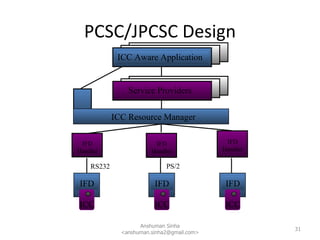
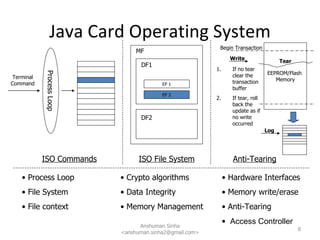
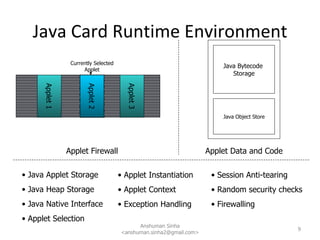
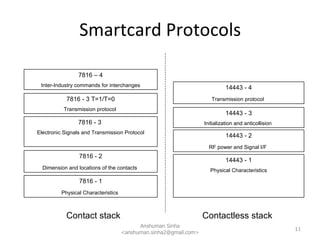
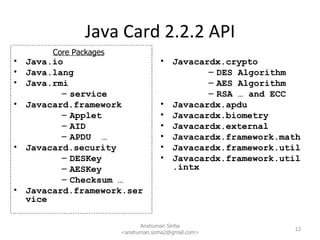
This document provides a technical overview of Java for smartcards. It discusses why Java is used for smartcards, the Java Card architecture including applets, runtime environment and global platform specifications. It also summarizes key aspects of the Java Card toolchain, development process and security features.












![Java Card Applets [1/2] Extension of javacard.framework.applet Applet has following methods … deselect() getShareableInterfaceObject(..) Install(..) Anshuman Sinha <anshuman.sinha2@gmail.com> Called by JCRE before selection of another applet . Called by JCRE on behalf of client applet to get all methods which are shared … Called by JCRE on behalf of client applet to get all methods which are shared …](https://image.slidesharecdn.com/javacard-110531204614-phpapp01/85/Technical-Overview-of-Java-Card-27-320.jpg)
![Java Card Applets [2/2] Process(APDU) Register(..) Select() SelectingApplet() Anshuman Sinha <anshuman.sinha2@gmail.com> Called by JCRE to process application specific commands Called by JCRE to process application specific commands Called by JCRE when this applet is selected Called by JCRE to return any data back to terminal while the applet is being selected](https://image.slidesharecdn.com/javacard-110531204614-phpapp01/85/Technical-Overview-of-Java-Card-28-320.jpg)