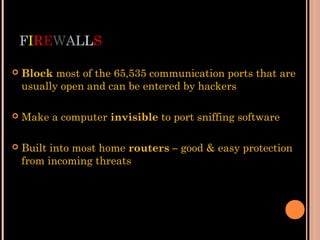
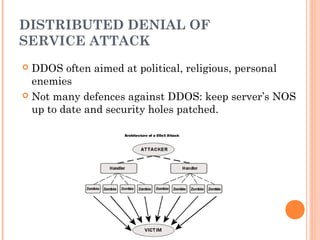
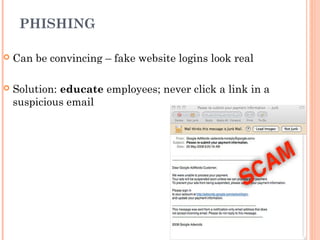
This document discusses various threats to data and information security during storage, communication and disposal. It identifies deliberate actions like viruses, theft and hacking; accidental actions such as incompetent employees and natural disasters; and technical failures involving hardware, software and storage media. It provides examples and recommendations for prevention, including physical security, procedures, encryption, firewalls, disaster recovery plans and backups.