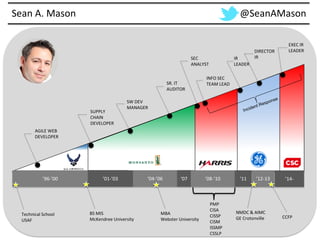
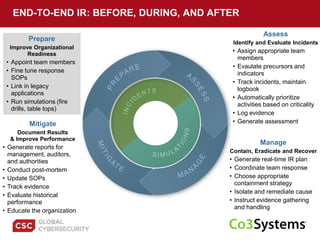
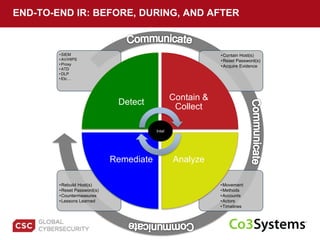
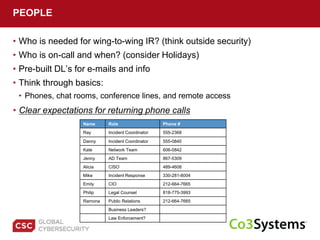
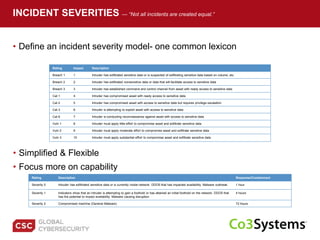
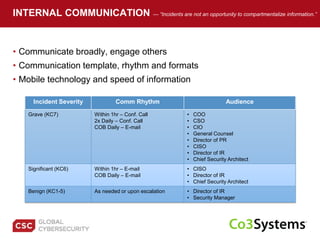
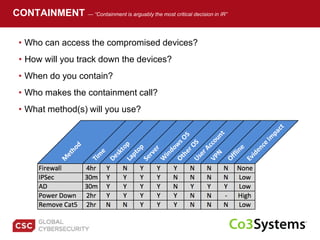
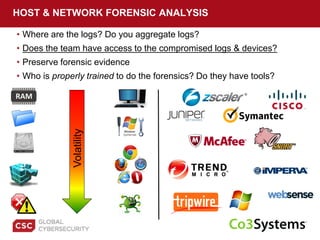
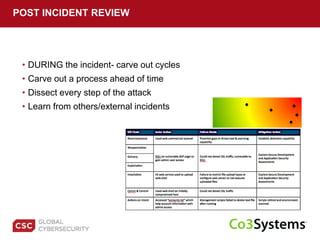
The document provides a comprehensive guide on preparing for incident response, detailing the steps for improving organizational readiness, managing incidents, and post-incident evaluations. It emphasizes the importance of team roles, communication, containment strategies, and the use of incident severity models for effective response. Additionally, it highlights the need for ongoing training, documentation updates, and establishing solid relationships with external parties for support during incidents.