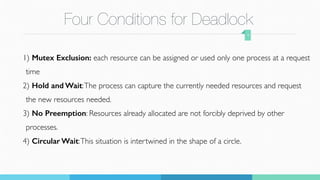
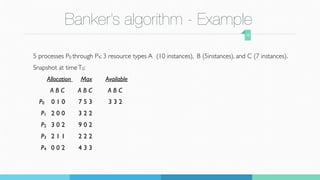
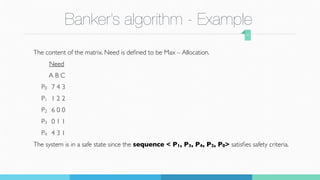
The document summarizes a student project presentation on implementing Banker's algorithm for deadlock avoidance. It includes:
1) An overview of Banker's algorithm and how it checks for safe states to avoid deadlock by dynamically evaluating resource requests.
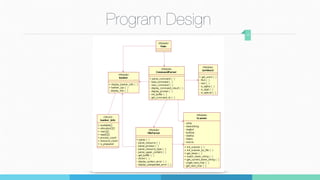
2) Details on the data structures and parsing approach used to represent the banker's algorithm information and process resource requests.
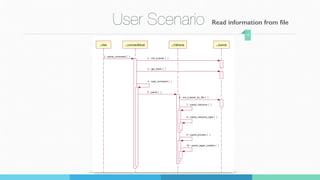
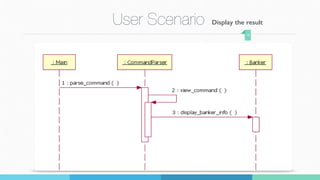
3) A demonstration of the program loading sample data from a file, displaying the banker's algorithm information, and handling different user commands and error scenarios.





![Banker’s algorithm - Notation
* N: the number of processes on the system
* M: the number of resources present in the system
- Available [1: m]: Indicate which resource i is
- Max [1: n, 1: m]: Expression of the maximum number of resources of type j of process i
- Allocation [1: n, 1: m]: Indicates whether process i has received a resource of type j
- Need [1: n, 1: m]: Max - Allocation. Express how many more can be allocated in the future
-Vectors X,Y
- Work array: an array containing the intermediate result of a resource
- Finish array: a boolean array indicating which process has terminated
8](https://image.slidesharecdn.com/sjsuosikwhanchang-170418152917/85/The-implementation-of-Banker-s-algorithm-data-structure-and-its-parser-8-320.jpg)
![Banker’s algorithm - Safety Check
Step 1. Assign the resources currently available for work. Finish Set all values of array to false (which means that no processes have
finished yet)
Step 2. Find a process i that does not finish its current run and can satisfy all of the resources it needs the most.
Step 3.Terminate the process and return the resource to finish.
Step 4.When all finish [] entry values are true, the algorithm is ended
How to perform a resource grant using Safety Check
Step 1. Record the newly requested request of each process in the request array
Step 2. If a request in a process requests more than Maximum, it will not accept the request
Step 3. If the condition is less than the maximum value, once you have performed the safety check algorithm
=>The banker's algorithm is implemented in safety and performs deadlock avoidance.
=>There are situations in which a process needs to manage a maximum request for each type, making expensive decisions to perform
and deadlock avoidance.
9](https://image.slidesharecdn.com/sjsuosikwhanchang-170418152917/85/The-implementation-of-Banker-s-algorithm-data-structure-and-its-parser-9-320.jpg)

![Approach
1) Defined a banker’s information structure
#define A 65
#define MAX_RESOURCE 100
#define MAX_PROCESS 100
#define MAX_RESOURCE_NAME_LEN 40
typedef struct _banker_info
{
char resource_name[MAX_RESOURCE]
[MAX_RESOURCE_NAME_LEN + 1];
int available[MAX_RESOURCE];
int instance_count[MAX_RESOURCE];
int allocation[MAX_PROCESS][MAX_RESOURCE];
int max[MAX_PROCESS][MAX_RESOURCE];
int need[MAX_PROCESS][MAX_RESOURCE];
int process_count;
int resource_count;
int sequence[MAX_PROCESS];
int sequence_count;
int is_prepared;
} banker_info;
13
2) Implemented a scanner module to separate
tokens from files.
Token Types
• ENDFILE: the end of file,
• ERROR: scan error
• ID:Alphabet exists more than one
• NUM: Decimal exists more than one
• COLON:“:”](https://image.slidesharecdn.com/sjsuosikwhanchang-170418152917/85/The-implementation-of-Banker-s-algorithm-data-structure-and-its-parser-13-320.jpg)
![Approach
3) Program command
• load [file_name]: Read Banker’s
information from file
• view: Display the information of Banker
• quit: Exit the program
14
4) Error type for reading the input
• When the allocation value of the process is
larger than the available value of the resource
• When the allocation value of the process is
larger than its max value
• When negative value is input to all values
• When unexpected input is found in the file
format](https://image.slidesharecdn.com/sjsuosikwhanchang-170418152917/85/The-implementation-of-Banker-s-algorithm-data-structure-and-its-parser-14-320.jpg)