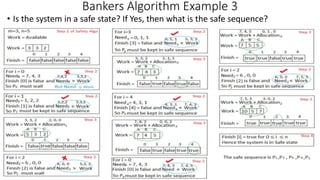
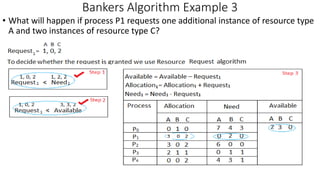
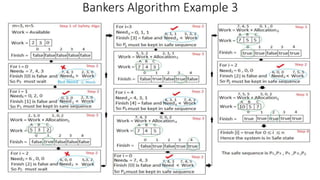
Here is the solution to the Bankers Algorithm example 3:
A) The content of the Need matrix will be:
Process | A | B | C
P0 | 3 | 1 | 3
P1 | 2 | 4 | 2
P2 | 7 | 4 | 5
P3 | 8 | 4 | 6
P4 | 8 | 5 | 5
B) The system is not in a safe state. The available resources (3, 3, 2) are not sufficient to fulfill the need of process P2 (7, 4, 5).
C) If process P1 requests one more instance of resource A and two instances of resource C, the request can be granted as





![Banker’s Algorithm
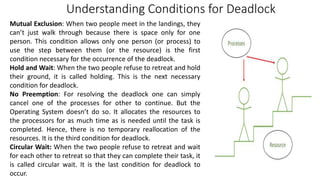
• The banker’s algorithm is a resource allocation and deadlock avoidance algorithm
that tests for safety by simulating the allocation for predetermined maximum
possible amounts of all resources, then makes an “s-state” check to test for possible
activities, before deciding whether allocation should be allowed to continue.
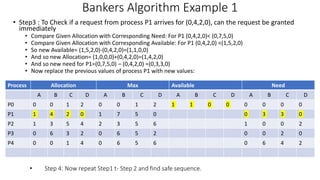
• Let n = number of processes, and m = number of resources types.
• Available: Vector of length m. If available [j] = k, there are k instances of resource
type Rj available
• Max: n x m matrix. If Max [i,j] = k, then process Pi may request at most k
instances of resource type Rj
• Allocation: n x m matrix. If Allocation[i,j] = k then Pi is currently allocated k
instances of Rj
• Need: n x m matrix. If Need[i,j] = k, then Pi may need k more instances of Rj to
complete its task
Need [i,j] = Max[i,j] – Allocation [i,j]](https://image.slidesharecdn.com/os-unit3deadlockbankersalgorithm-230719223941-465ea54b/85/OS-Unit-3-Deadlock-Bankers-Algorithm-pptx-9-320.jpg)
![Banker’s Algorithm
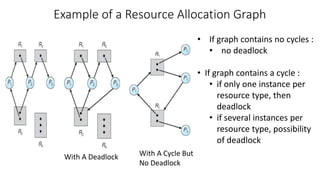
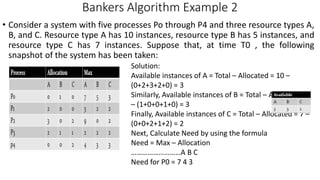
• Banker’s algorithm consists of
1. Safety algorithm and
2. Resource request algorithm
• Safety Algorithm: The algorithm for finding out
whether or not a system is in a safe state
can be described as follows:
1) Let Work and Finish be vectors of length
‘m’ and ‘n’ respectively.
Initialize: Work = Available
Finish[i] = false; for i=1, 2, 3, 4….n
2) Find an i such that both
a) Finish[i] = false
b) Needi <= Work
if no such i exists goto step (4)
3) Work = Work + Allocation[i]
Finish[i] = true
goto step (2)
4) if Finish [i] = true for all i
then the system is in a safe state
• Resource-Request Algorithm : Let Requesti be the request
array for process Pi. Requesti [j] = k means process Pi
wants k instances of resource type Rj. When a request for
resources is made by process Pi, the following actions are
taken:
1) If Requesti <= Needi
Goto step (2) ; otherwise, raise an error condition,
since the process has exceeded its maximum claim.
2) If Requesti <= Available
Goto step (3); otherwise, Pi must wait, since the
resources are not available.
3) Have the system pretend to have allocated the requested
resources to process Pi by modifying the state as
follows:
• Available = Available – Requesti
• Allocationi = Allocationi + Requesti
• Needi = Needi– Requesti](https://image.slidesharecdn.com/os-unit3deadlockbankersalgorithm-230719223941-465ea54b/85/OS-Unit-3-Deadlock-Bankers-Algorithm-pptx-10-320.jpg)
![Bankers Algorithm Example 3
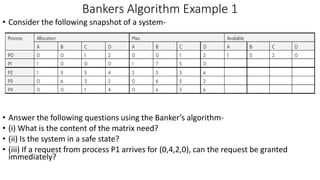
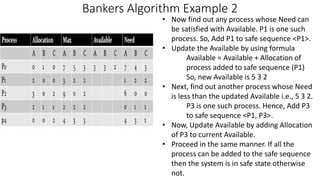
• Considering a system with five processes P0 through P4 and three resources of
type A, B, C. Resource type A has 10 instances, B has 5 instances and type C has
7 instances. Suppose at time t0 following snapshot of the system has been
taken:
A) What will be the content of the Need matrix?
Need [i, j] = Max [i, j] – Allocation [i, j]](https://image.slidesharecdn.com/os-unit3deadlockbankersalgorithm-230719223941-465ea54b/85/OS-Unit-3-Deadlock-Bankers-Algorithm-pptx-16-320.jpg)