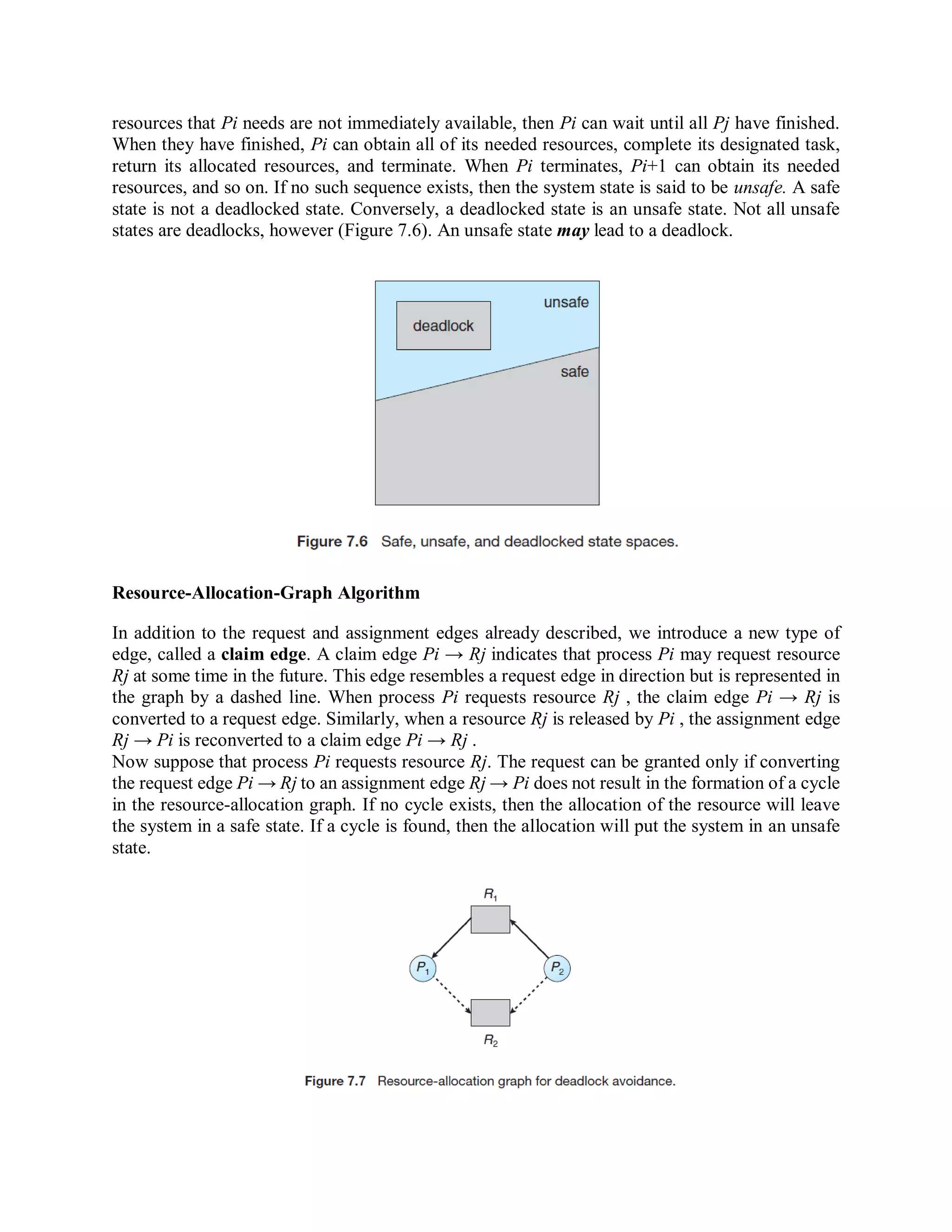
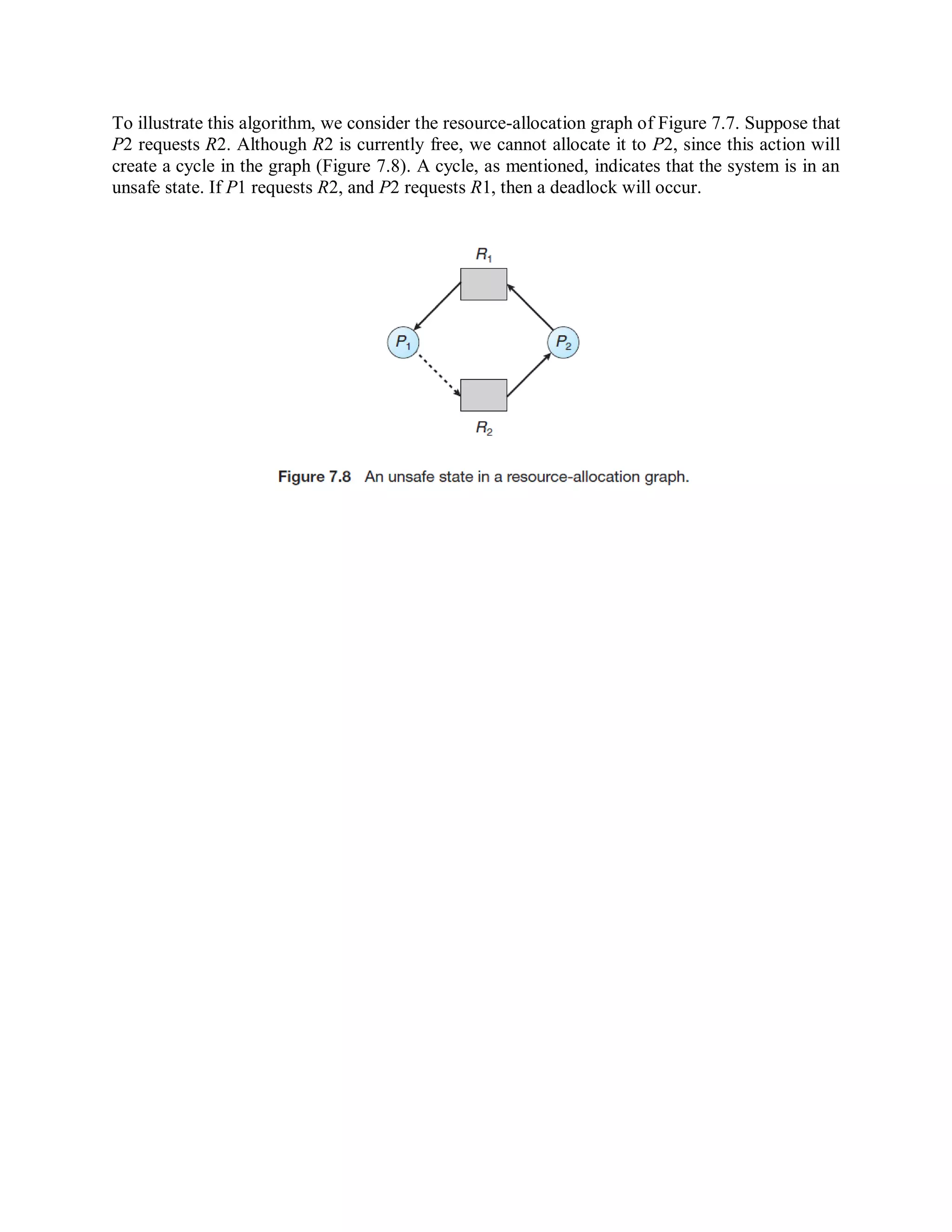
There are three main approaches to handling deadlocks: prevention, avoidance, and detection with recovery. Prevention methods constrain how processes request resources to ensure at least one necessary condition for deadlock cannot occur. Avoidance requires advance knowledge of processes' resource needs to decide if requests can be immediately satisfied. Detection identifies when a deadlocked state occurs and recovers by undoing the allocation that caused it.