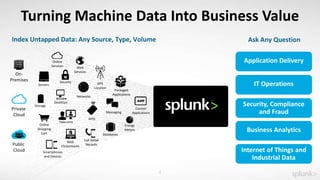
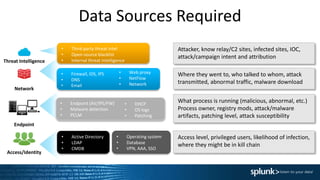
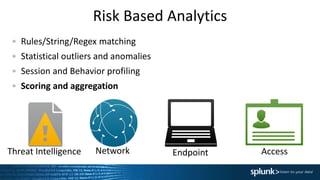
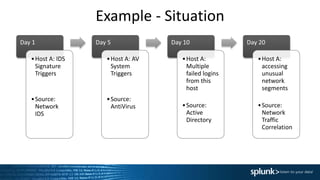
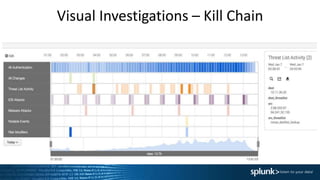
This document summarizes an presentation about operationalizing security intelligence. It discusses three key aspects:
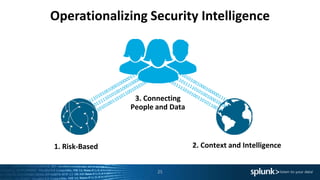
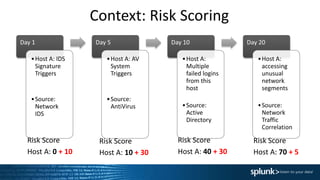
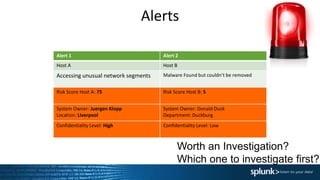
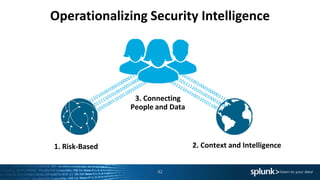
1. Using risk-based analytics to prioritize alerts based on correlating events over time and assigning risk scores to hosts. This helps determine which alerts require immediate investigation.
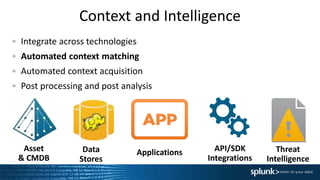
2. Adding context to alerts by integrating data from different technologies, matching context, and acquiring additional context through APIs. This provides more insight into prioritizing alerts.
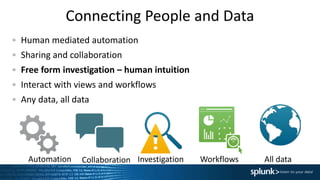
3. Connecting security data with people by enabling human-mediated automation, collaboration, free-form investigation through interactive views and workflows. This allows leveraging all security data and human intuition in investigations.
The presentation promotes operationalizing security intelligence through these approaches and evaluating Spl