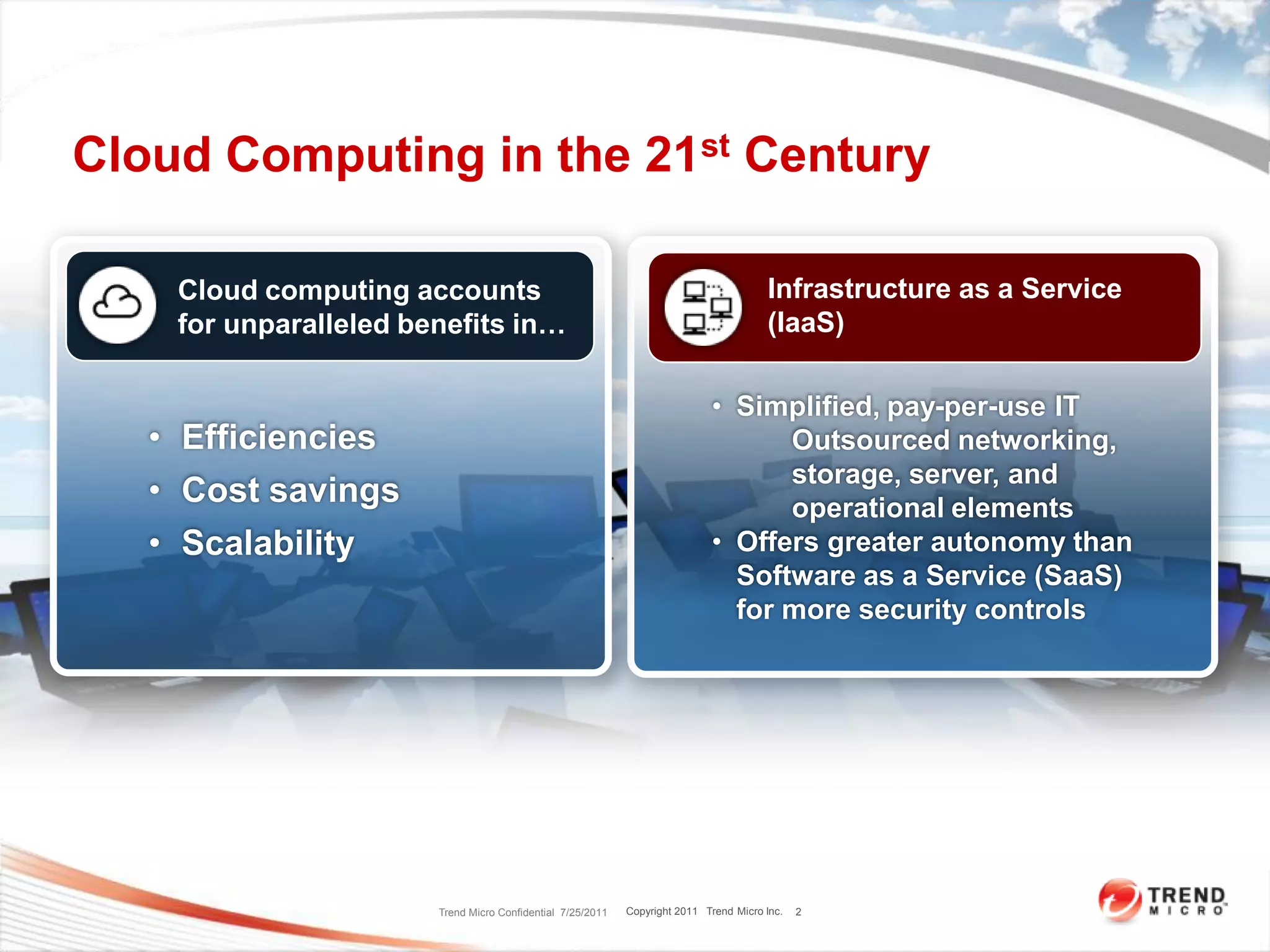
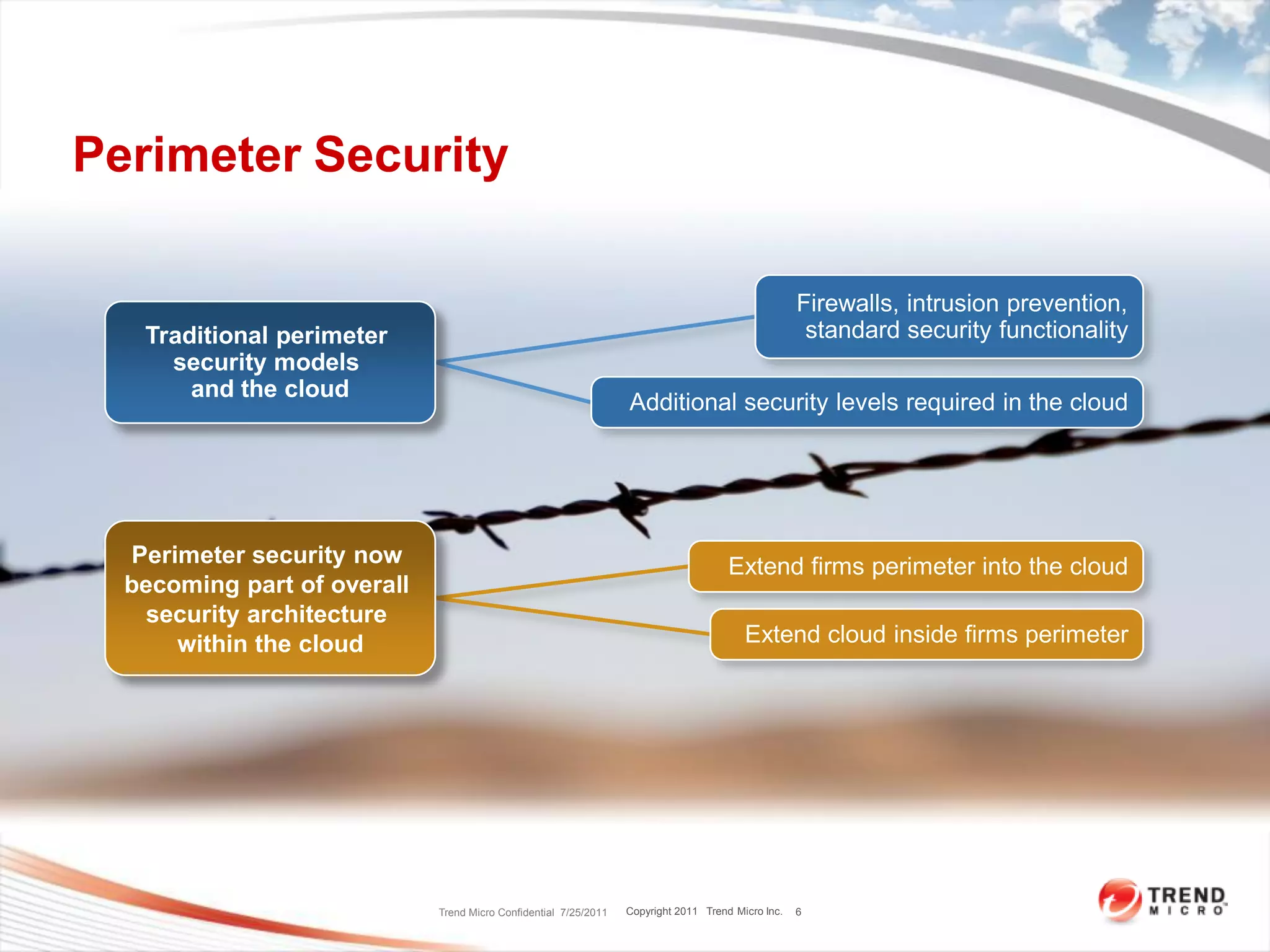
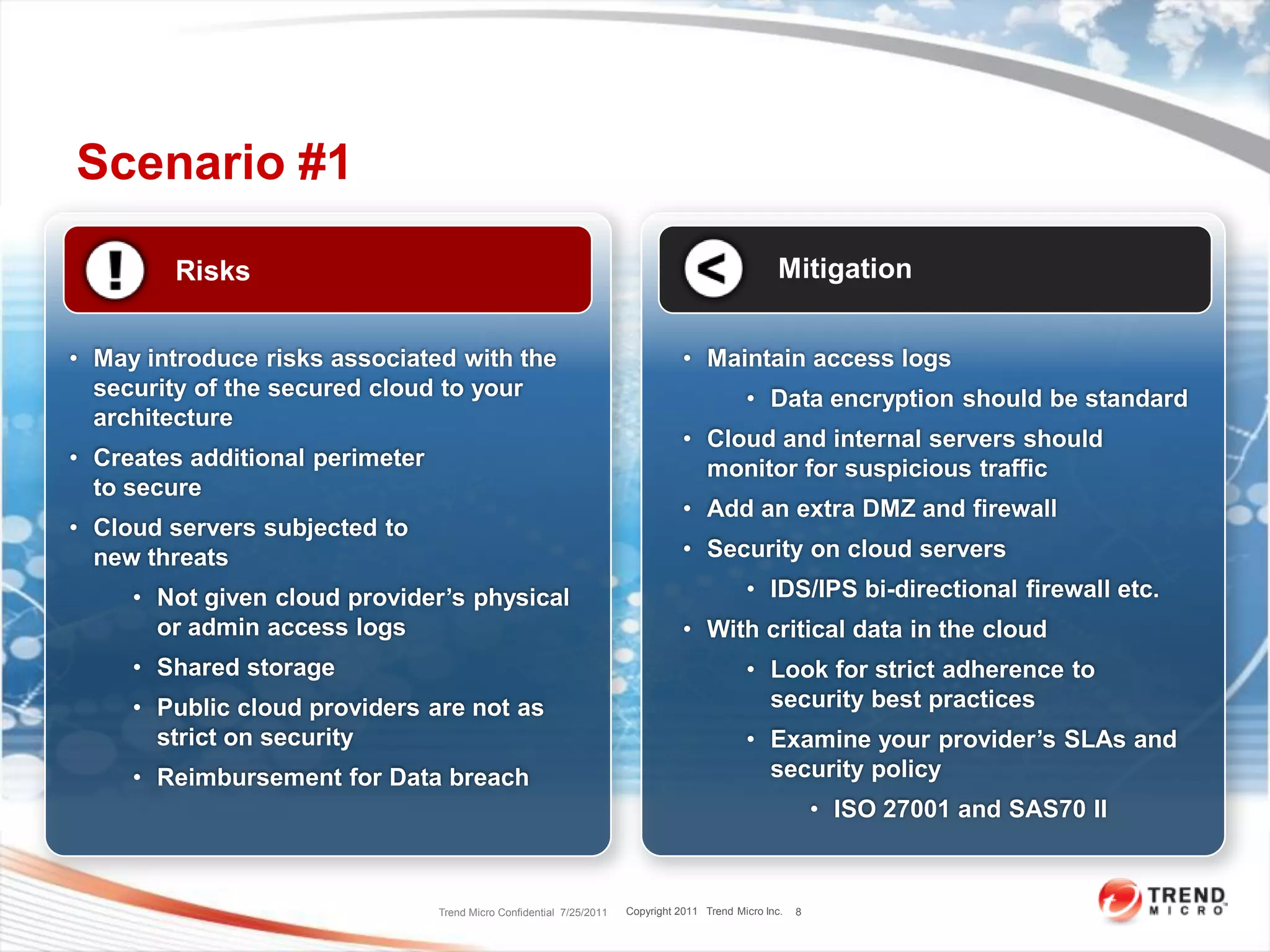
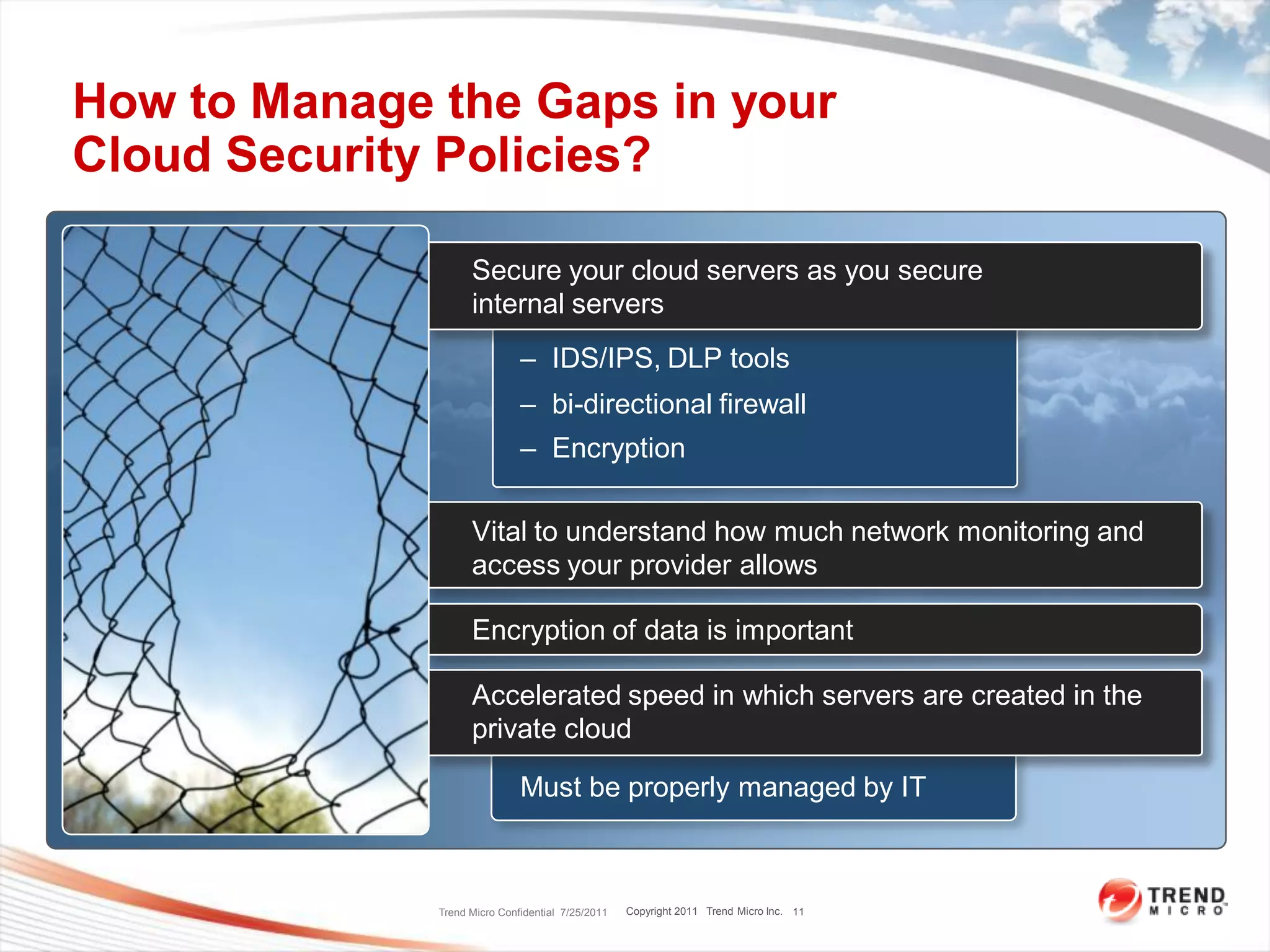
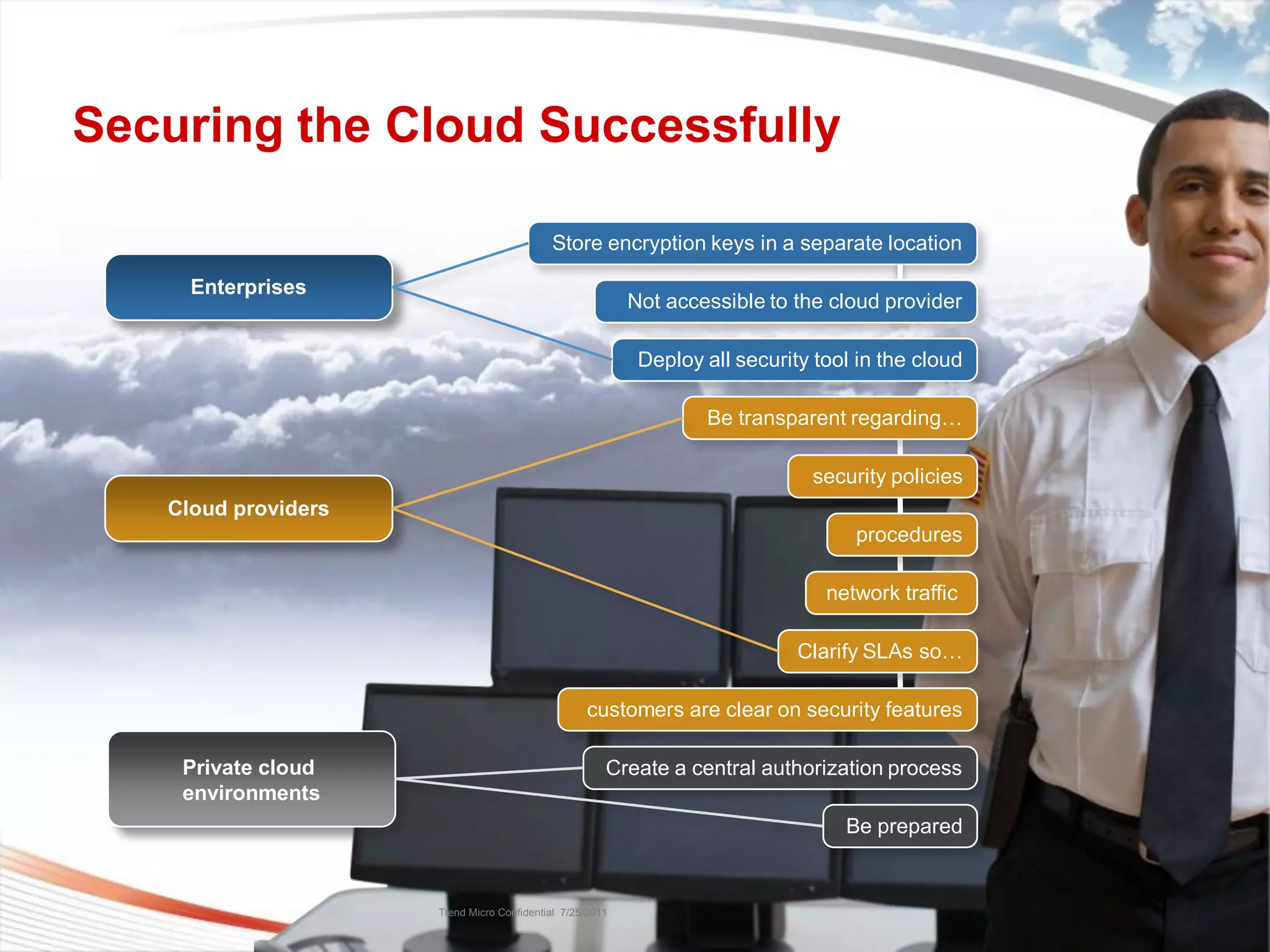
The document discusses security challenges in cloud computing and two scenarios for securing data in the cloud. Extending a company's perimeter into the public cloud involves creating VPN tunnels and applying security tools to cloud servers. Extending the cloud into a company's perimeter involves a cloud provider installing a node on-site. Both scenarios require log monitoring, encryption, firewalls and understanding the provider's security capabilities. The key is properly securing cloud servers as if they were internal servers and clarifying security responsibilities between customers and providers.