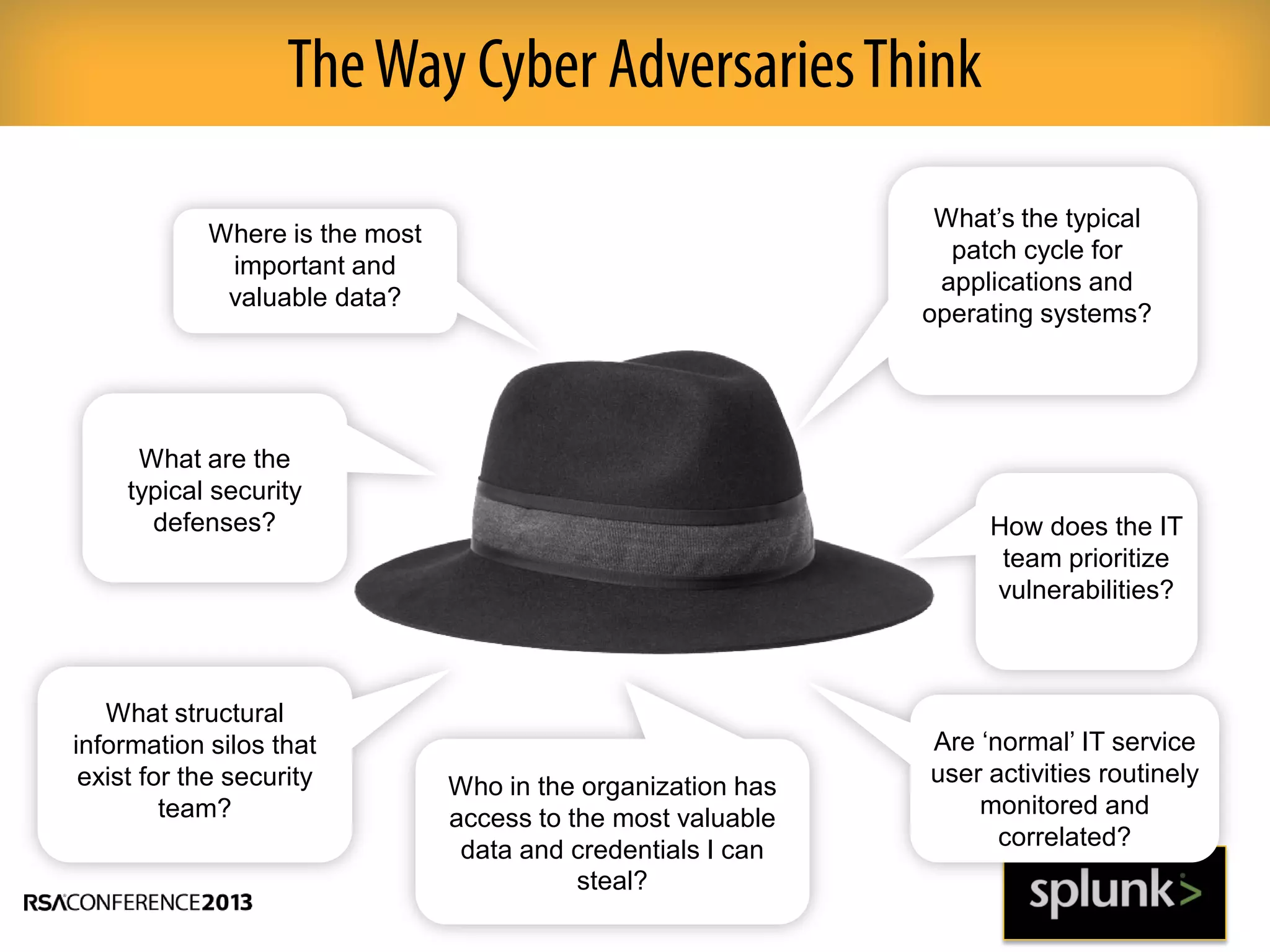
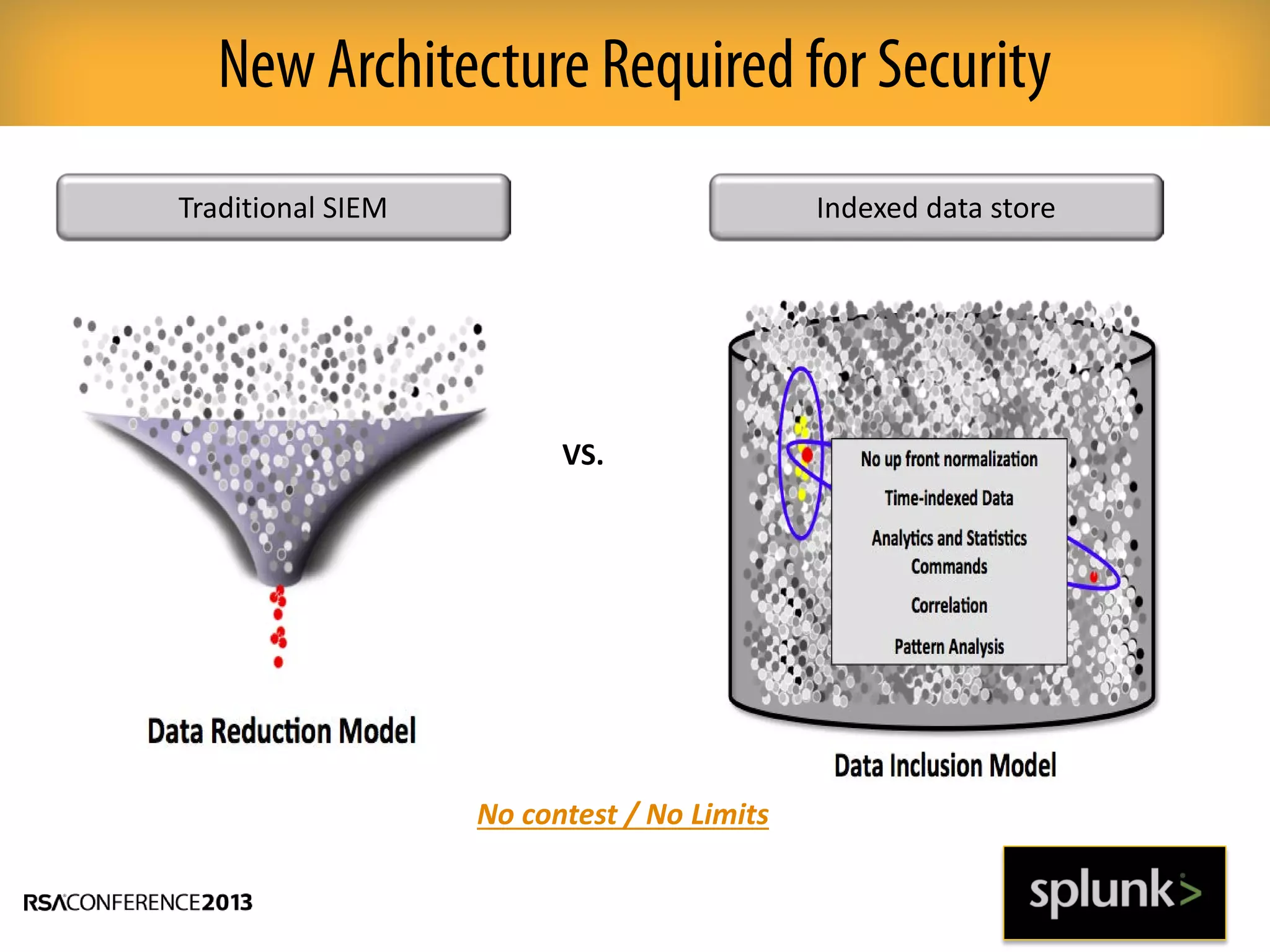
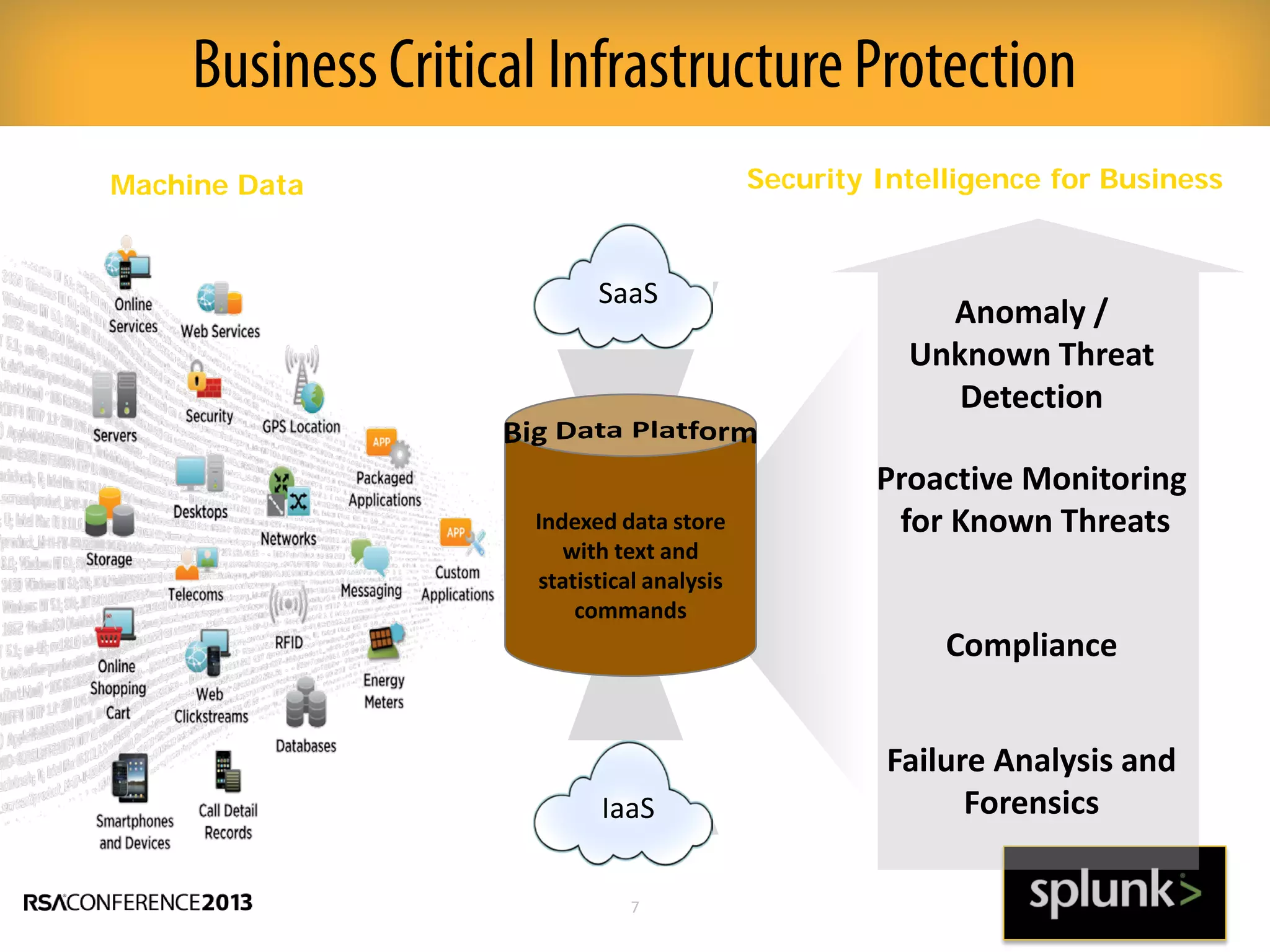
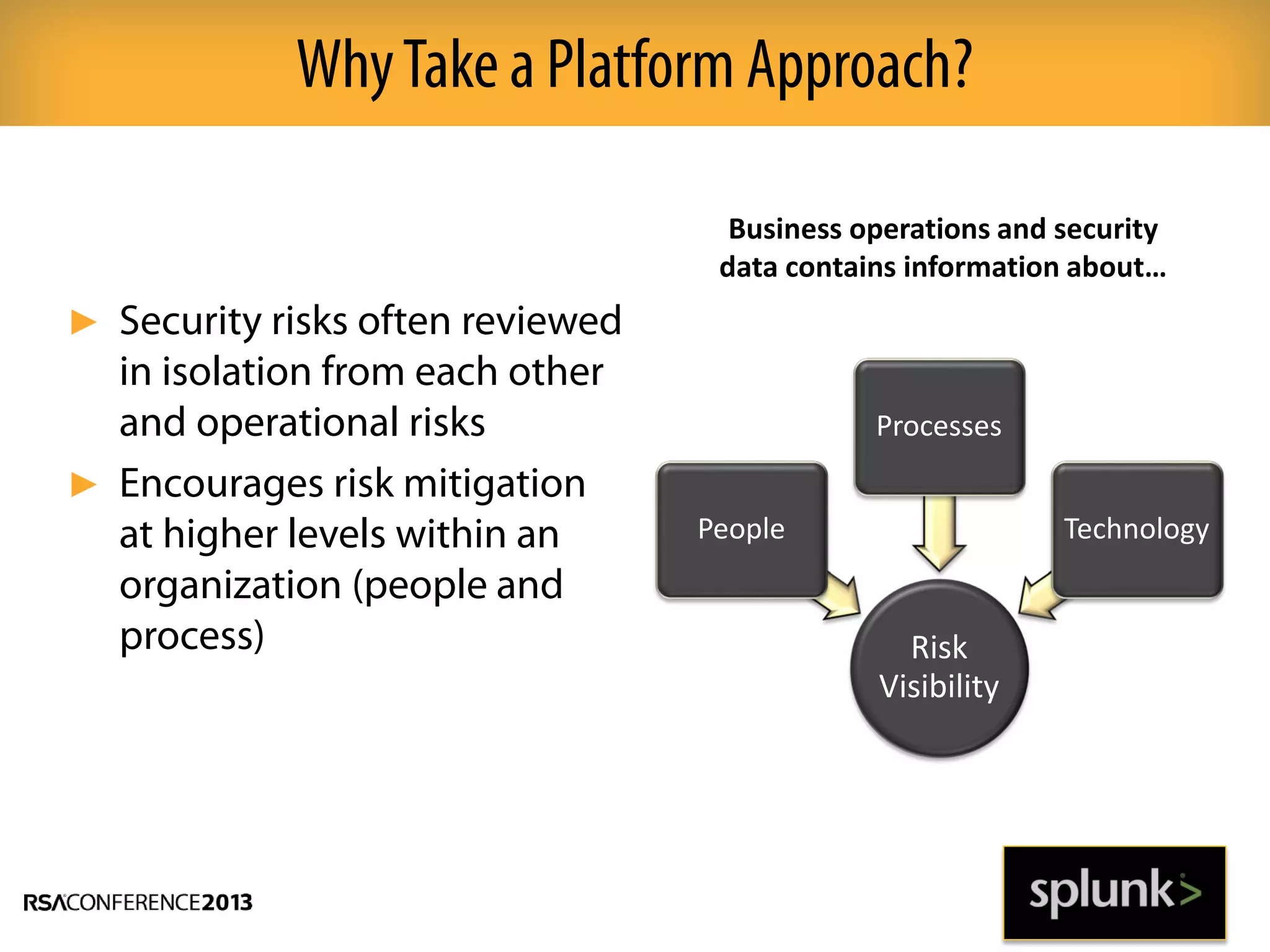
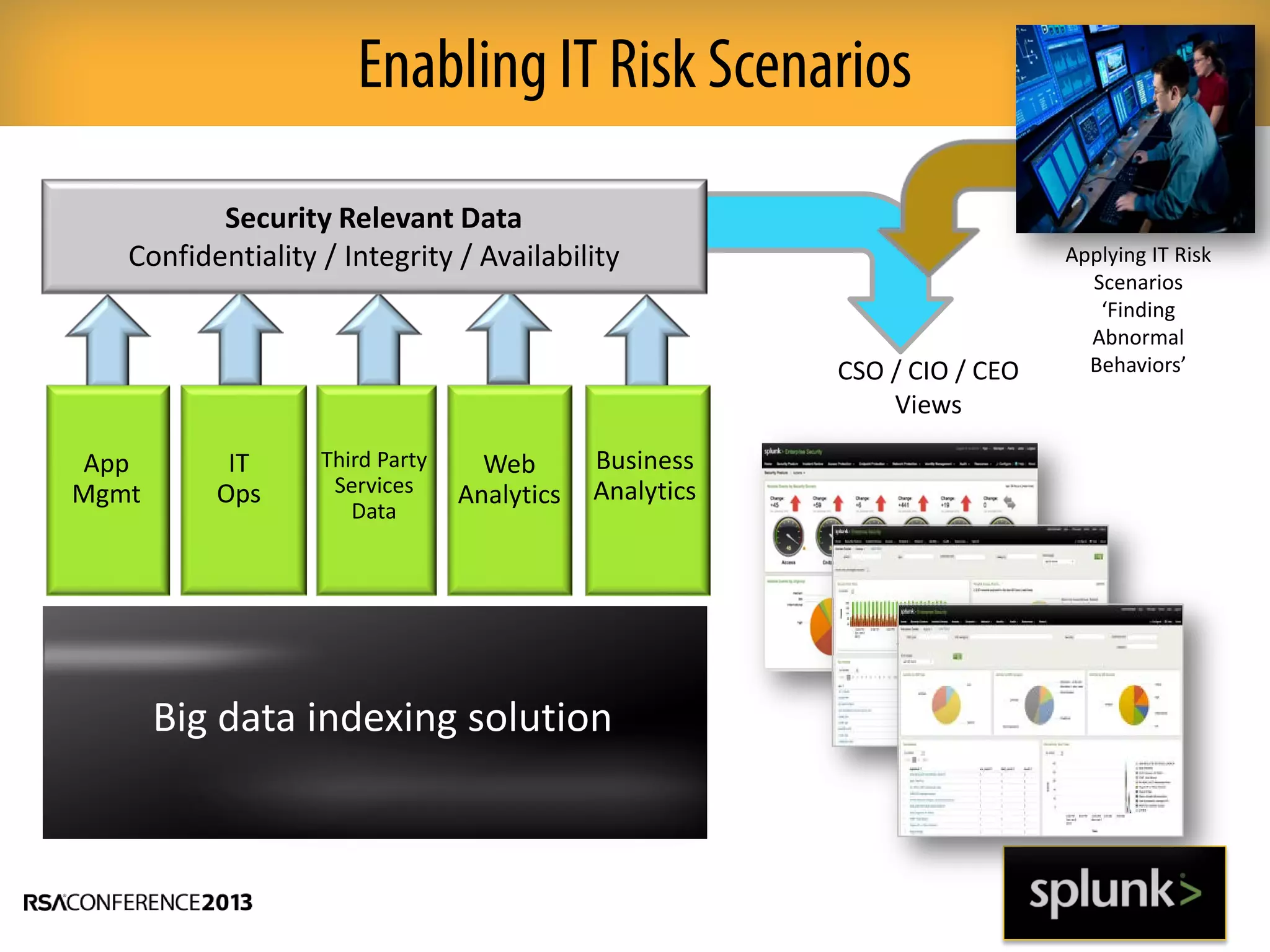
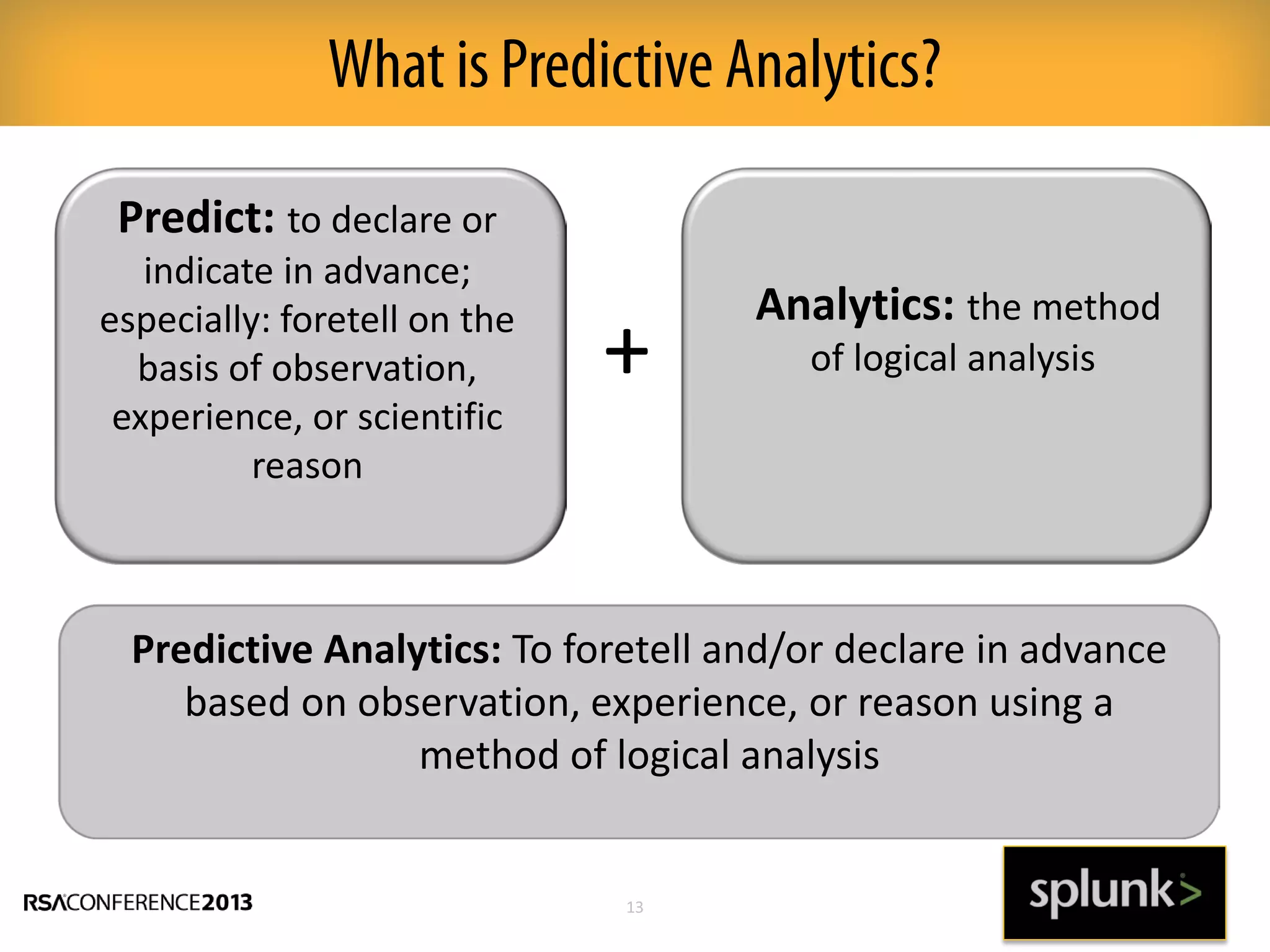
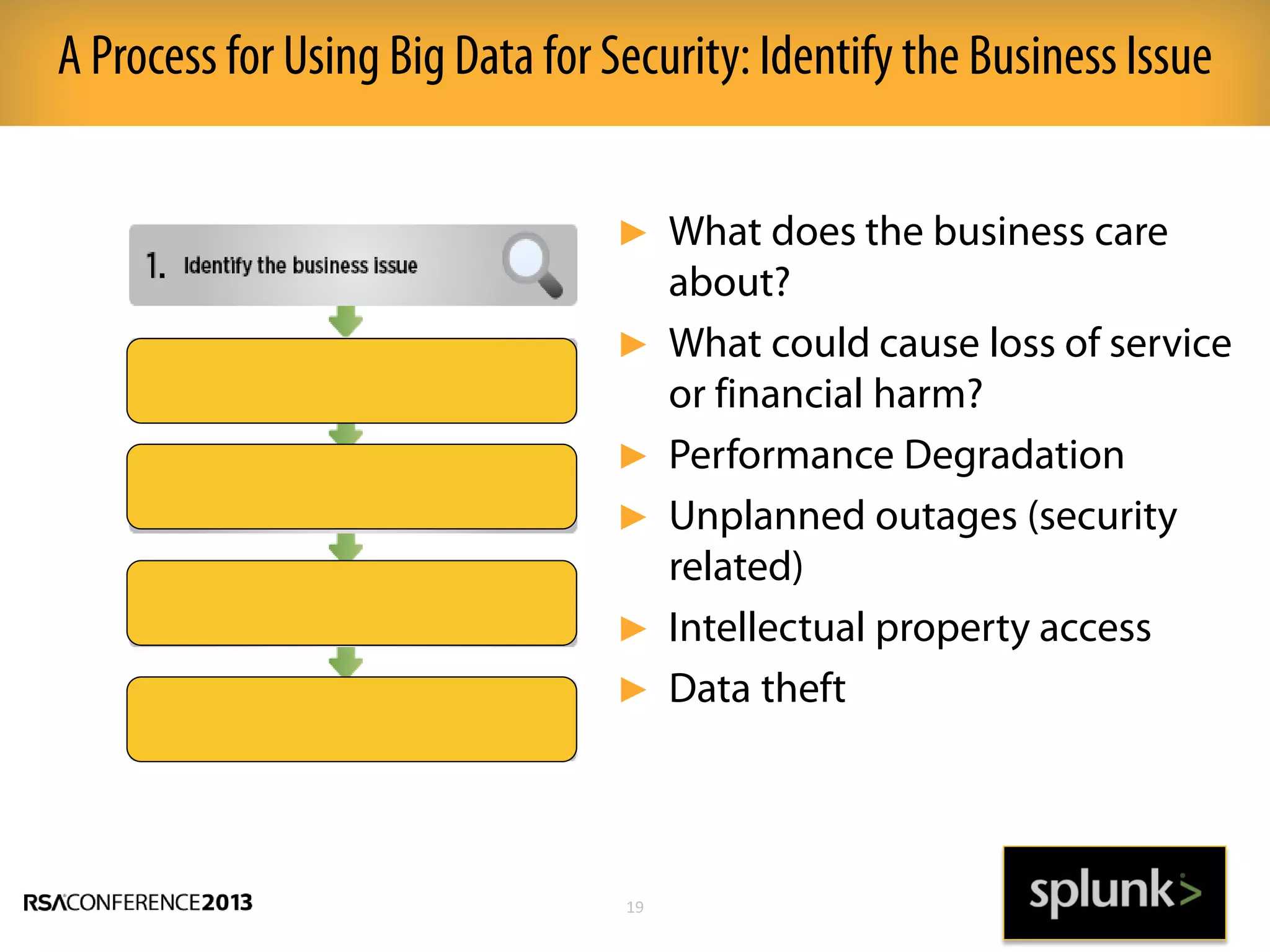
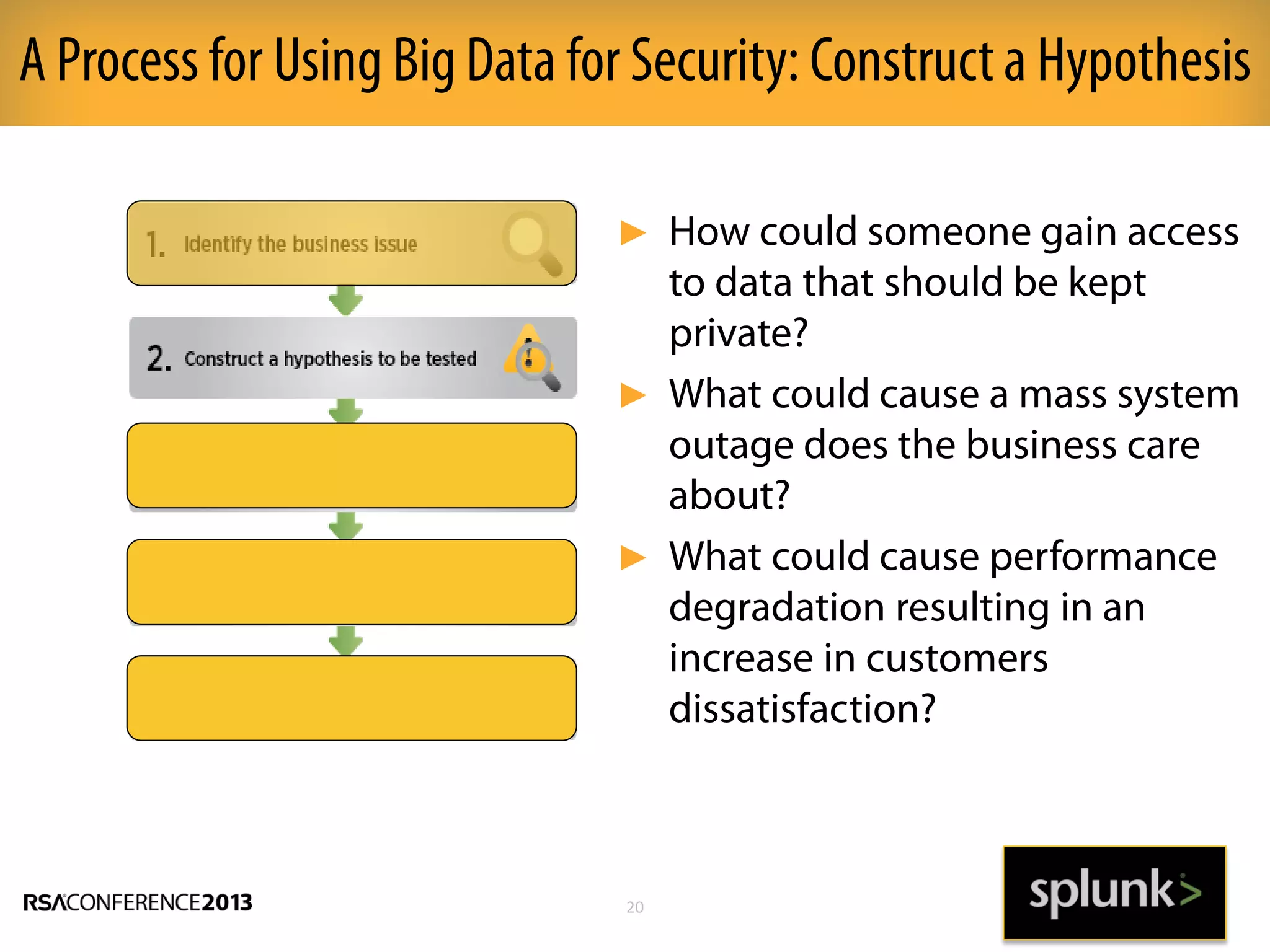
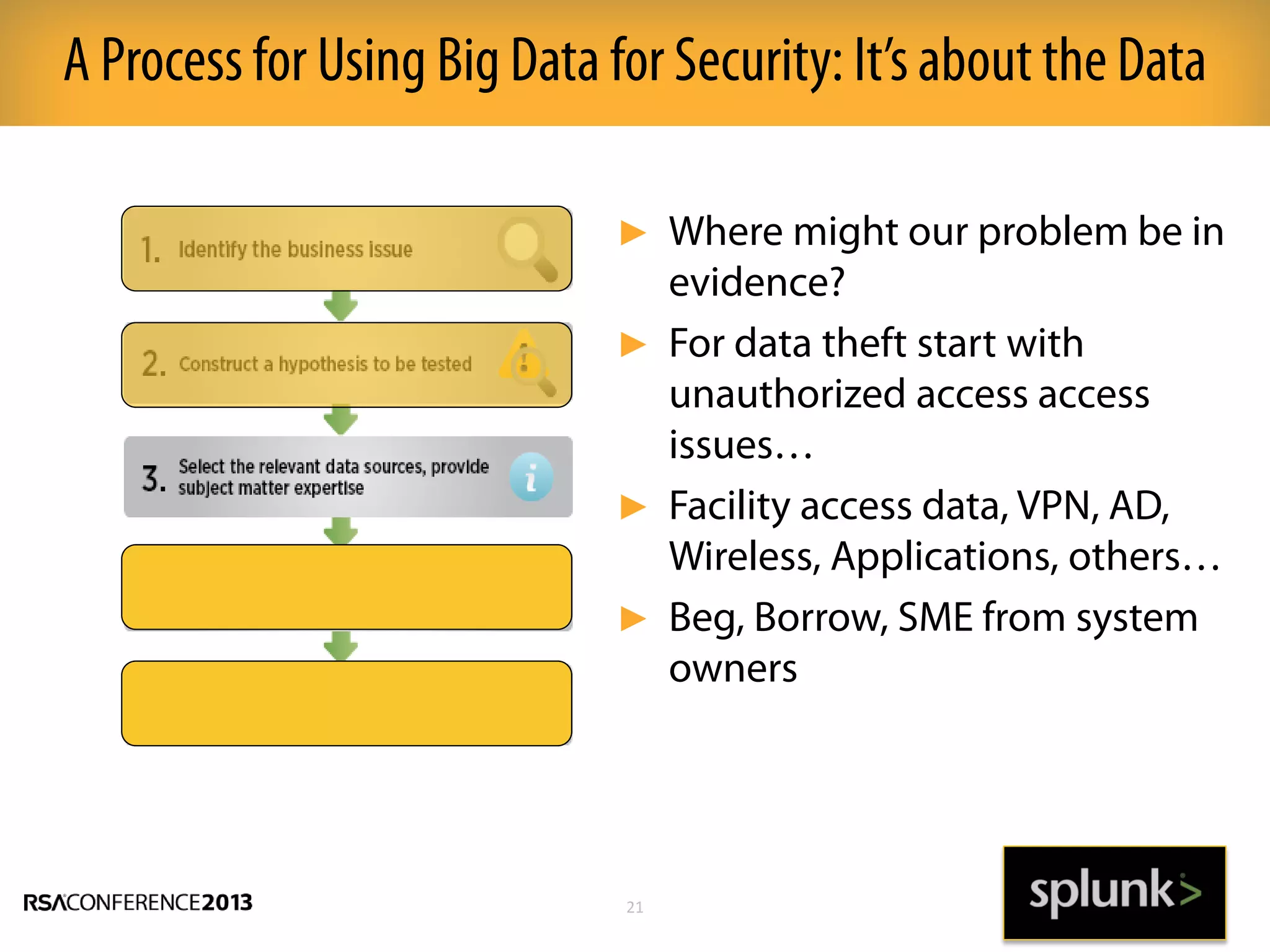
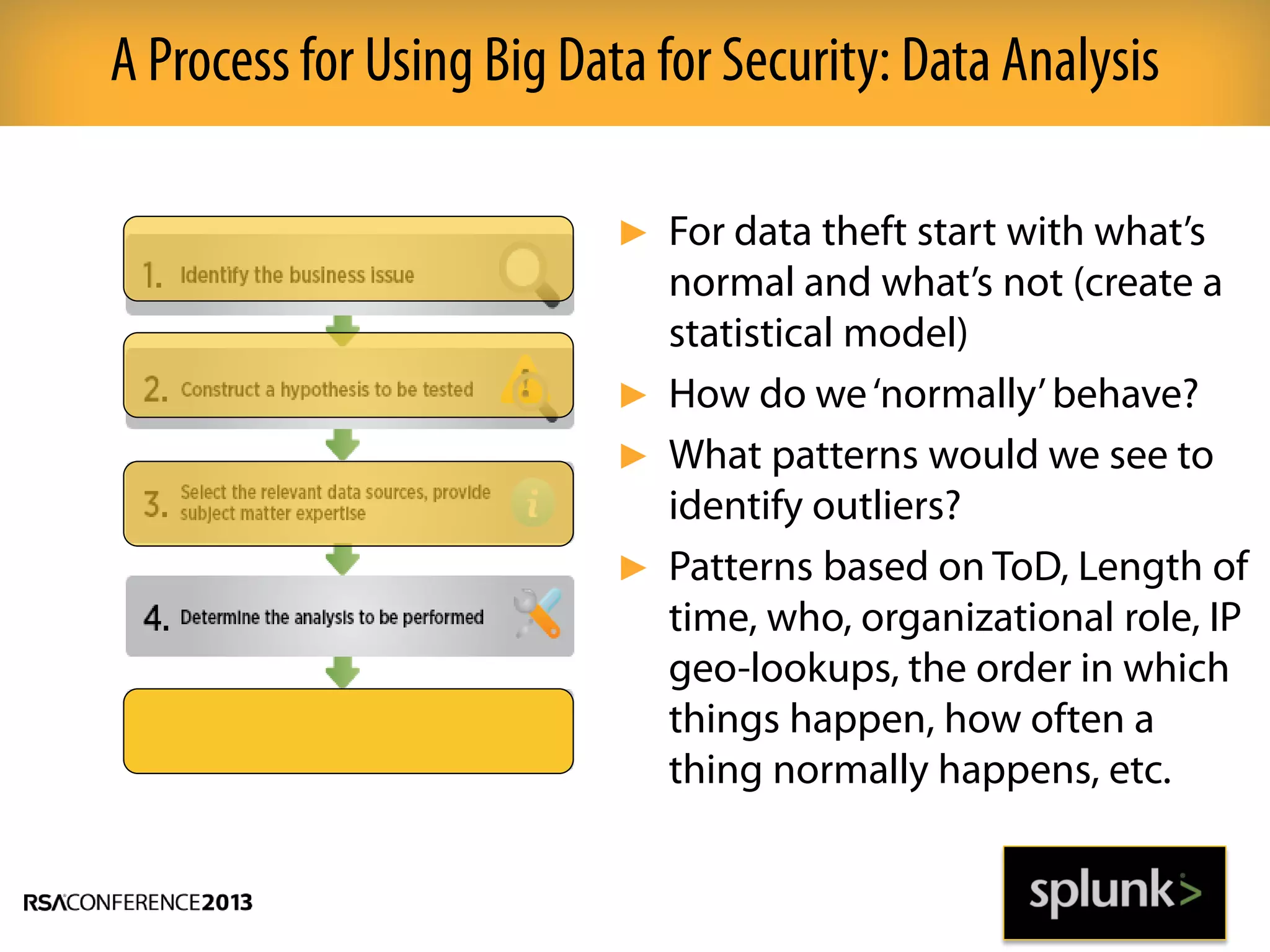
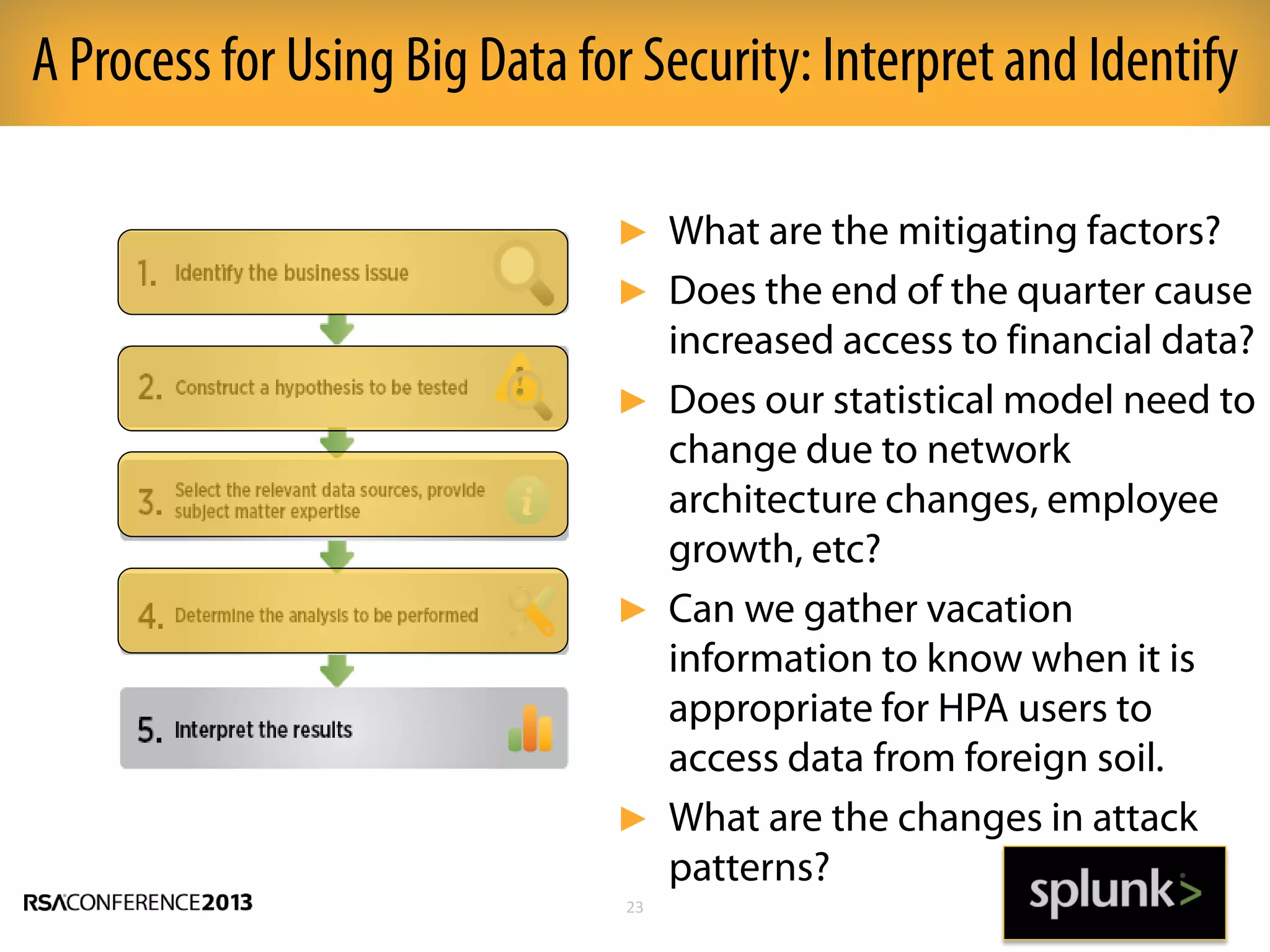
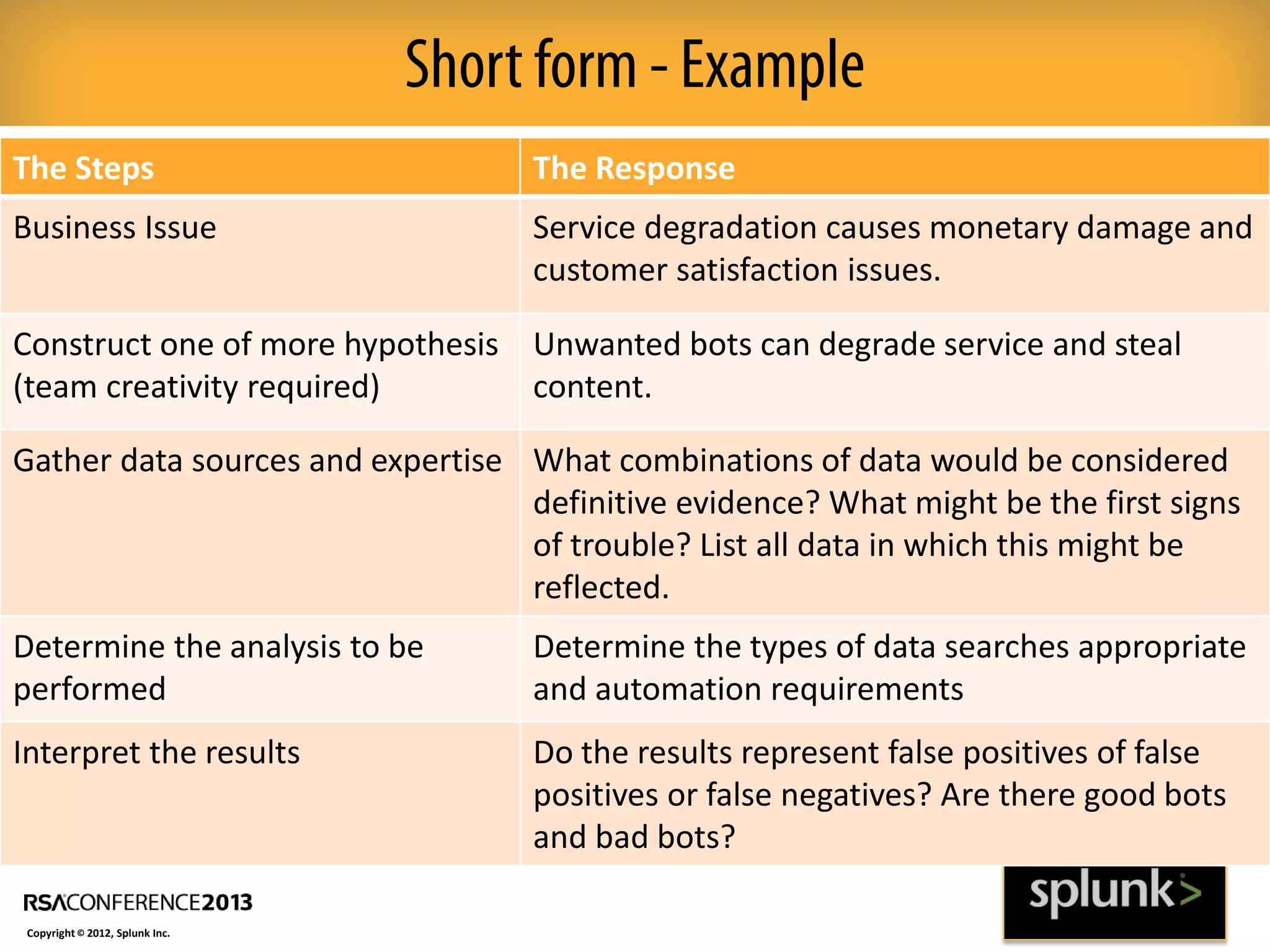
This document discusses how big data and security analytics can help organizations better protect themselves from cyber threats. It outlines how traditional security information and event management (SIEM) tools are no longer sufficient to handle the volume, velocity, and variety of security-related data. The document recommends taking a platform approach that combines both traditional IT security data and less traditional sources like industrial control systems, mobile devices, cloud services to gain better visibility into risks. It also emphasizes using statistical analysis and predictive modeling of this broader set of data sources to more accurately detect anomalies and advanced threats.