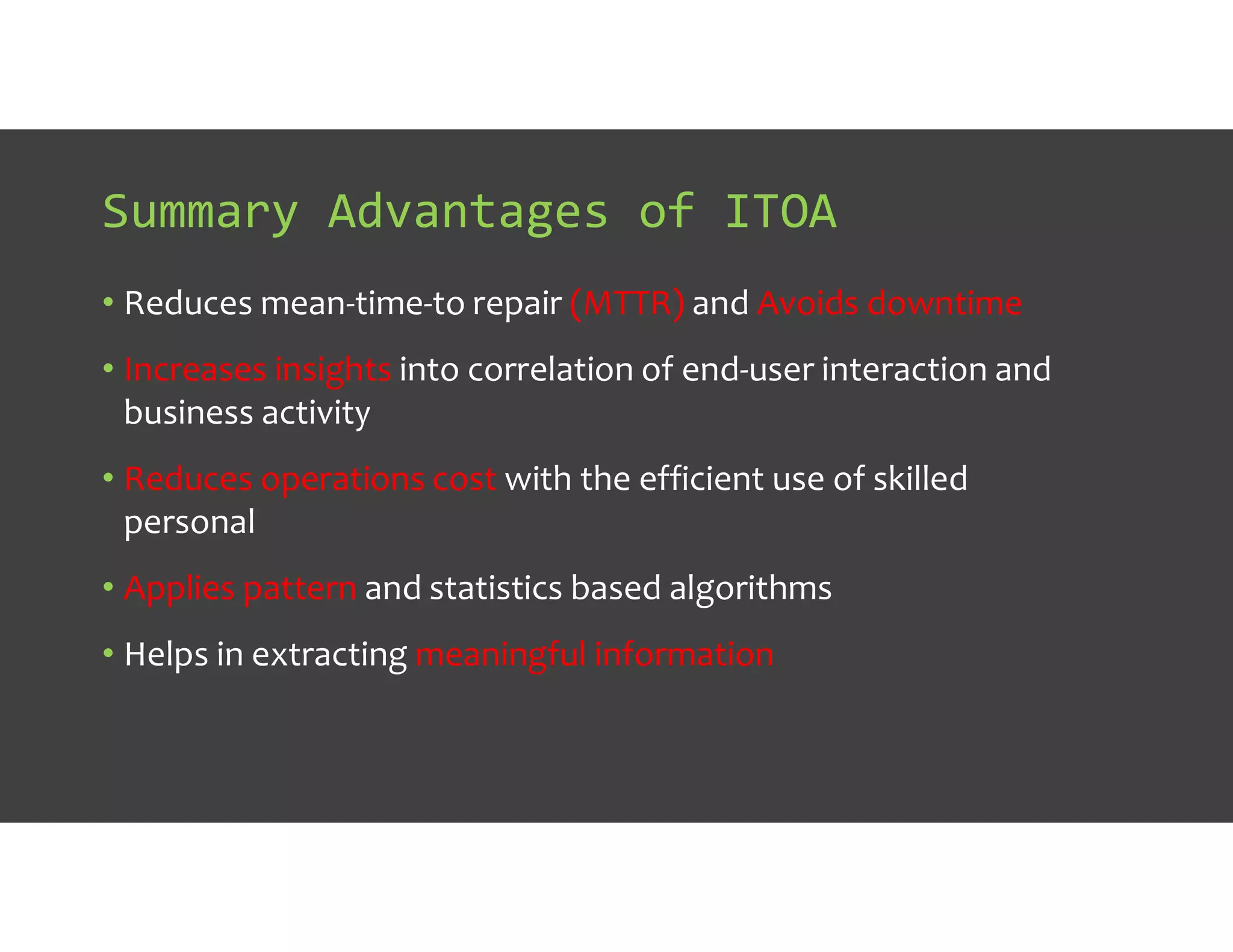
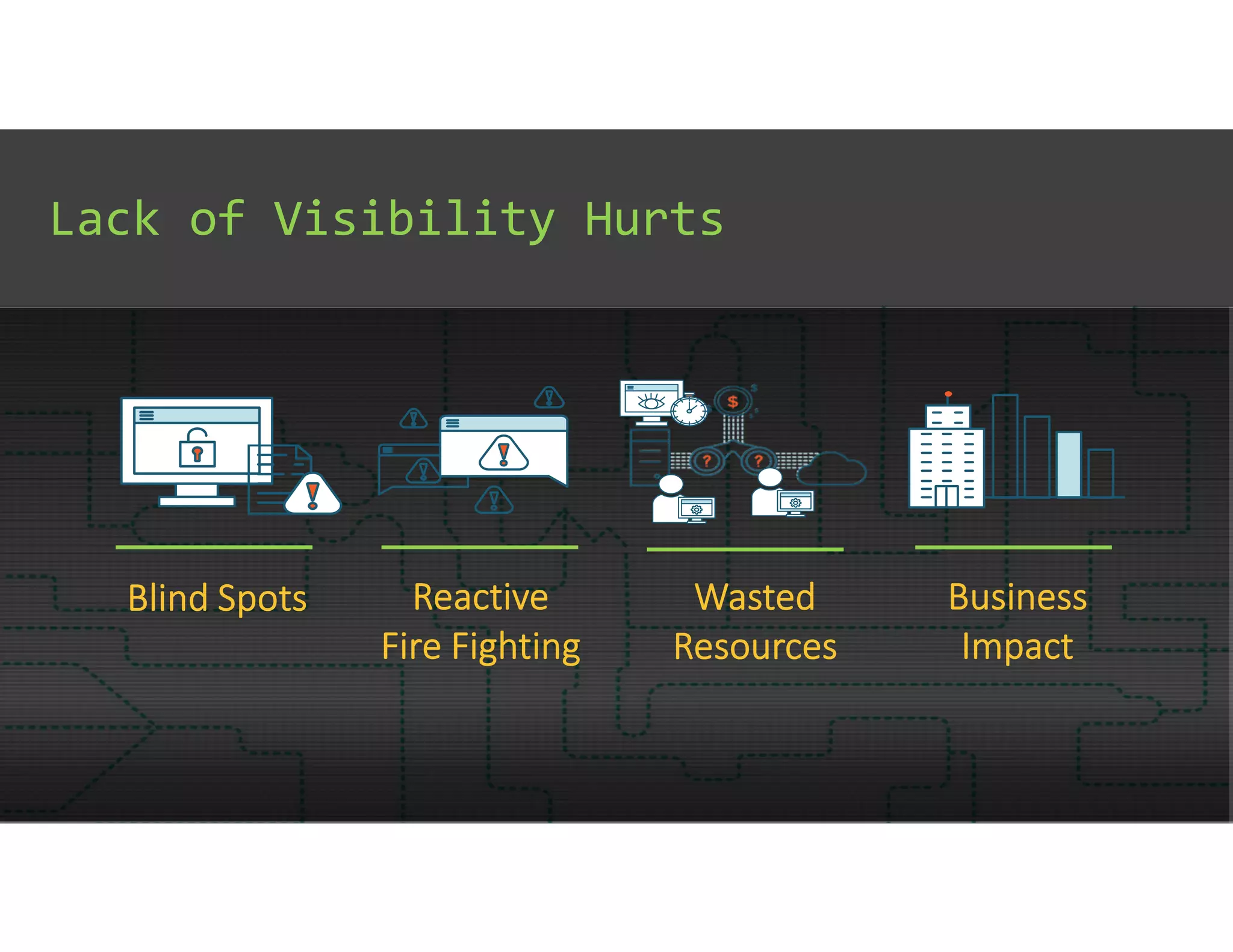
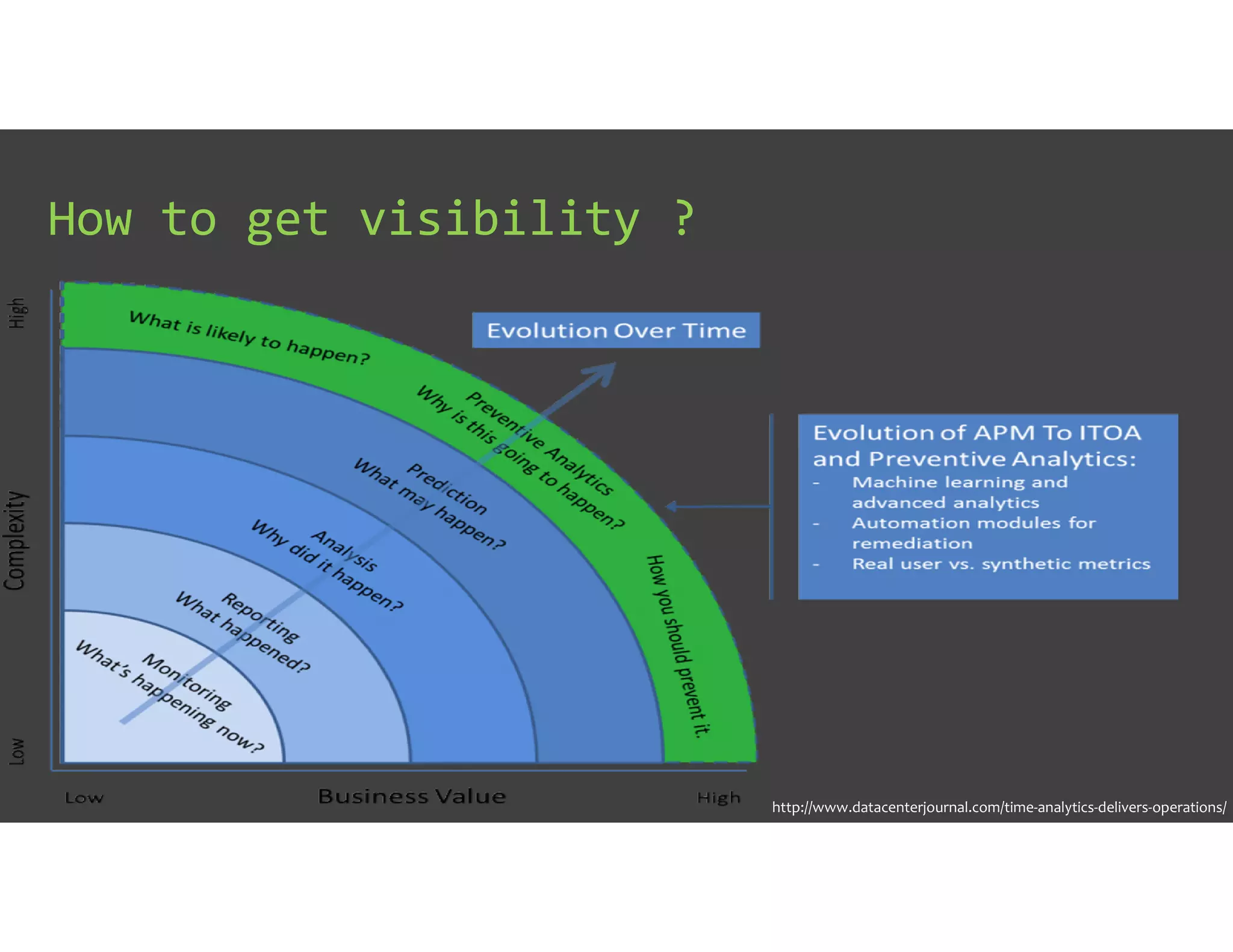
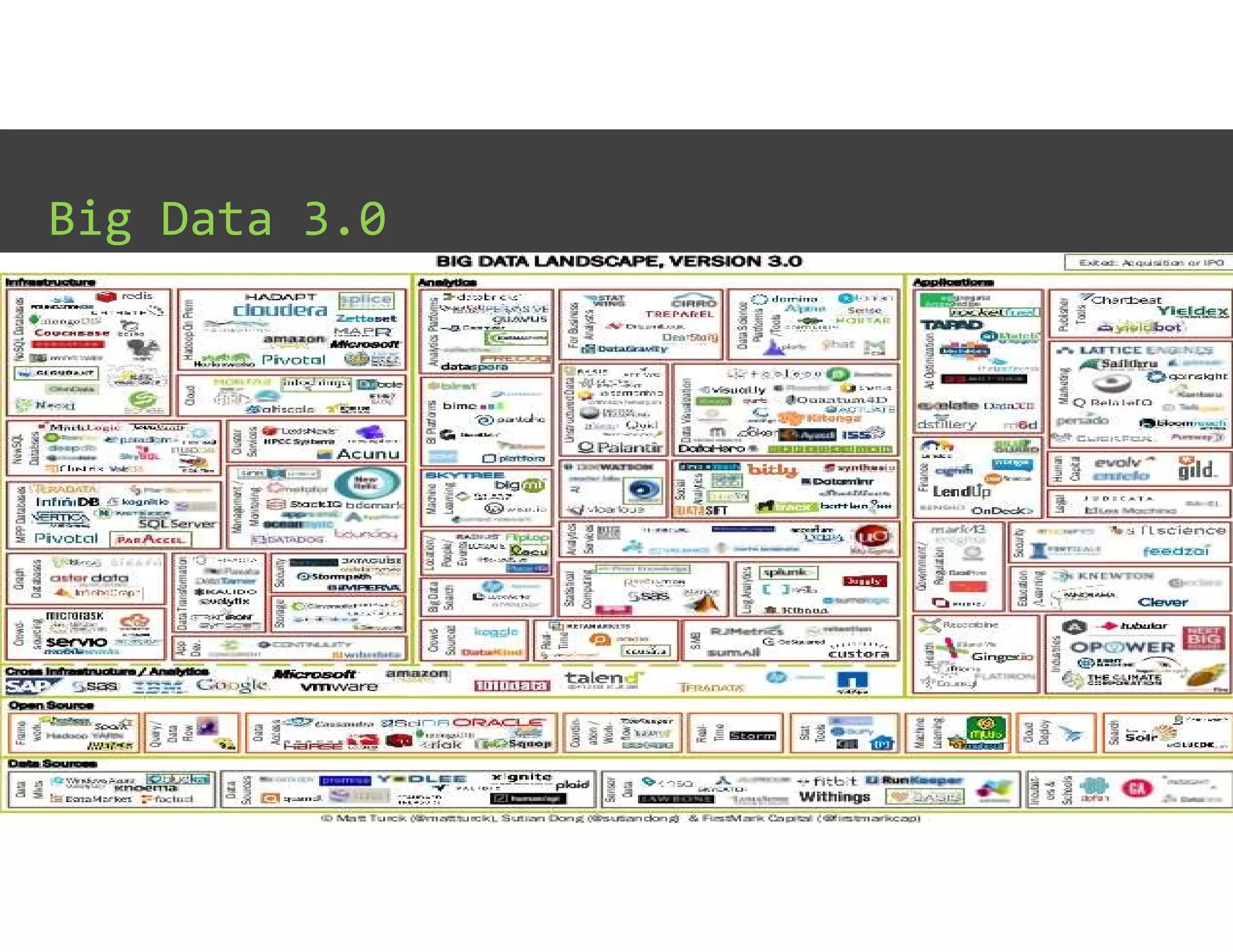
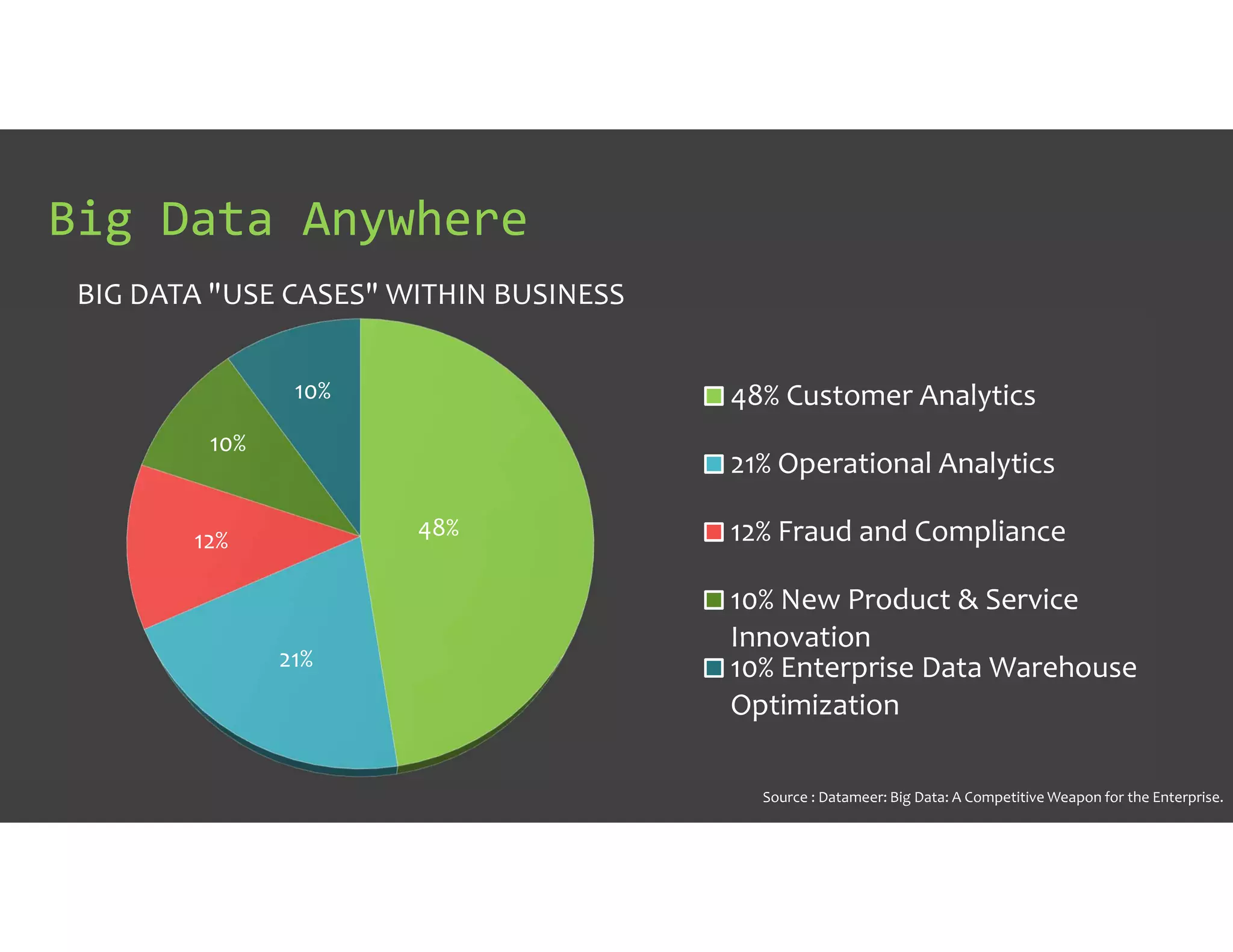
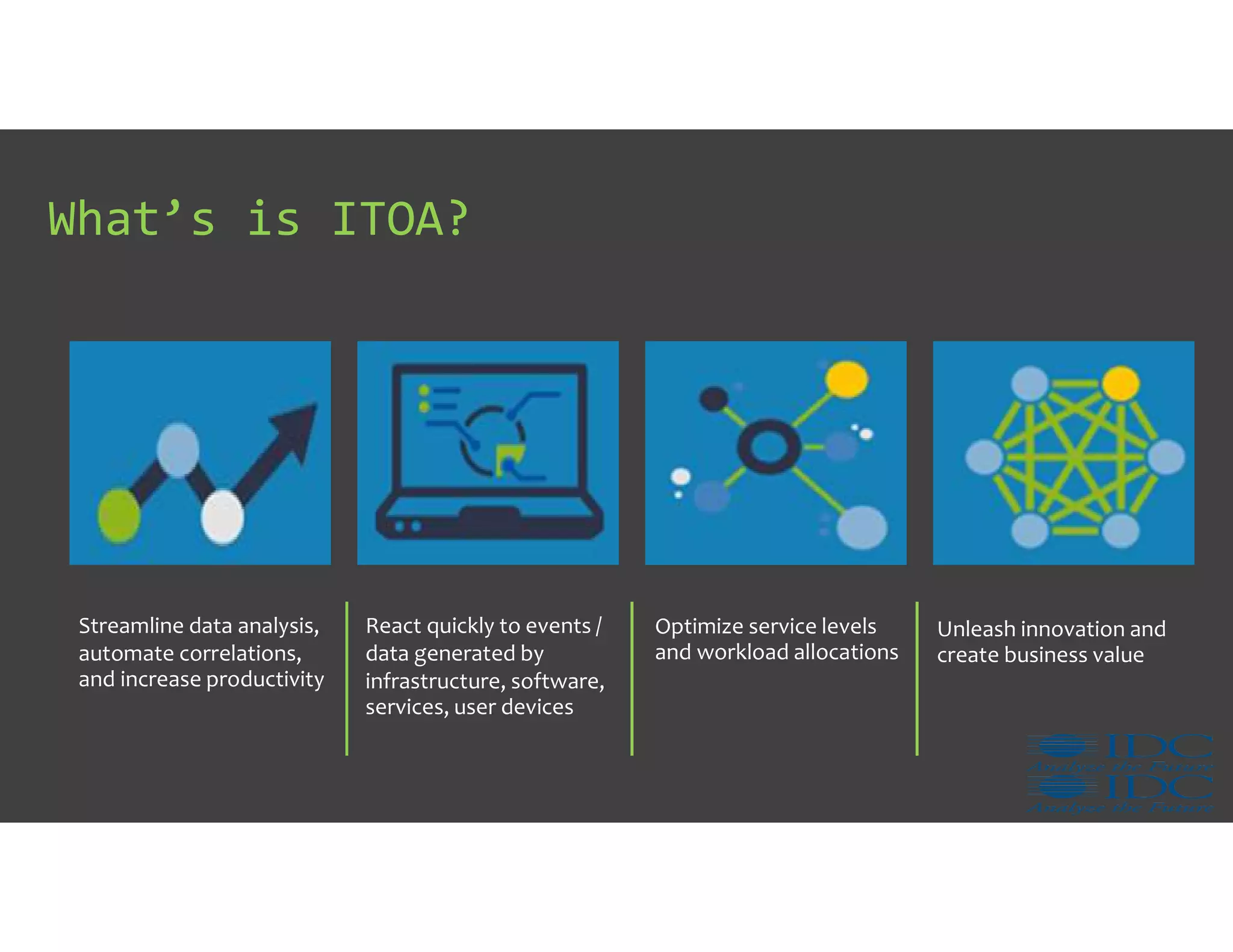
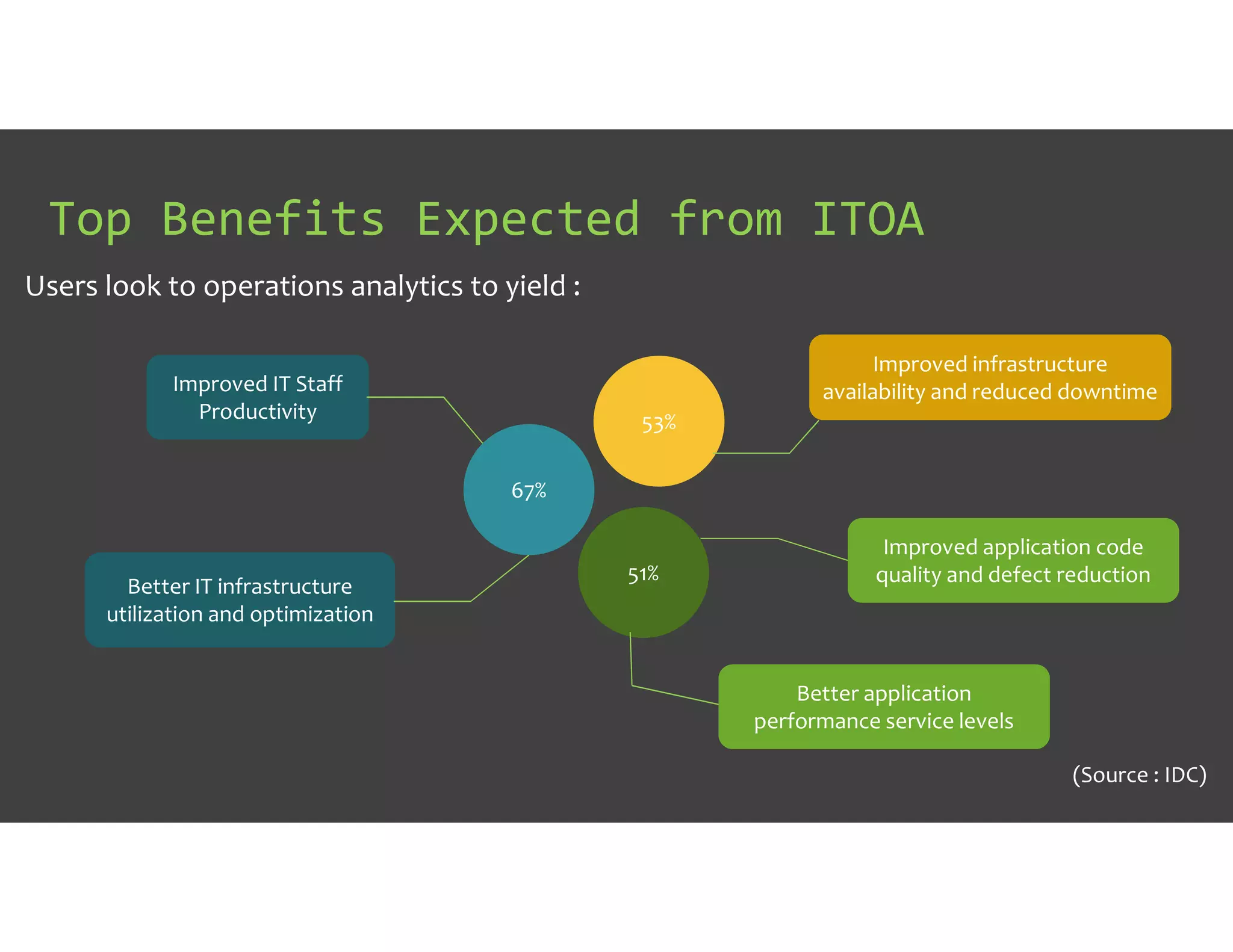
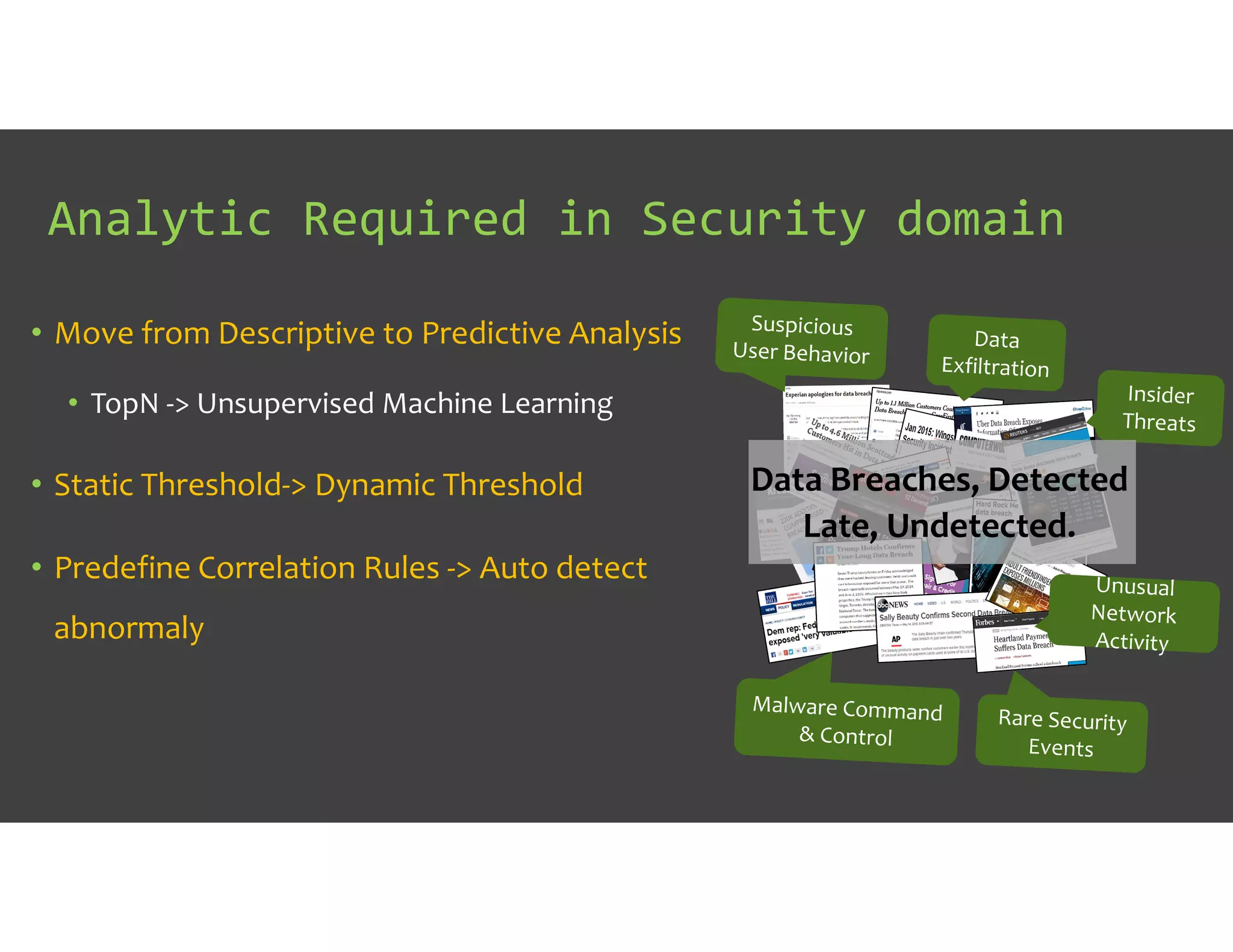
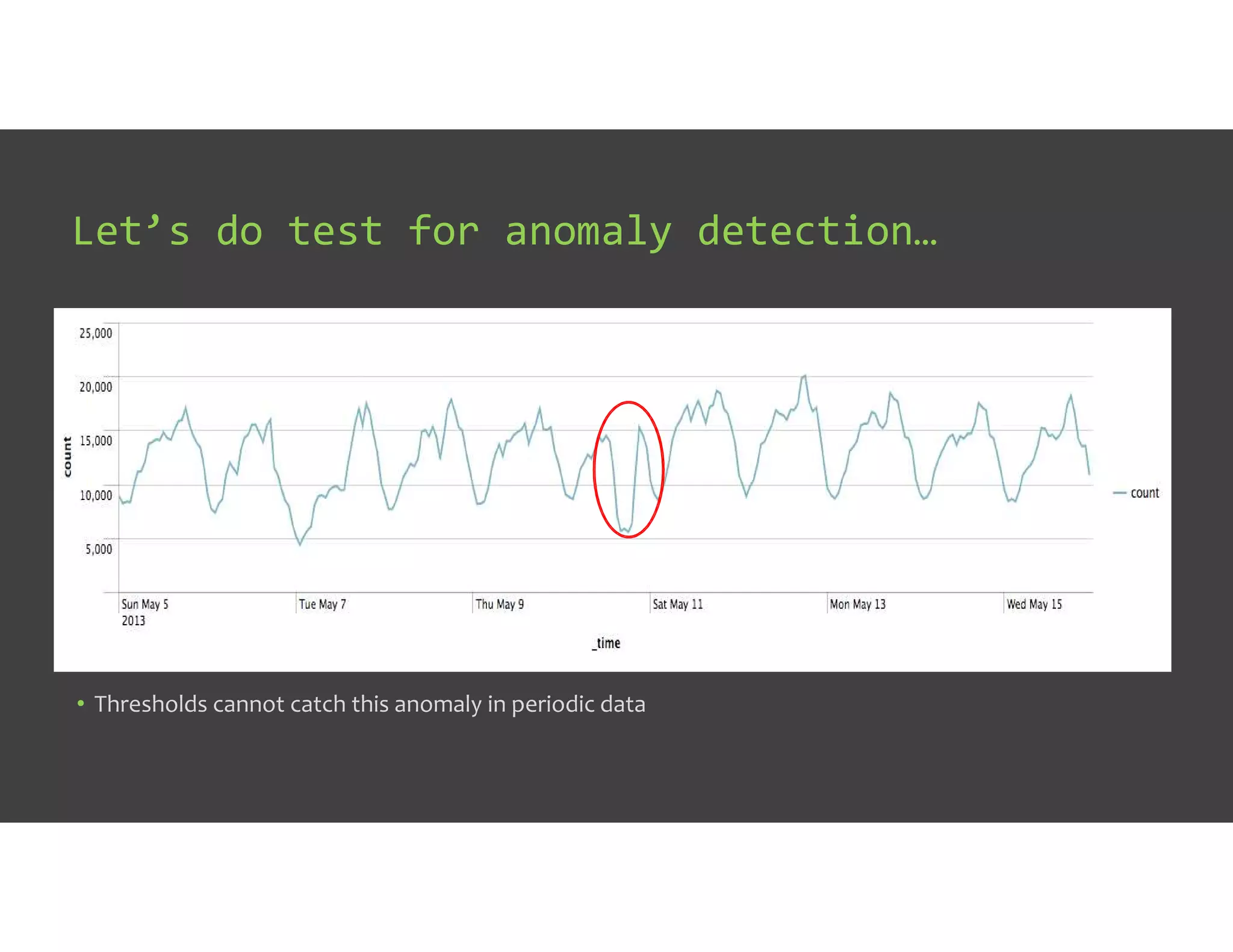
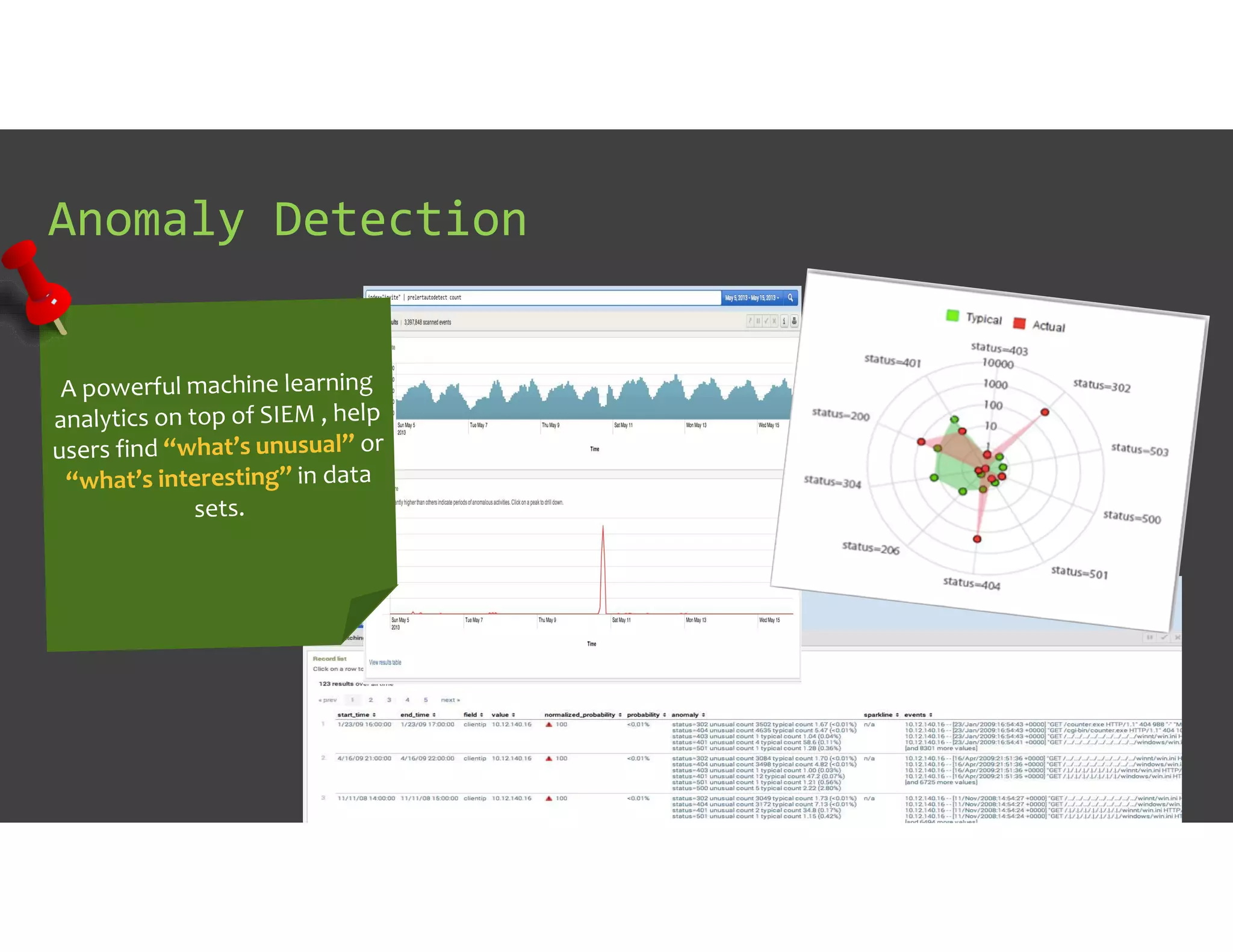
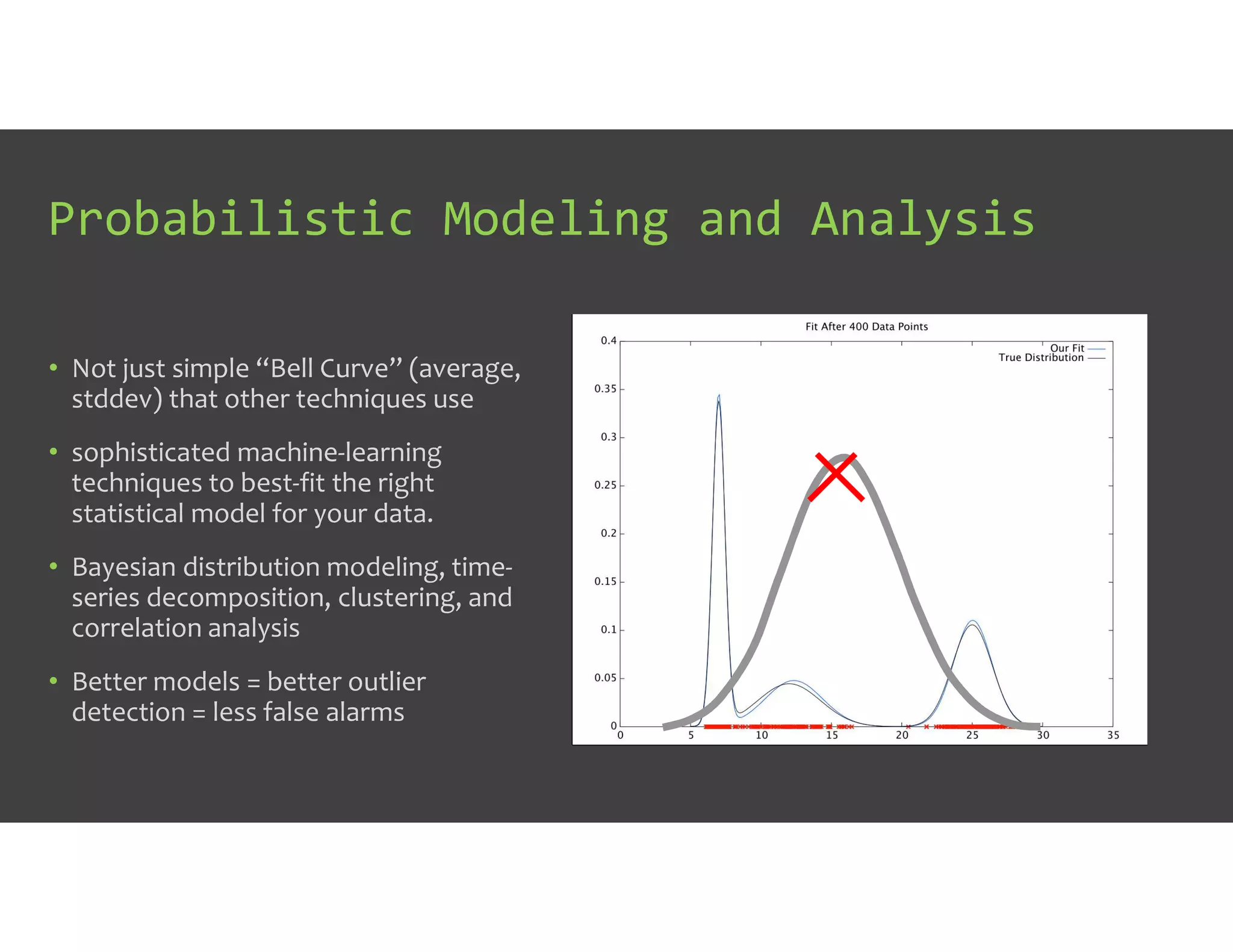
The document discusses IT Operations Analytics (ITOA) as an emerging field focusing on anomaly detection and operational intelligence in IT systems. It highlights the increasing importance of big data analytics in identifying security threats and improving operational efficiency, emphasizing the shift from descriptive to predictive analysis. The document details various use cases of ITOA in enhancing cybersecurity and reducing operational risks through advanced machine learning techniques.









![SANS: “Organizations Need To Understand Their
Environment And What Constitutes Normal And Abnormal
Behavior, Train Staff On How To Use Analytic Tools
And Define The Data They Need To Collect.”[1]
[1] Analytics and Intelligence Survey 2014, a SANS Survey, Written by David
Shackleford, October 2014 , p8.
http://www.sans.org/reading-room/whitepapers/analyst/analytics-intelligence-
survey-2014-35507
[2] http://digital-forensics.sans.org/media/poster_2014_find_evil.pdf
[2]](https://image.slidesharecdn.com/itoperationanalyticforsecurity-santisook-missconfsp1-160619142119/75/IT-Operation-Analytic-for-security-MiSSconf-sp1-32-2048.jpg)