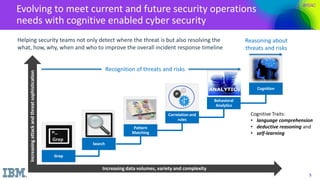
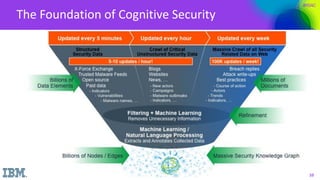
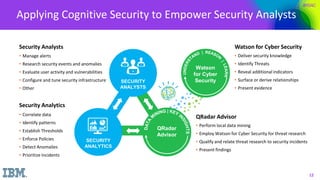
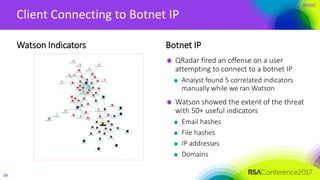
The document discusses the application of cognitive security in addressing challenges faced by cybersecurity analysts, such as high volumes of alerts, threat identification, and resource limitations. It introduces IBM's cognitive security platform, which enhances threat detection and response by leveraging advanced analytics and external data sources. A case study on SCANA Corporation illustrates the practical benefits of using cognitive security tools like Watson, which significantly reduces investigation time and improves incident analysis.